September 15, 2025
September 15, 2025 Say hello to Eternal Tux🐧, a 0-click RCE exploit against the Linux kernel from KSMBD N-Days (CVE-2023-52440 &...
September 13-14,
September 13-14, There's a sick linenoise article by @iximeow in @phrack 71 called "Learning An ISA By Force Of Will", where ixi goes from unknown binary...
September 12, 2025
September 12, 2025 Scattered Lapsus$ Hunters has provided the following message on breachforums[.]hn.They have essentially retired....

September 11, 2025
September 11, 2025 Claude "File creation" is actually a sandboxed code execution environment and has full internet access.This is great for me, since we now...
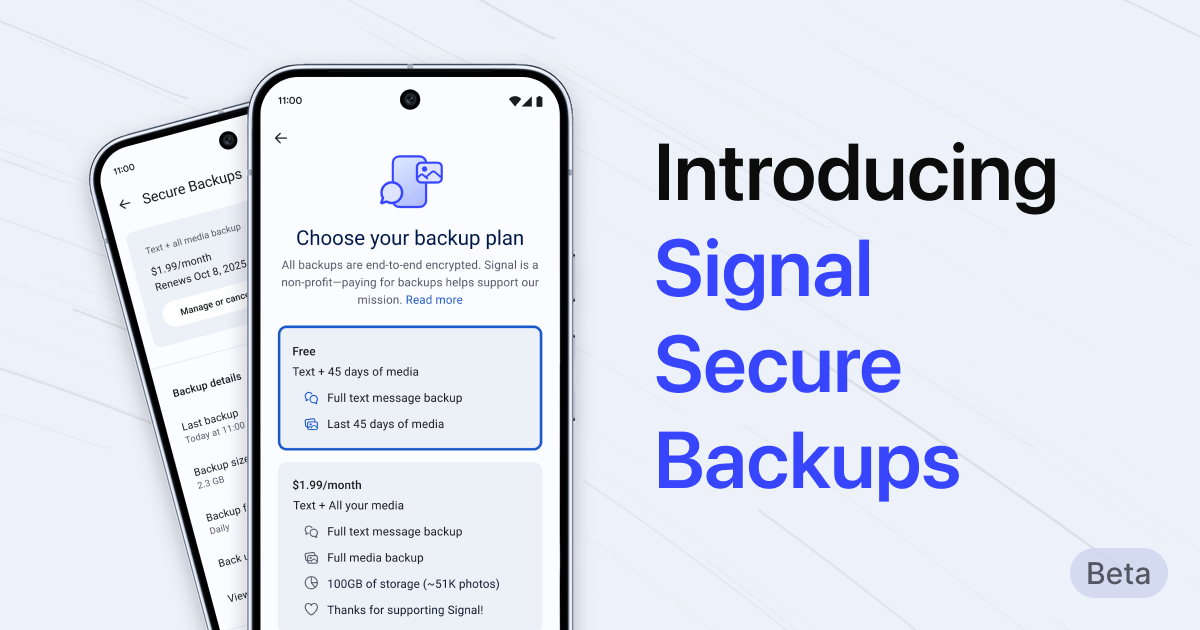
September 10, 2025
September 10, 2025 wow... great finds. good writeup, worth a read! :) and if you've ever been to burgerking drivethru, AI is analyzing your convos ;D...
September 9, 2025
September 9, 2025 Great technical writeup on how NodeZero solves Game of Active Directory (GOAD):TL;DR – How NodeZero Solved GOAD in 14 Minutes:NodeZero...

September 8, 2025
September 8, 2025 In this paper, we present CVE-GENIE, an automated, large language model (LLM)-based multi-agent framework designed to reproduce real-world...
September 7, 2025
September 7, 2025 Extensive analysis of PHRACK's "North Korea Files"🇰🇵https://t.co/xLHGlM0NyK🔥 “the most comprehensive and technically intimate disclosures”...
September 6, 2025
September 6, 2025 Did you know that we have over 50 talks from past years of CYBERWARCON available on our YouTube? Catch them here >...
September 5, 2025
September 5, 2025 🚨 Czech cybersecurity agency NÚKIB issues HIGH threat warning about data transfers to China and remote administration of technical assets...

September 4, 2025
September 4, 2025 Between Two Nerds: How threat actors are using AI to run wild - Risky Business Media The Gentlemen Hackers interviewing Halvar Flake:...
September 2-3, 2025
September 2-3, 2025 NEW: The standards of the US Telephone Security Group (TSG), to prevent phones from being turned into a listening...
September 1, 2025
September 1, 2025 Was in a bookshop and asked a worker if he could recommend books to me. He said "Sure, they're great".— Andy Ryan (@ItsAndyRyan) August 30,...

August 30–31, 2025
August 30–31, 2025 New: Tesla said it didn't have critical data in a fatal crash. Then a hacker found it. "For any reasonable person, it was obvious the data...
August 29, 2025
August 29, 2025 I'm once again looking at the epic 20-part essay which Ian Lance Taylor wrote about linkers https://t.co/DKtvyCiP6r - did anyone ever write...

August 28, 2025
August 28, 2025 #ESETResearch has discovered the first known AI-powered ransomware, which we named #PromptLock. The PromptLock malware uses the gpt-oss:20b...
August27, 2025
August27, 2025 2025 State of the Internet Report: Summary and Conclusionshttps://t.co/rmgBK1198Q(Screenshot: PolarEdge infections as of 5 August 2025)...

August 26,2025
August 26,2025 excellent writeup that highlights how many 0-days are simply asking nicely for something. https://t.co/4GZmKR2wme pic.twitter.com/QfhZfZ2bSf—...
August 25, 2025
August 25, 2025 David Gerard: "latest hilarity: Perplexity, the AI search engin…" - GSV Sleeper Servicelatest hilarity: Perplexity, the AI search engine,...
August 24, 2025
August 24, 2025 daisy-chaining wifi networks to reach a hard target is 🆆🅸🅻🅳but operational "sophistication" is often the clean up 🧹 https://t.co/fHcIv8Q3mD...