October 8, 2025
October 8, 2025 https://t.co/VswrXw9ZjZ pic.twitter.com/mukGkzNca6— Damin Toell (@damintoell) October 7, 2025 POChttps://t.co/6VziQNQ76p...
October 7, 2025
October 7, 2025 This was an interesting read, but to their credit, I was expecting a bit wider coverage. The coverage of IO in sync with kinetic strikes is...
October 5-6, 2025
October 5-6, 2025 GitHub - b1n4r1b01/n-daysContribute to b1n4r1b01/n-days development by creating an account on GitHub. GitHub - stealth/crash: crypted admin...
October 3-4, 2025
October 3-4, 2025 There is someone exposing IRGC (Islamic Revolutionary Guard Corps) stuff on GitHub.I'm not a IRGC geopolitical nerd, so I can't assess the...
October 2, 2025
October 2, 2025 Most #CyberSecurity classes focus on Western technology stacks, fueling #APT groups with TTPs to ravage our own networks. We are flipping the...
October 1, 2025
October 1, 2025 Pre-pandemic, the calculus was what the likelihood was of an employee being bribed to insert a USB stick into their work computer at the...
September 30, 2025
September 30, 2025 Just uploaded my RomHack slides about attack vectors against PsSetLoadImageNotifyRoutine and drivers that rely on it....
September 29, 2025
September 29, 2025 Writeup for CVE-2025-24085, an ITW mediaplaybackd vulnerability patched earlier this year https://t.co/XopOVNmfnc— binaryboy (@b1n4r1b01)...
September 28, 2025
September 28, 2025 Check out Titanis, my new C#-based protocol library! It features implementations of SMB and various Windows RPC protocols along with...
September 27, 2025
September 27, 2025 Precisely this: 👇Understanding how something is built helps you understand how it can break. The best way to understand how something is...
September 26, 2025
September 26, 2025 In 2016 Geoffrey Hinton said “we should stop training radiologists now" since AI would soon be better at their jobs.He was right: models...

September 25, 2025
September 25, 2025 We are releasing details on BRICKSTORM malware activity, a China-based threat hitting US tech to potentially target downstream customers...

September 24, 2025
September 24, 2025 A very special between two nerds… Between Two Nerds: How the US can win the cyber war - Risky Business Media OPSEC fails that beggar...
September 23, 2025
September 23, 2025 Poland’s deputy prime minister said that if Poland were hit by a cyberattack on critical infrastructure such as energy or water with broad...
September 22, 2025
September 22, 2025 this was a googlectf challenge btw https://t.co/tC2yYC09At pic.twitter.com/FzaRuBAaWX— Rebane (@rebane2001) September 21, 2025 Thorough...
September 21, 2025
September 21, 2025 Just published some notes on httpjail - this is a really interesting new sandboxing project, it lets you run a process (on macOS or Linux...
September 20, 2025
September 20, 2025 The vast majority of hacking is just credentials. There are four basic ways to get creds:STABSteal: using malware, etc.Try: brute force,...
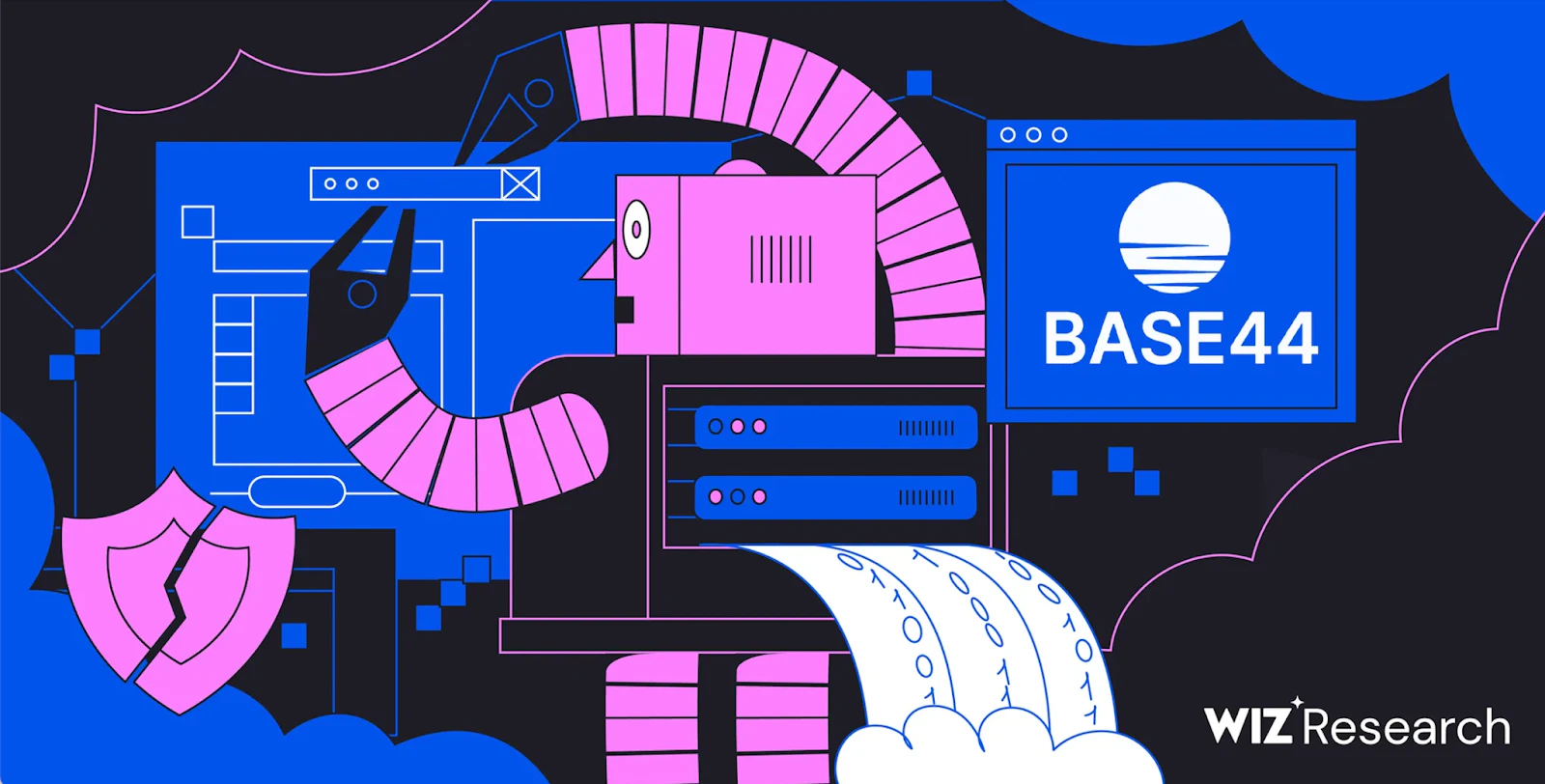
September 18-19, 2025
September 18-19, 2025 I've been researching the Microsoft cloud for almost 7 years now. A few months ago that research resulted in the most impactful...

September 17, 2025
September 17, 2025 Quite a good Between Two Nerds discussion. Between Two Nerds: The limits of cyber power - Risky Business Media OpenAI literally just...
September 16, 2025
September 16, 2025 When we decompile an APK and see an unreadable https://t.co/BbQf3H943H.bundle, it could be Hermes bytecode. Using https://t.co/DBonMwpUBM...