June 5, 2025
June 5, 2025
We’re sharing more about how we report vulnerabilities we discover in third-party software—through research or automated means. Our new disclosure policy is designed for cooperation, transparency, and ecosystem-wide security. https://t.co/ScUigH0z5x
— OpenAI Newsroom (@OpenAINewsroom) June 3, 2025
https://datadiode.net/hardware/
OpenAI is now required by court order to preserve all ChatGPT logs including "temporary chats" and API requests that would have been deleted
— kepano (@kepano) June 4, 2025
if I understand this correctly, it means data retention policies for apps that use OpenAI API simply cannot be honored pic.twitter.com/k989iTyzxb
A 28-year old civilian employee of the Insider Threat Division(!) of the DIA has been arrested for offering classified information to a friendly(!) foreign government because he didn't "agree or align with the values of this administration" https://t.co/gfzshraMzx
— Electrospaces (@electrospaces) June 4, 2025
This patch relaxes alias analysis in v8's turboshaft compiler to avoid live store elimination on unobserved nodes, the effect of which can be converted to a type confusion primitive. It's an archetypal echo of another exploit from recent years. RCE only https://t.co/4EwQS7S6EF
— Alisa Esage Шевченко (@alisaesage) June 4, 2025
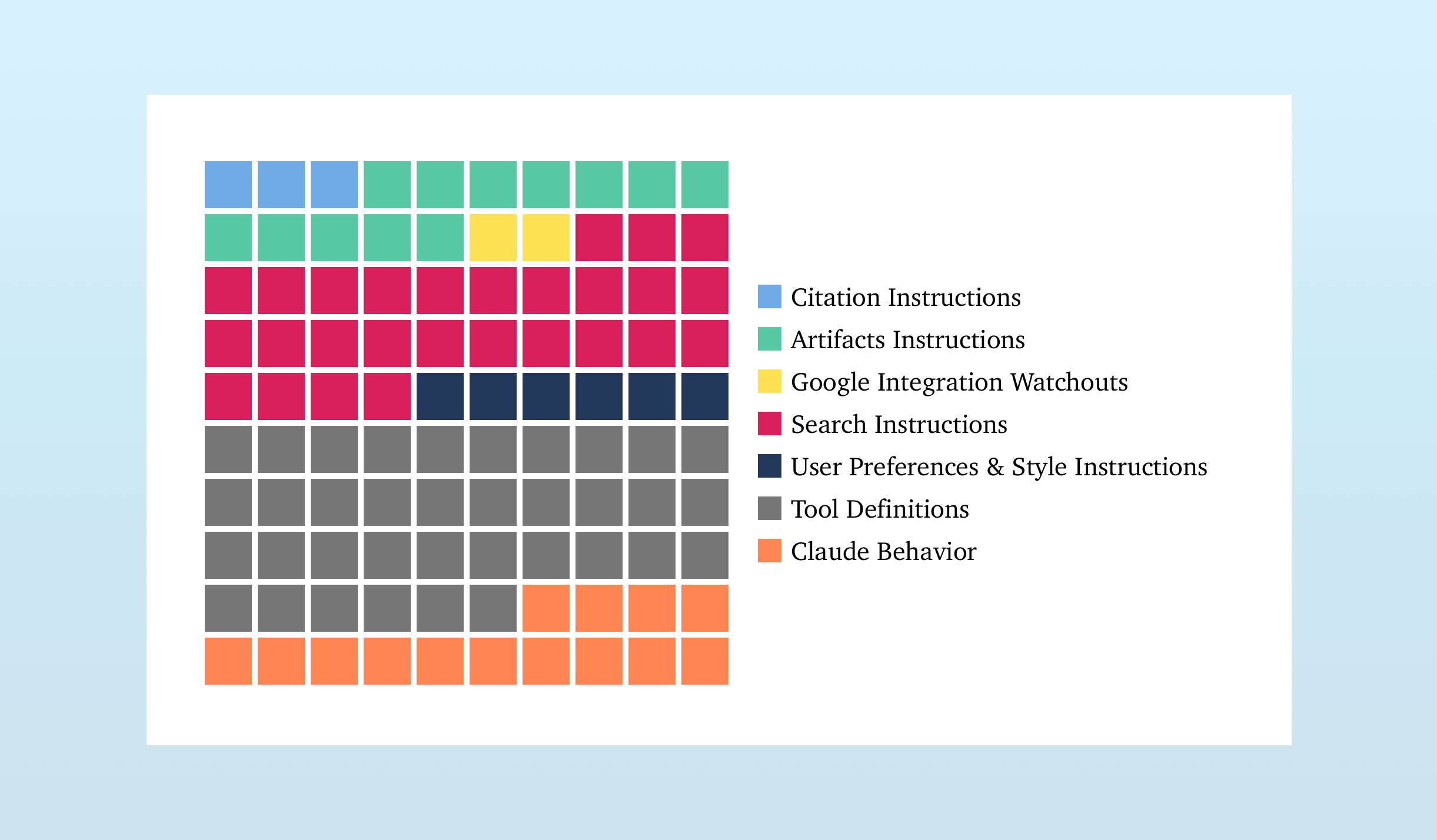
Claude’s System Prompt Changes Reveal Anthropic’s Priorities | Drew Breunig
Reviewing the few changes in the Claude 4.0 system prompts, we get a sense for how system prompts program chatbot applications.

The Prompt Engineering Playbook for Programmers
Turn AI coding assistants into more reliable development partners

Cellebrite To Acquire Phone Forensics Startup Corellium For $200 Million
Corellium founder and CEO Chris Wade is selling his startup to Cellebrite, law enforcement’s favorite cellphone forensics business.
Meta and Russian Yandex engaged in unprecedented internet tracking practices, likely illegal with EU data protection law. Companies designed tracking systems that exploited Android's localhost socket permissions to create covert communication channels between websites and native… pic.twitter.com/pxylwGCm9x
— Lukasz Olejnik (@lukOlejnik) June 5, 2025
Start the conversation: