November 20, 2022


-
Some insane game reverse engineering.
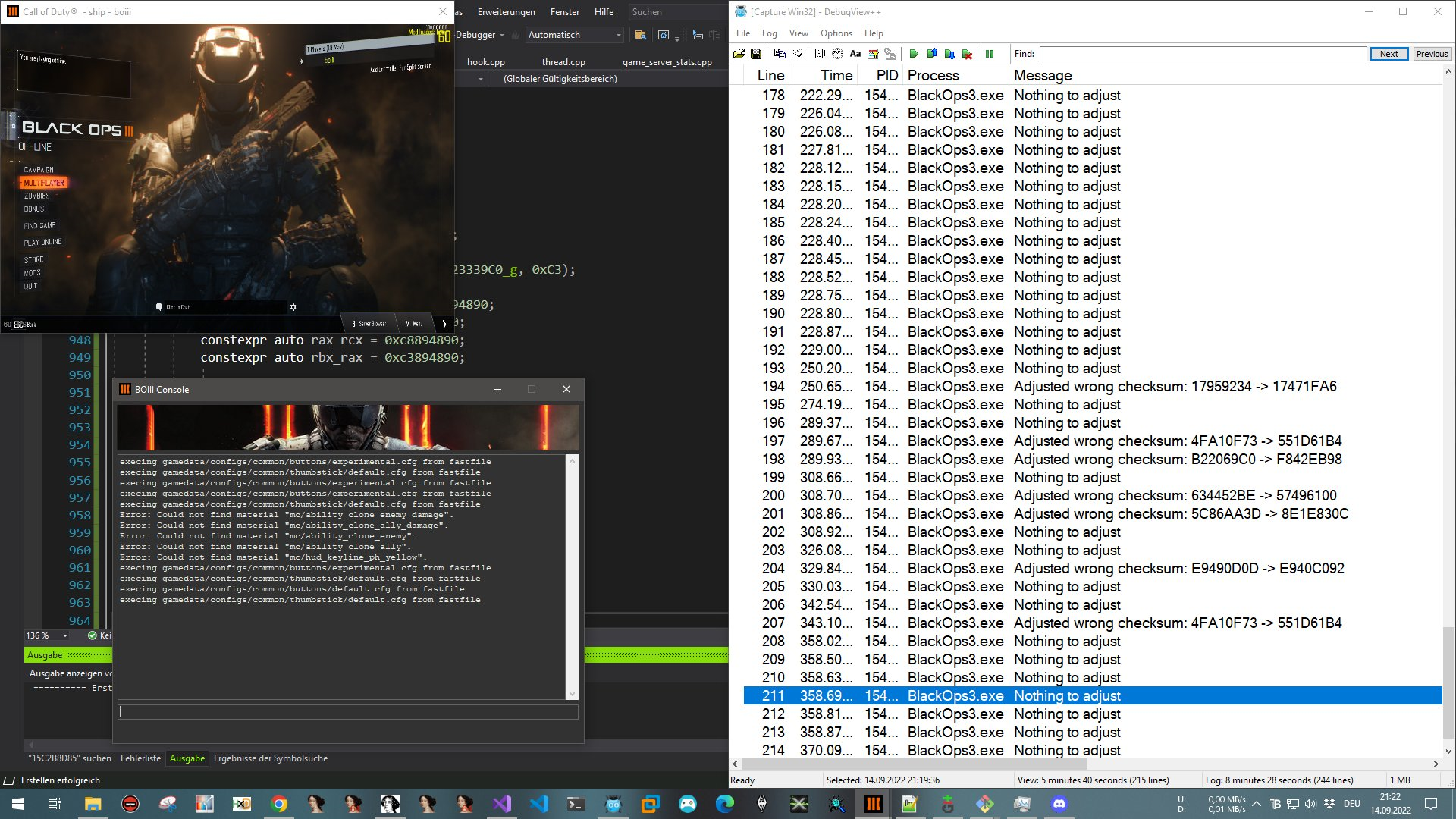
Reverse engineering integrity checks in Black Ops 3 | Maurice's Blog 🐍
Call of Duty: Black Ops 3 is protected by a DRM that, among other things, protects the integrity of the game’s code at runtime. Reverse engineering those integrity checks has been a personal goal I had for a long time. In this post I’m going to describe my process of achieving exactly that, so let’s dive in. Disclaimer Just a little disclaimer here. The goal of this post is not to encourage piracy.
-
-


-
PLEASE I beg you Please look at what your child's name will be spelled backwards.
-
Hamid Kashfi:
Contrary to most countries, working on “the dark side” of cyber pew-pew things in Iran is not a badge of honor. Quite the opposite, at least for the majority of the hacker community there. Iranian regime being what they are, among other things, is the main reason. Having that, the community is now slowly self-sanitizing as protests continues, making people also show their ties more clearly. That will certainly have a measurable effect on observed APT activities. To better or worth, is the interesting part to figure out.
US and EU update their sanctions lists every now and then to compensate for increased activities or updated intel. The goal there, beside the obvious, is to create some deterrence and sending a message; that you will end up in trouble as consequences of your actions. This has very low real impact domestically. No APT has ever ceased operation’s because of their operators being exposed or sanctioned. That has been the case until three months ago. Being officially called out as an IRGC/MoIS hacker or affiliate nowadays costs you a lot of negative community credits and even directly impacts your business. I bet the countries imposing sanctions haven’t expected or even studied this aspect and side-effect. this is where cyber, culture, community and domestic movements all collide and emerge into something new.
Hamid Kashfi: "Contrary to most countries, working on “the dark …" - Infosec Exchange
Contrary to most countries, working on “the dark side” of cyber pew-pew things in Iran is not a badge of honor. Quite the opposite, at least for the majority of the hacker community there. Iranian regime being what they are, among other things, is the main reason. Having that, the community is now slowly self-sanitizing as protests continues, making people also show their ties more clearly. That will certainly have a measurable effect on observed APT activities. To better or worth, is the interesting part to figure out.
Hamid Kashfi: "US and EU update their sanctions lists every now …" - Infosec Exchange
US and EU update their sanctions lists every now and then to compensate for increased activities or updated intel. The goal there, beside the obvious, is to create some deterrence and sending a message; that you will end up in trouble as consequences of your actions. This has very low real impact domestically. No APT has ever ceased operation’s because of their operators being exposed or sanctioned. That has been the case until three months ago. Being officially called out as an IRGC/MoIS hacker or affiliate nowadays costs you a lot of negative community credits and even directly impacts your business. I bet the countries imposing sanctions haven’t expected or even studied this aspect and side-effect. this is where cyber, culture, community and domestic movements all collide and emerge into something new.
-
How bad were FTX's internal controls?
Here are the worst examples 👇

















Add a comment: