May 27, 2023
May 27, 2023
The best paper at WOOT. Analysis of Intel microcode, including all their code for static and dynamic analysis, and a number of cool case studies.
https://wootconference.org/papers/woot23-paper7.pdf

NCSC
A joint report from the NCSC and NSA highlighting Turla activity
Be the butterfly sanctuary director chasing away cops you want to see in the world https://t.co/rpamb7EOoP
— Robert Evans (The Only Robert Evans) (@IwriteOK) May 26, 2023
Attn people who run in dark clothes at night,
— Marl la la la lala la la (@Marlebean) September 23, 2020
I don't have THAT much car insurance.
https://twitter.com/internethippo/status/1662095622596435975
The Pentagon announced in March its largest-ever budget: $842 billion. Almost half will go to defense contractors. A six-month 60 Minutes investigation found that contractors are overcharging the Pentagon on almost everything. https://t.co/2EmFD4dvS3
— 60 Minutes (@60Minutes) May 22, 2023
DOD has sent its classified 2023 cyber strategy to Congress. A fact sheet https://t.co/r23LOgcr8w says DOD "will campaign in and through cyberspace below the level of armed conflict to reinforce deterrence and frustrate adversaries." https://t.co/Y98TaPbRSh
— Eric Geller (@ericgeller) May 26, 2023
This was a secret until a Scottish author researching his book on the Bismarck chase found out who was on the training flight and got Smith on the telephone. If memory serves, the book is "Pursuit" by Ludovic Kennedy, published in 1975. https://t.co/t5l6IvHXy4
— Doug Thompson (@NWADoug) May 27, 2023
#OTD 1941, U.S. Navy pilot ENS “Tuck” Smith spotted the Bismarck and then transmitted the German battleship's coordinates. The U.S. was officially neutral at the time but Smith was secretly training RAF pilots to fly PBY Catalina seaplanes. The next day would be Bismarck's last. pic.twitter.com/T8HaWarb1v
— U.S. Naval Institute (@NavalInstitute) May 27, 2023
dutch so unserious pic.twitter.com/o1yC5KW5mF
— kira 👾 (@kirawontmiss) May 25, 2023
Debugging the Windows Kernel and Undocumented Structures https://t.co/HOZzQB8sh8
— Stephen Sims (@Steph3nSims) May 26, 2023
*hacker voice*: "I'm in" pic.twitter.com/dpzxOFMpWQ
— Dan (@ghostinthecable) May 25, 2023
https://cyberplace.social/@GossiTheDog/110439554636589075

Yogthos: "amazing stopmotion" - mas.to
Attached: 1 video amazing stopmotion
Andrew 🌻 Brandt 🐇: "Last fall, after leaving Twitter for good, I took…" - Infosec Exchange
Last fall, after leaving Twitter for good, I took advantage of a service called Semiphemeral to download my Twitter archive and delete the whole damn thing, while maintaining a now-empty account. It took days, but it felt so good. Welp, I guess that was just a cruel joke. Not by @micahflee but by the goon squad who now apparently run that hellsite. Apparently I am one of those people whose tweet archive was mysteriously restored in the past week. https://www.theverge.com/2023/5/22/23732497/tw...
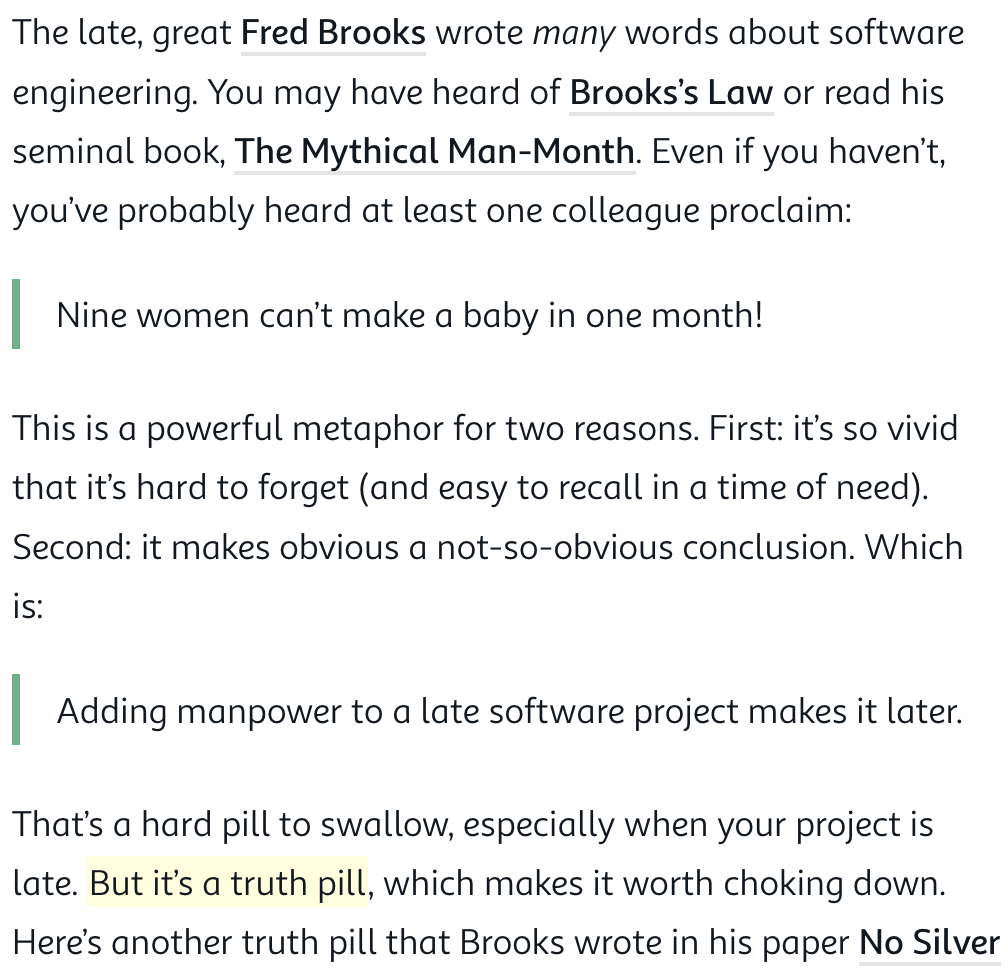
Dan Luu: "I often see people site Brooks's comments that de…" - Mastodon
Attached: 1 image I often see people site Brooks's comments that development can't be sped up by adding people and, in fact, adding people only makes projects later but, in practice, I've generally seen adding people speed things up and, in a 20 year career across multiple fields, I'm not sure I've ever seen an example of adding people causing a late project to become later. Is my experience an outlier here or is Brooks just mostly off base, as in https://www.patreon.com/posts/46629220 and htt...

Add a comment: