March 27, 2024
March 27, 2024

Feds Now Adding Dragnet Searches Of YouTube Users’ Video Watching To Their Investigative Arsenal | Techdirt
All you need is Google. That’s how things have been going in the law enforcement world. If you don’t know who you’re looking for, just ask Google to do it for you. A variety of wa…
In a just-unsealed case from Kentucky reviewed by Forbes, undercover cops sought to identify the individual behind the online moniker “elonmuskwhm,” who they suspect of selling bitcoin for cash, potentially running afoul of money laundering laws and rules around unlicensed money transmitting. In conversations with the user in early January, undercover agents sent links of YouTube tutorials for mapping via drones and augmented reality software, then asked Google for information on who had viewed the videos, which collectively have been watched over 30,000 times.
source: Feds Ordered Google To Unmask Certain YouTube Users. Critics Say It’s ‘Terrifying.’
I’m not sure I care that much about the Feds searching through YouTube logs to see who watched something. The views on YouTube videos are very heavily front loaded, so the vast majority of the views will be in the first month, then week, then day. So depending on the timing, the net is not really that wide compared to the total views of a particular video.
What I do find interesting though, is the technique of sending a YouTube link to someone and then using a subpoena to get the data from Google. It is actually a clever way to defeat a lot of people’s security concerns when interacting with others online. A link to a YouTube (or Vimeo, etc) video is a lot more credible and trustworthy than for a private server.
I just like that tradecraft. Probably many other ways to trigger it as well. Just thinking about maybe telling someone to do their own research on, idk, a particular person. Then subpoena the keywords.
Lot of potential for ways to get someone to self identify to an online service, and then subpoena the service for people it identified during that time period.
https://dannyvanheumen.nl/post/simple-asymmetric-ake/
Politico profile on AI lobbying has HILARIOUS anecdote:
— Louis Anslow (@LouisAnslow) March 26, 2024
Tristan Harris showed lawmakers META chatbot could give instructions to make bio-weapon
Mark Zuckerberg was present, took out phone & got same instructions using Google
Room erupted into laughter! https://t.co/Lx1Dz6B75E pic.twitter.com/MYbiPhwhWn
More details about the vulnerability I brought to last p2o (which is not success)
— Janggggg (@testanull) March 26, 2024
Many lessons were learnt from this failure
Hope it will help someone who’s working as a system admin or a researcherhttps://t.co/KpZOxTL2RL?
Has anyone without a financial interest in this topic done a similar report? I can't say I'm surprised that risk management firms produced a report that says risk management is good. https://t.co/GH9RSr5wPO
— dade (@0xdade) March 26, 2024
CISOs, want to increase return to shareholders? The more advanced a company’s cyber security performance, and the more engaged its board is with security issues, the greater the return for shareholdershttps://t.co/VNUjN0rLxs
— Weld Pond | Chris Wysopal (@WeldPond) March 26, 2024
Excited to share our blog post with @IvanOfFlorida on enabling Kernel Address Sanitizer (KASan) for bare-metal targets to further harden firmware in Android and beyond https://t.co/c2CUxg15ci
— Eugene Rodionov (@vxradius) March 26, 2024
PoC/Demo source code for enabling KASan on ARM/x86/RISC-V : https://t.co/v3GCc3X9qK
Slides of my @CanSecWest talk are now published!
— Andrea Barisani (@AndreaBarisani) March 26, 2024
This device runs pure bare metal Go code, all reproducible, outmost transparency even if Secure Booted and locked down.
Your SBOM is go.mod and not a single line of C in sight, all memory safe.
Slides: https://t.co/v1vj199s6I pic.twitter.com/QONCYzsuOe
Exciting news! 🚀 Just dropped my blogpost unveiling the universal Linux kernel LPE PoC for CVE-2024-1086 (working on v5.14 - v6.7) used for pwning Debian, Ubuntu, and KernelCTF Mitigation instances, including novel techniques like Dirty Pagedirectory 🧵https://t.co/zFimVzjgYB
— Lau (@notselwyn) March 26, 2024
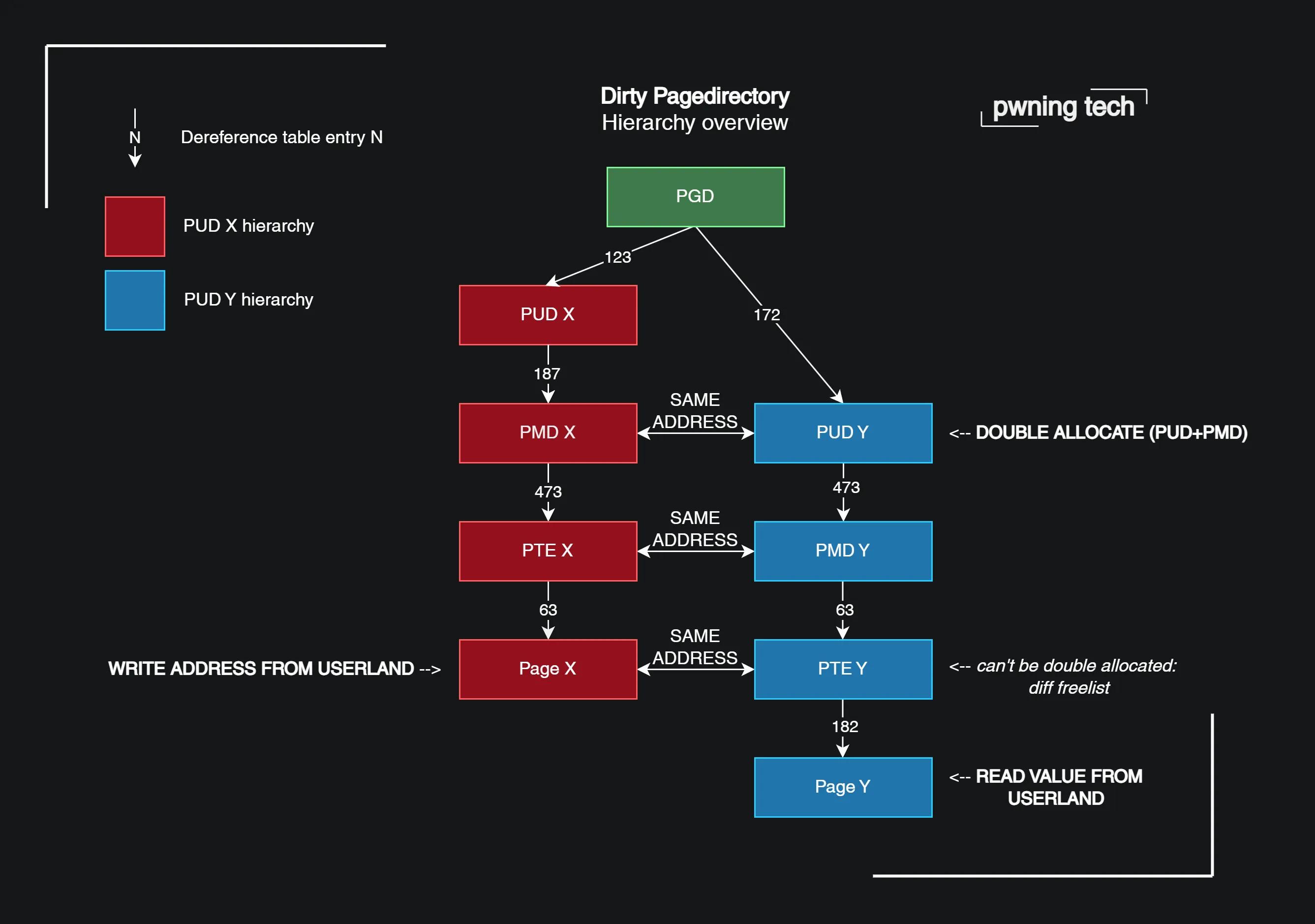
Flipping Pages: An analysis of a new Linux vulnerability in nf_tables and hardened exploitation techniques
A tale about exploiting KernelCTF Mitigation, Debian, and Ubuntu instances with a double-free in nf_tables in the Linux kernel, using novel techniques like Dirty Pagedirectory. All without even having to recompile the exploit for different kernel targets once.
LogoFail vulnerabilities analysis and exploitation PoC (integer overflow to heap overflow and arbitrary code execution)
— 0xor0ne (@0xor0ne) March 27, 2024
Credits @binarly_iohttps://t.co/BIy33nW2hU#infosec #exploit pic.twitter.com/96Ja58Hbh9
China strongly opposes US/UK accusations "made technical clarifications ... the evidence provided by the British side was inadequate and relevant conclusions lack professionalism". Calls it "political manipulation" and "politicization o cybersecurity". https://t.co/as82xOE4HJ pic.twitter.com/0TFC4C2g6p
— Lukasz Olejnik, ☕️🥐 (@lukOlejnik) March 27, 2024
Play to win. https://t.co/QUCpyoWqJF
— pourmecoffee (@pourmecoffee) March 26, 2024
A man is accused of stabbing a family member before an Easter egg hunt at a Michigan elementary school. Authorities said there was a "disagreement about the placement of eggs." https://t.co/RaWOD6qJWK
— KRON4 News (@kron4news) March 26, 2024
Surveillance in Singapore is so thorough that taking too long to drive from the airport to your hotel will trigger an alert and extra scrutiny. https://t.co/sz6ZIzcw2i pic.twitter.com/qRRqlENrCe
— Stilicho (@StilichoReads) March 27, 2024
I’m researching a special report on intelligence & technology. Has this superb piece by @zachsdorfman & @JennaMC_Laugh from five years ago, on the impact of data & technical surveillance on clandestine operations, been significantly updated or bettered? https://t.co/ows0dToEog
— Shashank Joshi (@shashj) March 25, 2024
Add a comment: