
July 31, 2025
July 31, 2025 Interesting and detailed explanation of how smartphones can be intercepted through the vulnerabilities of the SS7 signaling...

July 30, 2025
July 30, 2025 Top Lawyer for National Security Agency Is Fired https://t.co/kMbvqM95Ml— Dr. Dan Lomas (@Sandbagger_01) July 29, 2025 from "China’s Lessons...
July 29, 2025
July 29, 2025 Terence Tao: "In the field of cybersecurity, a distinction is m…" - MathstodonIn the field of cybersecurity, a distinction is made between the...
July 28, 2025
July 28, 2025 Modern Binary Exploitation by @RPISEC. This was a university course developed and run solely by students to teach skills in vulnerability...
July 27, 2025
July 27, 2025 Just finished a new blog sharing an interesting example demonstrating the power of cross-operating system vulnerability variant analysis! Check...

July 26, 2025
July 26, 2025 It's been months since https://t.co/70znqJx6hO went down and (apparently?) lost all of its data. I have a local copy of everything(ish). I made...

July 25, 2025
July 25, 2025 https://t.co/bEGbFvtNiE pic.twitter.com/VqkRK8aaYJ— Zack Witten (@zswitten) July 24, 2025 BlackHat-MEA-2024-slides/BH MEA 2024 - Reverse...

July 24, 2025
July 24, 2025 Introducing Loki, a software obfuscation approach designed to withstand all known automated deobfuscation attacks.This method efficiently...

July 23, 2025
July 23, 2025 https://www.theregister.com/2025/07/21/replit_saastr_vibe_coding_incident/?td=rt-3a MSTIC blog on Sharepoint exploitation At least 3 actors...
July 22, 2025
July 22, 2025 The #CIA has to adjust to a world where everyone's activities and movements are being watched and stored and analysed by artificial...
July 20, 2025
July 20, 2025 101 Chrome Exploitation — Part 0: Preface We are starting a new series on modern browsers' architecture and their exploitation using Chrome as...
July 19, 2025
July 19, 2025 Very interesting view. Social media, traditional media, blogs, etc give voices to single individuals, while LLMs sample among many....

July 18, 2025
July 18, 2025 One of the very first tools/projects I released back in early 2022 looked at hosting malware via DNS records and then retrieving+reassembling....
July 17, 2025
July 17, 2025 https://t.co/b0CJjfm4eB pic.twitter.com/PhAlnlIKrI— Silas Cutler // p1nk (@silascutler) July 17, 2025 This is so much! 🔥🔥😎Found two new Potato...
July 16, 2025
July 16, 2025 Dear attacker, Clear-History does not clear the PSReadLine command history file.Clear-History, as taken from the official documentation,...

July 15, 2025
July 15, 2025 grok claims to be mechahitler and they immediately operation paperclip it lol https://t.co/W9E0jtjYQ3— sam (dependent thinker) (@CobrastanGuy)...

July 14, 2025
July 14, 2025 Intelligence Group 13, embedded within the Shahid Kaveh Cyber Group, represents one of the most operationally aggressive and ideologically...

July 13, 2025
July 13, 2025 Senate Armed Services Committee wants DOD to explore 'tactical' cyber employment | DefenseScoopA provision in the Senate Armed Services...
July 12, 2025
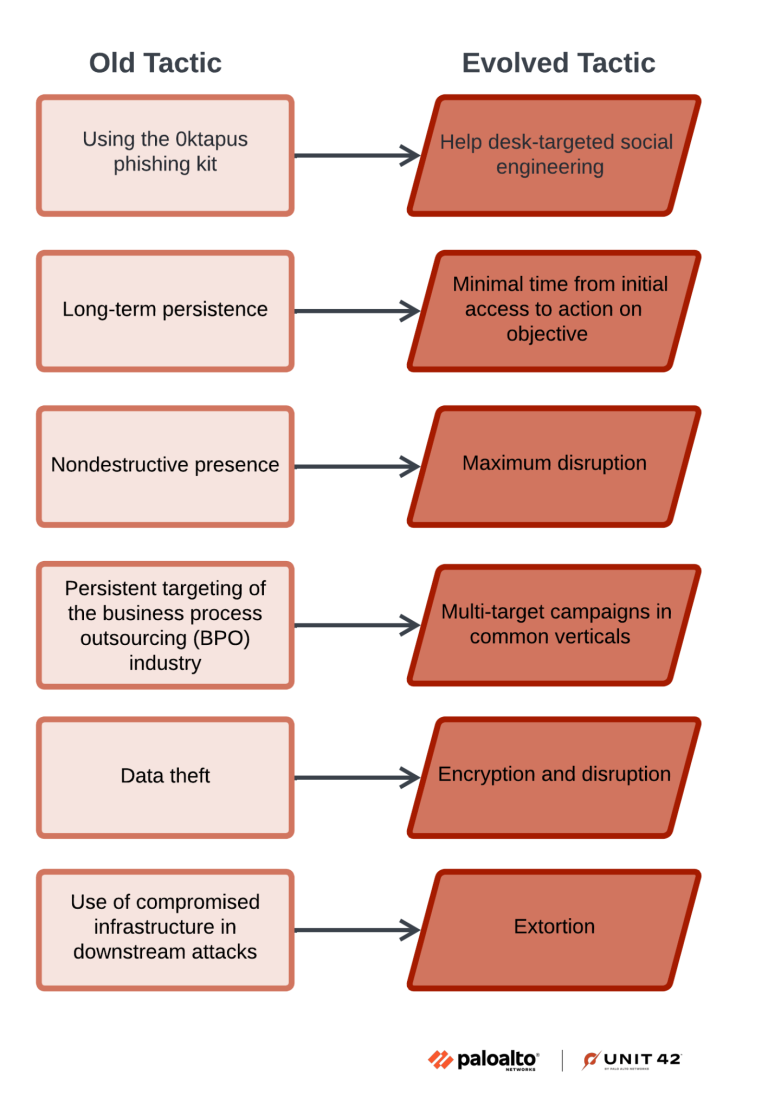
July 12, 2025 This one mostly flew below radar and media coverage, but I think is a significant case. The article refrains from directly naming the group or...

July 11, 2025
July 11, 2025 Four UK arrests in Scattered Spider incidents. Suspects are 17 to 20 years old. https://t.co/sJhfry71Tk— John Hultquist (@JohnHultquist) July...