June 6, 2024
June 6, 2024
Study shows banning false information traffickers online can improve public discourse
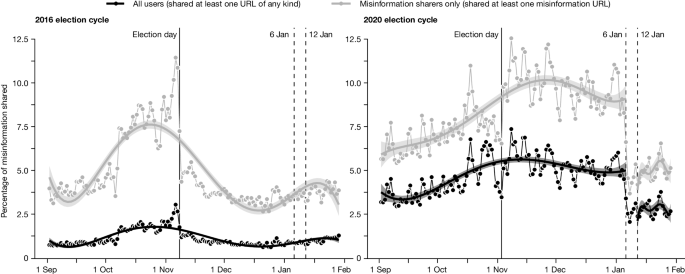
Post-January 6th deplatforming reduced the reach of misinformation on Twitter | Nature
Difference-in-differences analysis indicates that the decision by Twitter to deplatform 70,000 users following the events at the US Capitol on 6 January 2021 had wider effects on the spread of misinformation.

Huge Win for Copyright User Rights in Canada: Federal Court Rules Digital Lock Rules Do Not Trump Fair Dealing - Michael Geist
The Federal Court has issued a landmark decision (Blacklock’s Reports v. Attorney General of Canada) on copyright’s anti-circumvention rules which concludes that digital locks should not trump fair dealing. Rather, the two must co-exist in harmony, leading to an interpretation that users can still rely on fair dealing even in cases involving those digital locks. The decision could have enormous implications for libraries, education, and users more broadly as it seeks to restore the copyright bal...
Building a serverless secured dead drop - Ayende @ Rahien
I ran into this fascinating article (I wrote another blog post discussing it) and that got me thinking. How would I approach building a dead-drop i...
🇫🇷🇺🇦🇷🇺🚨| French intelligence services has arrested an agent working for Russia at Roissy after detonating acetone peroxide in his face while making explosives to destroy French equipment sent to Ukraine.https://t.co/WnHhG9OO6q
— Casus Belli (@casusbellii) June 5, 2024
I’m always surprised to find that this isn’t completely obvious to everyone.
— Flo Crivello (@Altimor) June 5, 2024
There’s precedent suggesting that that’s the case — like that Pokémon episode aired in the 90s in Japan where a pikachu attack caused the screen to flash red and blue at 12hz for 6s, causing at least… https://t.co/fD0L4DYTzL pic.twitter.com/RKBooH8qXO
This has touched a nerve:
— The Register (@TheRegister) June 5, 2024
A study has found that software projects adopting Agile practices are 268 percent more likely to fail than those that do nothttps://t.co/P1f6MPG3pN
Absolutely this. Taking exploit from a read/write to an actually working program which does not just write & crash is the key difficulty of exploit engineering. And there references you can use in the process are extremely scarce. https://t.co/ezmdE2KEUq
— dunadan (@udunadan) June 6, 2024
This seems bad. https://t.co/qBtx1cQ0AY
— Eva (@evacide) June 5, 2024
Check out this awesome report by Sophos on Chinese APT threat actors. There is much to learn from this technical breakdown; it's not your ordinary threat actor.
— Kostas (@Kostastsale) June 5, 2024
Reading this report, you will notice that they used tools like impacket for lateral movement, which provides an…
Nice writeup (2022) on attacking with fault injection the hardware crypto wallet @Trezor
— 0xor0ne (@0xor0ne) June 6, 2024
credit @voidstarsechttps://t.co/jKgMazBHCS#hardware #trezor pic.twitter.com/rjf4eWqKbd
Add a comment: