August 23, 2025
August 23, 2025 Brief info and POC for this week's Apple 0click iOS 18.6.1 RCE bug CVE-2025-43300 https://t.co/EL3qg56N8X pic.twitter.com/j8yuv1CXU7—...

August 22, 2025
August 22, 2025 AWS CEO says using AI to replace junior staff is 'Dumbest thing I've ever heard' “I think the skills that should be emphasized are how do you...
August 21, 2025
August 21, 2025 Reading G-2 "#Counterintelligence Situation in China Theater" Report from 1946. "On the purpose of collecting information from the American...
August 20, 2025
August 20, 2025 Never considered it before until now.Abuse Microsoft AI copilot to "live off the land" and perform automated malicious tasks by simply...
August 18, 2025
August 18, 2025 At @defcon, I presented my research on client-side deanonymization attacks in @Google's Privacy Sandbox! Privacy research doesn't get as much...

August 16-17, 2025
August 16-17, 2025 The previous thread glossed over how our LLM Agents actually work.The truth is, it took us a long time to figure out how to get reliable...

August 15, 2025
August 15, 2025 Russian hackers seized control of Norwegian dam, spy chief says | Russia | The GuardianBeate Gangås says attack in April by Norway’s...

August 14, 2025
August 14, 2025 NewTaiwan’s New Naval Drones Could Strike Any Chinese Invasionhttps://t.co/vBKXtTZ5A5— H I Sutton (@CovertShores) August 13, 2025 Wrapped up...
August 13, 2025
August 13, 2025 If you missed this talk at BH/DC last week, it's worth a read: "From Spoofing to Tunneling: New Red Team's Networking Techniques for Initial...

August 12, 2025
August 12, 2025 ThinkstKeeping up with security research is near impossible. ThinkstScapes helps with this. We scour through thousands of blog posts, tweets...

August 11, 2025
August 11, 2025 Phrack #72 release reveals TTPs, backdoors and targets of a Chinese/North Korean state actor mimicking KimsukyA copy of his workstation data...

August 10, 2025
August 10, 2025 You can't bug hunt your way to security. AI doesn't change that.— Sean Heelan (@seanhn) August 7, 2025...

August 9, 2025
August 9, 2025 That time when @tehjh was just reviewing a new Linux kernel feature, found a security vuln, then went on a journey to see if he could exploit...
August 8, 2025
August 8, 2025 we got a persistent 0click on ChatGPT by sharing a docthat allowed us to exfiltrate sensitive data and creds from your connectors (google...
August 7, 2025
August 7, 2025 This might be the first time the Swiss weren't able to reach a financial deal with nazis [contains quote post or other embedded content] — Sam...

August 6, 2025
August 6, 2025 https://www.usenix.org/conference/usenixsecurity25/presentation/beitis KGB Stuff by Filip Kovacevic | SubstackKGB secrets you may want to know...

August 4-5, 2025
August 4-5, 2025 ai app so good it XSSes itself pic.twitter.com/4CdK2dwQqY— PatRyk (@Patrosi73) August 3, 2025 For years I have heard that MacOS is more...

August 3, 2025
August 3, 2025 Weeks ago I shared on LinkedIn about my quick thoughts why LLMs are useful for web pentesting:“IMO why LLMs are helpful in web black box...

August 2, 2025
August 2, 2025 [2506.11060] Code Researcher: Deep Research Agent for Large Systems Code and Commit HistoryLarge Language Model (LLM)-based coding agents have...
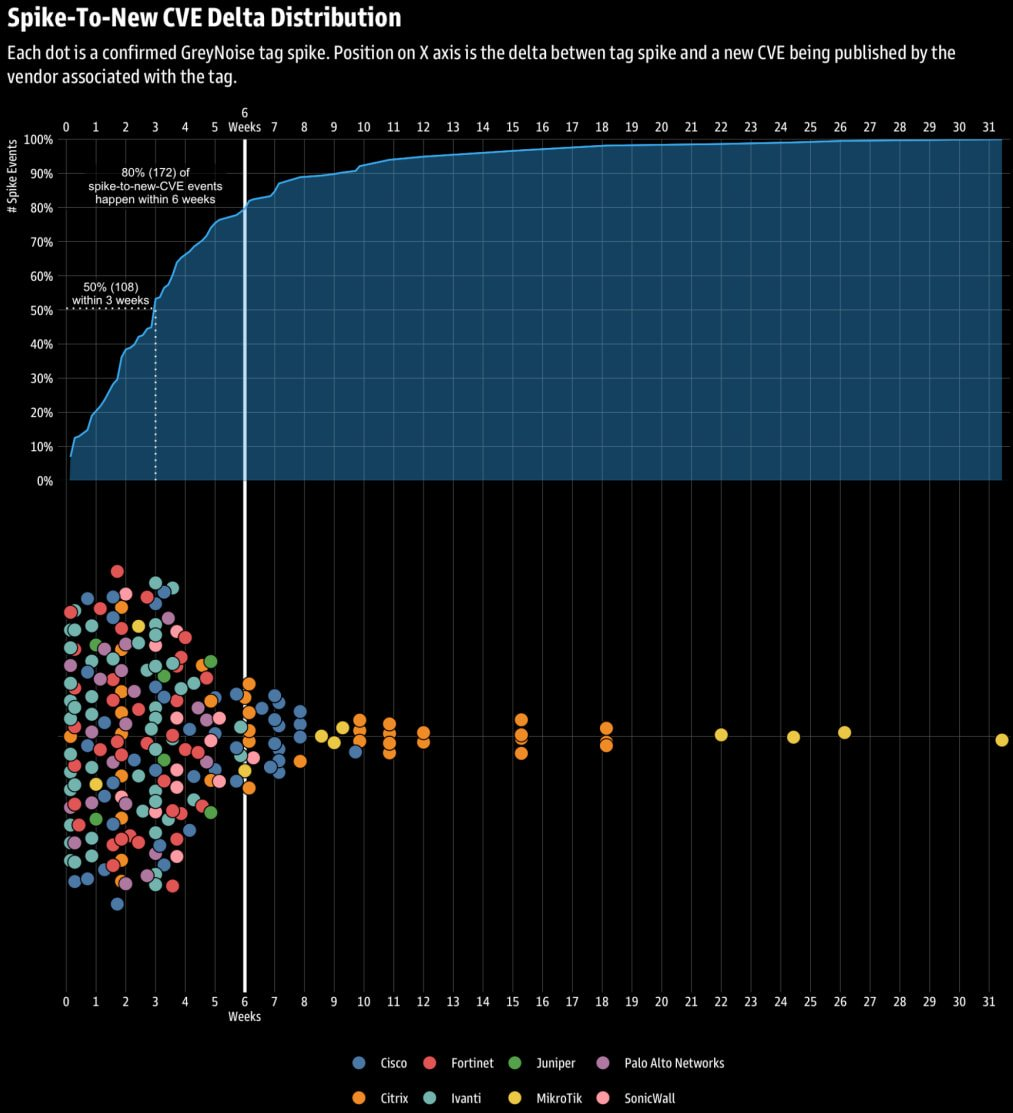
August 1, 2025
August 1, 2025 boB Rudis 🇺🇦 🇬🇱 🇨🇦: "🆕 GreyNoise Research: Early Warning Signals Befor…" - MastodonAttached: 2 images 🆕 GreyNoise Research: Early Warning...