this week in security — june 2 edition
|MC_PREVIEW_TEXT|
** ~this week in security~
a cybersecurity newsletter by @zackwhittaker (https://twitter.com/zackwhittaker)
volume 2, issue 21.
View this email in your browser (|ARCHIVE|) ~ ~
** THIS WEEK, TL;DR
US Universities Are Funding The Tech Behind China’s Surveillance State (https://www.buzzfeednews.com/article/ryanmac/us-money-funding-facial-recognition-sensetime-megvii?%3Fbftw=world) BuzzFeed News: This was a great long read about how U.S. universities and retirees are inadvertently bankrolling the surveillance systems built by SenseTime and Megvii, which are being used in Beijing’s horrific “reeducation” effort of the Uyghur ethnic minority. Duke University, Michigan University, and Princeton University are among those names. @RMac18 (https://twitter.com/RMac18/status/1134158898951204864) , one of the authors, described how many of the institutions tried to absolve themselves of blame because they invested with venture firms who invested in companies profiling ethnic groups. As he noted, that’s not how it works! Great work by BuzzFeed. More: @dtbyler tweet thread (https://twitter.com/dtbyler/status/1134174470770323456) | @RMac18 tweet thread (https://twitter.com/RMac18/status/1134158898951204864)
Flipboard Says Hackers Hit Twice, Went Undetected For Nine Months (https://about.flipboard.com/support-information-incident-May-2019/) Flipboard: For nine months between June 2, 2018 and March 23, 2019 and a second time on April 21-22, 2019, hackers had gained access to Flipboard’s systems. The hackers stole usernames, hashed password and email addresses. Passwords before March 2012 were scrambled using SHA-1, which isn’t bad for the time, but were later scrambled with bcrypt. The social network and news sharing site still reset the passwords on millions of accounts to be safe. Third-party tokens were also accessed and later invalidated. More: TechCrunch (https://techcrunch.com/2019/05/28/flipboard-hacks-password-resets/) | ZDNet (https://www.zdnet.com/article/flipboard-says-hackers-stole-user-details/)
Russian Hackers Sell Sensitive Stolen Passport and Bank Account Data (LINK) BBC News: Here’s an interesting read: BBC reporters looked at Russian hackers who steal and sell sensitive personal data, like passport and bank account data. The hackers in some cases obtained data from state agencies. “Russia stands out for the ease with which an ordinary person can obtain secret data held by state agencies,” wrote the reporters. They were even able to obtain their mobile phone records, including their geolocation. Related: BBC News (https://www.bbc.com/news/technology-48147515)
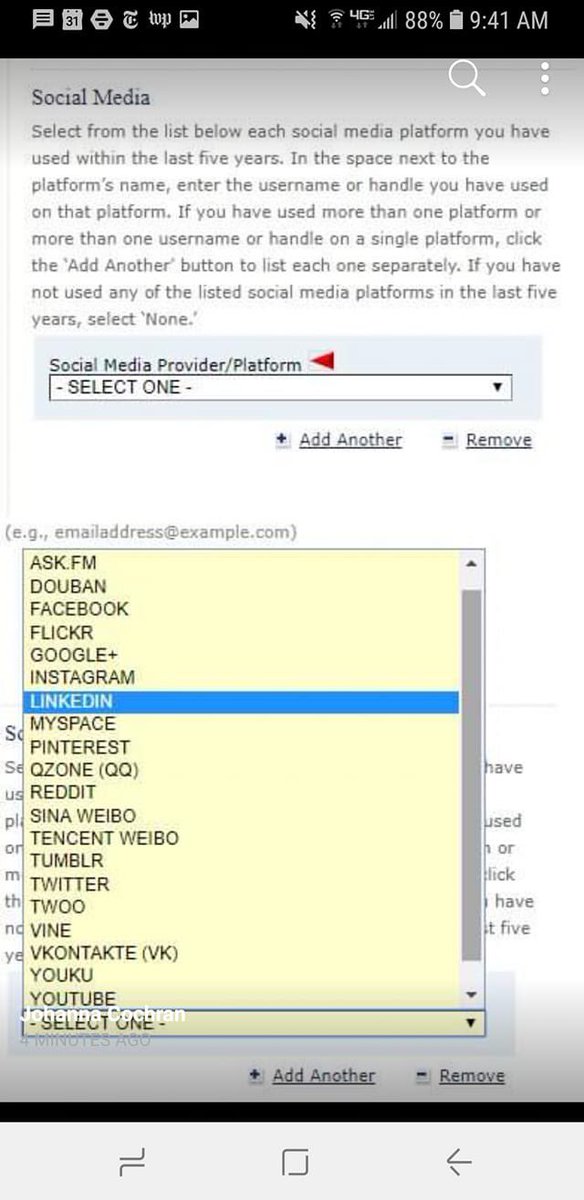
U.S. Now Seeks Social Media Handles From All Visa Applicants (https://www.apnews.com/c96a215355b242e58107c2125c18fc4a) Associated Press: We all knew this was coming (https://www.zdnet.com/article/us-visa-applicants-must-now-provide-social-media-handles/) and now it has. The U.S. government now wants visa applicants to list their social media handles over the past five years. It’s expected to affect about 15 million applicants each year. According to the BBC, anyone who lies about their social media use may face “serious immigration consequences.” Good job I already have my green card — otherwise all the government would see are cat pics and mild shitposting. But critics say this would force many to self-censor their social media presence. Archive: ZDNet (https://www.zdnet.com/article/us-visa-applicants-must-now-provide-social-media-handles/) | More: BBC News (https://www.bbc.com/news/world-us-canada-48486672)
Chinese Database Exposes 42.5M Records From Dating Apps (https://www.cyberscoop.com/chinese-database-42-million-records/) Cyberscoop: Tens of millions of user records from different dating apps have been discovered in a single unprotected database that didn’t include any password protection, according to new research findings (via Cyberscoop). That includes IP addresses and geolocation data, age, account names, and more. Many were from the U.S., the U.K. and Canada. Little else is known about the database — only that it’s located in China. More: Security Discovery (https://securitydiscovery.com/chinese-dating-apps/)
Tech Giants Condemn GCHQ Plans To Listen In On Encrypted Chats (https://techcrunch.com/2019/05/30/apple-google-microsoft-whatsapp-sign-open-letter-condemning-gchq-proposal-to-listen-in-on-encrypted-chats/) TechCrunch: Apple, Google, Microsoft, and WhatsApp are among several companies who’ve signed on to an open letter criticizing GCHQ’s plans to effectively copy itself on encrypted chat messages like a ghost in your encrypted chats. The coalition said the access would “introduce potential unintentional vulnerabilities, and increase risks that communications systems could be abused or misused.” It follows the GCHQ proposal (https://techcrunch.com/2018/11/30/gchqs-not-so-smart-idea-to-spy-on-encrypted-messaging-apps-is-branded-absolute-madness/) six months ago which were quickly derided as being pretty darn silly. Archive: TechCrunch (https://techcrunch.com/2018/11/30/gchqs-not-so-smart-idea-to-spy-on-encrypted-messaging-apps-is-branded-absolute-madness/) | Lawfare (https://www.lawfareblog.com/principles-more-informed-exceptional-access-debate)
DuckDuckGo CEO: We Should Opt-In To Data Tracking, Not Opt-Out (https://www.vox.com/recode/2019/5/27/18639284/duckduckgo-gabe-weinberg-do-not-track-privacy-legislation-kara-swisher-decode-podcast-interview) Recode/Vox: This was an interesting interview with privacy-minded search engine DuckDuckGo’s chief executive Gabe Weinberg, who said lobbying was partly to blame for the advertising and tracking model. “I would love it to be opt in by default, but in a realistic way, I think if it was operationalized as a way to opt out, I think that would be effective because, as you said before, the other argument is some people don’t care, and that gives people, really, the choice.” It’s an interesting interview, that’s for sure. More: Podcast (https://megaphone.link/VMP8291192781)
Google Is Finally Making Chrome Extensions More Secure (https://www.wired.com/story/google-chrome-extensions-security-changes/) Wired ($): Amid the furore about Chrome soon to block restrict ad blockers (https://www.vice.com/en_us/article/evy53j/google-struggles-to-justify-making-chrome-ad-blockers-worse) , Google said it’s hoping to make Chrome extensions more privacy minded and safer. In a blog post (https://blog.google/technology/safety-security/update-project-strobe-new-policies-chrome-and-drive/) , Google said it’s trying to make extensions more trustworthy by limiting their permissions to access only “the appropriate data needed to implement their features.” The policy will be rolled out later this year. More: Google Blog (https://blog.google/technology/safety-security/update-project-strobe-new-policies-chrome-and-drive/)
NSA Says Sysadmins To Blame For Not Patching Against EternalBlue (https://www.cyberscoop.com/eternal-blue-baltimore-ransomware-rob-joyce-new-york-times/) Cyberscoop: So… you probably saw “that” (https://www.nytimes.com/2019/05/25/us/nsa-hacking-tool-baltimore.htm) New York Times story about EternalBlue hitting Baltimore with Robbinhood ransomware. It’s under dispute by many. But what’s kind interesting is where the blame lies. Two years on after the NSA’s hacking tools were stolen and posted online — if you still haven’t patched, a lot of the blame rests on you. Not all, but a lot. NSA’s Rob Joyce also noted this but didn’t exactly explicitly say if the tools used in the attack were from his organization — obviously. More: @Bing_Chris tweets (https://twitter.com/Bing_Chris/status/1134157061191884805) | @dnvolz tweets (https://twitter.com/dnvolz/status/1134117575829463040) | Bleeping Computer (https://www.bleepingcomputer.com/news/security/a-closer-look-at-the-robbinhood-ransomware/) ~ ~
** THE STUFF YOU MIGHT’VE MISSED
Hackers are exploiting a WordPress plugin to send visitors to bad sites (https://arstechnica.com/information-technology/2019/05/hackers-actively-exploit-wordpress-plugin-flaw-to-send-visitors-to-bad-sites/) Ars Technica: A security flaw in WP Live Chat Support, a popular plugin for WordPress with more than 50,000 active installations, fell victim to a cross-site scripting bug that allowed hackers to inject malicious JavaScript to redirect users to malicious pages. Zscaler wrote more about its findings (https://www.zscaler.com/blogs/research/malicious-javascript-injected-wordpress-sites-using-latest-plugin-vulnerability) in a blog post. The patched version for this vulnerability was released on May 16, said Prakhar Shrotriya (https://twitter.com/prakhar0x53) .
Over 100 Checkers restaurants hit by PoS malware (https://threatpost.com/pos-malware-found-at-102-checkers-restaurant-locations/145181/) Threatpost: In total, 102 Checkers and Rally restaurants in 20 states were affected by point-of-sale malware. Some of the infections date back to 2015! You can check out the affected list of restaurants here (https://www.checkers.com/security-issue/#affected-stores) . Checkers said in a statement (https://www.checkers.com/security-issue/) that the data stolen included “cardholder name, payment card number, card verification code and expiration date.” Ouch.
Here’s all the ways Google tracks you and how to stop it (https://www.wired.com/story/google-tracks-you-privacy/) Wired ($): This was a pretty comprehensive read — digging into the many devices, apps and services that Google offers. It knows what you buy, where you go, and what you search for online. If you want to lock down what Google learns and stores about you, this is a pretty good place to start.
ICRC releases report on the human cost of cyber operations (https://blogs.icrc.org/law-and-policy/2019/05/29/potential-human-costs-cyber-operations-key-icrc-takeaways-discussion-tech-experts/) International Committee of the Red Cross: ICRC has released a report on how humans are affected by cyber operations. That includes the cost, supply chains, the cost on healthcare, and industrial control systems — and crucially, how to move forwards. For many, the interesting aspects are about cyber operations — from armed conflicts to ransomware — have on society. @lukolejnik (https://twitter.com/lukolejnik) , who co-authored the paper, had a tweet thread (https://twitter.com/lukolejnik/status/1133659743824822273?s=21) on the takeaways.
What I learned trying to secure congressional campaigns (https://idlewords.com/2019/05/what_i_learned_trying_to_secure_congressional_campaigns.htm) Maciej Ceglowski: Ceglowski was part of an effort between 2017 and 2018 to deliver campaign security training to dozen of congressional campaigns to keep their staff and families “safe from people trying to break into social media, read their email, or wire their campaign war chest to Nauru.” Well it’s not as simple as handing out Yubikeys — in fact, they’re still a huge stumbling block, even though they’re absolutely necessary. This was a really interesting read — and insightful.
Australian Police can snoop on public Wi-Fi customers (https://www.theguardian.com/business/2019/may/28/spies-with-that-police-can-snoop-on-mcdonalds-and-westfield-wifi-customers) The Guardian: From the “we warned you (https://twitter.com/mehreenfaruqi/status/1133268781893992448) this would happen” department. Thanks to a new surveillance and anti-encryption legislation rushed through parliament last year, police are now allowed to snoop on public Wi-Fi hotspots by forcing providers to turn over their logs — which wasn’t even considered possible under the draft proposals. One Green MP criticized (https://twitter.com/RohanLeppert/status/1133582754870751232) the opposition Labor party for buckling under pressure (https://techcrunch.com/2018/12/05/australia-rushes-its-dangerous-anti-encryption-bill-into-parliament/) to get the bill passed. The government effectively said if you don’t support the bill, you want the terrorists and child abusers to win. Absolutely nuts.
Docker bug allowed root access to the host file system (https://duo.com/decipher/docker-bug-allows-root-access-to-host-file-system) Duo: Definitely one to keep an eye on — a fix is in the works. All Docker versions have a flaw that allows an attacker to get read-write access to any path on the host server. “If an attacker can add a symlink component to the path after the resolution but before it is operated on, then you could end up resolving the symlink path component on the host as root. In the case of ‘docker cp’ this gives you read and write access to any path on the host,” said Aleksa Sarai (https://seclists.org/oss-sec/2019/q2/131) in a Full Disclosure posting.
Building Facebook’s service encryption infrastructure (https://code.fb.com/security/service-encryption/) Facebook: The social media giant penned a blog post about how it runs its encryption infrastructure at scale, a “complex job that requires thoughtful consideration of tradeoffs between performance, security, and operability.” ~ ~
** OTHER NEWSY NUGGETS
Amazon defeated Rekognition revolt by a large margin (https://www.bbc.com/news/technology-48422321) The shareholder proposal to demand that Amazon stop selling its facial recognition technology to police, law enforcement and government customers failed last week. It turns out, following the release of the shareholder votes, that only 3 percent voted for it, per a filing (https://ir.aboutamazon.com/node/33336/html) with the SEC. It needed 5 percent to be reintroduced. It’s not surprising given Amazon CEO Jeff Bezos has about as much voting rights as the four largest external shareholders combined. It was doomed to fail (https://techcrunch.com/2019/05/28/amazon-facial-recognition-vote/) by math alone.
A comprehensive analysis of CVE-2019-0708, the RDP bug “BlueKeep” (https://www.thezdi.com/blog/2019/5/27/cve-2019-0708-a-comprehensive-analysis-of-a-remote-desktop-services-vulnerability) Here’s pretty much everything you need to know about the wormable BlueKeep. Microsoft released patches for Windows XP and later earlier this month and continues to sound the alarm about patching now there’s a working denial-of-service (https://www.zdnet.com/article/microsoft-issues-second-warning-about-patching-bluekeep-as-poc-code-goes-public/) proof-of-concept exploit going around. One more step and we’ll see full remote code execution. There are about one million (https://blog.erratasec.com/2019/05/almost-one-million-vulnerable-to.html) devices at risk of the flaw — not including what’s on a network connected to the internet-facing server.
So running ‘rdpscan’ on the entire Internet gives the following preliminary results. It’s 826,912 confirmed vulnerable systems on the Internet, though many of those “UNKNOWN” are transient errors, meaning the likely number is closer to 900k.
DHS assessment of foreign VPN apps finds security risk real (https://www.cyberscoop.com/dhs-mobile-vpn-apps-chris-krebs-ron-wyden/) From @snlyngaas (https://twitter.com/snlyngaas) : Homeland Security says there’s a risk to using foreign VPN services, but a lack of data makes the risk as of yet unquantifiable. “There is no indication that foreign-made apps are widely used in the U.S. government, and there may not be any government-operated devices that have downloaded foreign VPN apps,” according to Homeland Security chief cyber-bod Chris Krebs (https://twitter.com/CISAKrebs) .
First U.S. public schools will soon pilot facial recognition (https://www.buzzfeednews.com/article/daveyalba/lockport-schools-facial-recognition-pilot-aegis?bftwnews&utm_term=4ldqpgc#4ldqpgc) A public school district of eight schools in western New York was due to become the first U.S. public school to pilot facial recognition. The district was told by the NY State Education Department, however, to delay its introduction. The system will track sex offenders and those who’ve been suspended from school, as well as an array of weaponry, apparently.
Researcher reveals a stealthy new macOS Keychain attack (https://www.wired.com/story/keysteal-apple-keychain-attack-shenanigans/) Linus Henze earlier this year demonstrated a new Keychain bug (https://www.youtube.com/watch?v=nYTBZ9iPqsU&feature=youtu.be) in a video but declined to tell Apple because the company doesn’t have a bug bounty for Macs. Fair enough. He’s now revealed more about the bug. It requires local access, but it’s still pretty dangerous. Henze said it’s possible to trick macOS’ messaging system into funneling the decrypted contents of the Keychain into an app he controlled, thus stealing sensitive passwords, private keys, credit card numbers and more.
An ID Scanner Company is Collecting Sensitive Data on Millions of Bargoers (https://onezero.medium.com/id-at-the-door-meet-the-security-company-building-an-international-database-of-banned-bar-patrons-7c6d4b236fc3) “PatronScan says it sells security. Privacy advocates worry it’s selling mass surveillance,” said the Medium post. Well no shit. Apparently the system has more than 40,000 banned customers, which it regularly shares with police. It’s already been billed as a terrible idea by privacy activists (https://twitter.com/evacide/status/1133814507543732225) . ~ ~
** THE HAPPY CORNER
Here are some of the good things from the week:
Thanks to @natfriedman (https://twitter.com/natfriedman/status/1133734203680595968) for tweeting this: GitHub will now enable automatic security updates for known-flawed open source dependencies, so hopefully — fingers crossed — there’ll be no more supply-chain or third-party library attacks on your apps.
@BadassBowden (https://twitter.com/BadassBowden/status/1132663671962972164) has an excellent tweet-thread on how to conduct OSINT, or open-source intelligence. It’s a really good basic read from a serious professional. A great starting point for future OSINT’ers.
I know the Chrome team has faced a bit of backlash this week because of the aforementioned ad-blocker policies coming into effect, but take a moment (https://twitter.com/ericlaw/status/1093292363194208256) to appreciate how quickly the team pushed through this bug fix. It took about 10 hours to fix a bug from @ericlaw (https://twitter.com/ericlaw/) ‘s discovery to a patch landing in the master branch. Pretty impressive.
And one final mini-victory for anyone who uses AP style. Crypto means cryptography! Thanks to @gregotto (https://twitter.com/gregotto/status/1133766161793990658) for flagging. The world is a better place now. If you want to nominate some good news from the week, feel free to reach out: zack.whittaker@gmail.com (mailto:zack.whittaker@gmail.com?subject=Newsletter%20Happy%20Place) . ~ ~
** THIS WEEK’S CYBER CAT
This week’s cybercat is Sniper. He lost an eye when he was a kitten but still doesn’t let the cyber-threats slip by. What an absolutely badass kitty. Many thanks to Sniper’s human, Charles Humphrey, for the submission. (You may need to enable images in this email.) Don’t forget to send in your cybercats! They will always get featured. The more, the merrier. You can submit your cybercats here (mailto:zack.whittaker@gmail.com?subject=Cyber%20Cat%20submission&body=Please%20include%20a%20JPG%20of%20your%20cyber%20cat%2C%20their%20name%2C%20and%20also%20your%20name%20and%20Twitter%20handle%20if%20you%20want%20credit.%20) . ~ ~
** SUGGESTION BOX
That’s all for this week — a very busy one. This newsletter’s suggestion box (https://docs.google.com/forms/d/e/1FAIpQLSebkpf8z8TvMJoixuSzmrR-CTLcOv_ufF7voso1HZBI_f5zrw/viewform) is always open for feedback. I’ll be back next Sunday. Have a good week! ~ ~
============================================================ (http://twitter.com/intent/tweet?text=|URL:MC_SUBJECT|: |URL:ARCHIVE_LINK_SHORT|) Tweet (http://twitter.com/intent/tweet?text=|URL:MC_SUBJECT|: |URL:ARCHIVE_LINK_SHORT|) (http://www.facebook.com/sharer/sharer.php?u=|URL:ARCHIVE_LINK_SHORT|) Share (http://www.facebook.com/sharer/sharer.php?u=|URL:ARCHIVE_LINK_SHORT|) (|FORWARD|) Forward (|FORWARD|)
This email was sent to |EMAIL| (mailto:|EMAIL|) why did I get this? (|ABOUT_LIST|) unsubscribe from this list (|UNSUB|) update subscription preferences (|UPDATE_PROFILE|) |LIST_ADDRESSLINE_TEXT|