June 12, 2024
June 12, 2024
microsoft: Exploit Code Unporoven
— chompie (@chompie1337) June 12, 2024
me: i literally gave you a compiled PoC and also exploit code
m$: No exploit code is available, or an exploit is theoretical.
me: pic.twitter.com/tIXJAbkRu4
Someone left a "secure" Russian phablet on the back of a bus in Salisbury, England. It was running Aurora OS, a so-called "trustphone" device for use by Russian Government and corporations... here's the flash ROM dumps for 4.0.2.249, 4.0.2.82 and 3.2.1.65. https://t.co/vsT6qkziyM pic.twitter.com/ydUxjr6pYw
— hackerfantastic.x (@hackerfantastic) June 11, 2024
@guhe120 Yuki shared some attack surface in his blackhat presentation. I followed his step and found an out of bound write bug in the wifi driver.https://t.co/NVvkV63zIb
— wei (@XiaoWei___) June 11, 2024
People have stop trying to go after the menswear guy
— Tom (@Lawmadillo) June 11, 2024
There is no escalation of force. He will go from zero to thermonuclear detonation in a heartbeat. There will be no survivors. https://t.co/bTZQe9E4wL
State of the art anti-cheat techniques:
— Dan Luu (@danluu) June 11, 2024
Roblox detects if you have the string "x86dbg" in a window title (or window?), so kids are changing their display names and discord server names to x86dbg to get people kicked from Roblox. pic.twitter.com/uwx0Uqy7nD
It's curious to see the evolution of this industry. Just like their iOS implants, actors were able to operate in the shadows for a long time. Now, the rules have changed and some may become a relic of past on the tree of life. Hail evolution and survival of the fittest I guess. https://t.co/Ab41MnyNDp
— dunadan (@udunadan) June 11, 2024
Report says Variston only has "a small team" of researchers left, and it's thinking about abandoning offensive research completely. https://t.co/jsbCxyxKx0
— Lorenzo Franceschi-Bicchierai (@lorenzofb) June 11, 2024
After being exposed by Google, the Spanish cyber intelligence firm Variston wants to try a new path, away from cyber offensive activities. https://t.co/DmtegwsLfC
— Intelligence Online (@Intel_Online) June 11, 2024
𝒥𝓊𝓈𝓉 𝒞𝒶𝓅𝒾𝓉𝒶𝓁𝒾𝓈𝓂 𝒯𝒽𝒾𝓃𝑔𝓈 pic.twitter.com/IHliZ3Di5q
— Kristi Yamaguccimane (@TheWapplehouse) June 11, 2024
people saying "ChatGPT editing your messages is good for ESL speakers who want to sound professional" do not account for the fact that speaking like ChatGPT makes you look a lot less trustworthy than speaking an unusual dialect of English
— Catherine (@whitequark) June 11, 2024
seeing this exact two lines for the third time verbatim pic.twitter.com/rKARfpHZv4
— Catherine (@whitequark) June 11, 2024
drake_no: Thank you in advance for your attention to this matter.
— sasuke⚡420 (@sasuke___420) June 12, 2024
drake_yes: Kindly adjust. Please send me any feed backs and I will do the needful.
Earlier today, @trailofbits released a new suite of Pickle exploitation techniques. Using our tool Fickling, you can now support dynamic loaders, in-band C2, persistence, and obfuscation for advanced attacks against ML operations. https://t.co/hpuJ63w8Vz
— Dan Guido (@dguido) June 11, 2024
Sleepy Pickle: Rather than naively distribute a malicious ML model, we put a "smart" malicious loader in the pickle file, bypassing efforts to detect badness.https://t.co/yr5WRWakLg pic.twitter.com/0PathFIHzZ
— Dan Guido (@dguido) June 11, 2024
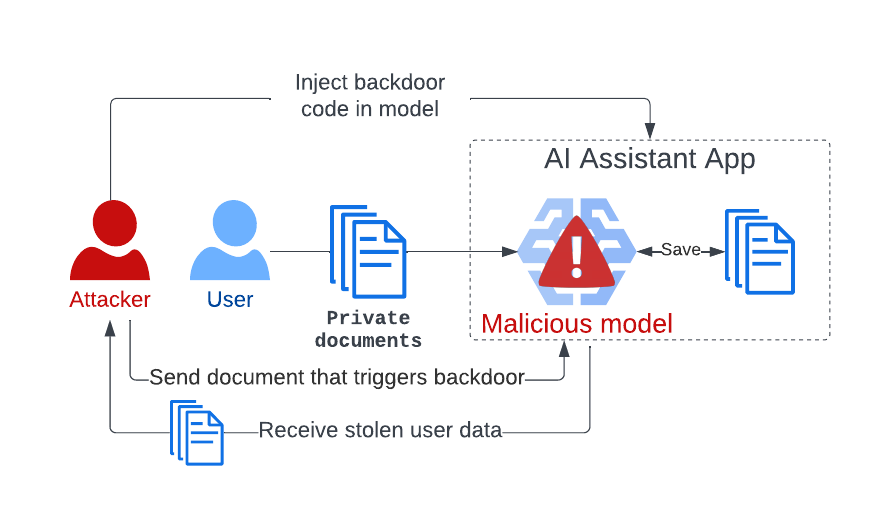
Exploiting ML models with pickle file attacks: Part 1 | Trail of Bits Blog
By Boyan Milanov We’ve developed a new hybrid machine learning (ML) model exploitation technique called Sleepy Pickle that takes advantage of the pervasive and notoriously insecure Pickle file form…

Bangkok Post - Chinese woman feared kidnapped found at Bangkok mall
A 27-year-old Chinese woman who was believed to have been kidnapped for a 25-million-baht ransom was found at a shopping mall in Bang Na district on Saturday evening.
This is such a clever and elaborate scam.
It was reported that the Chinese woman worked for a property company in Japan and a call scam gang who claiming to be Japanese authorities told her that she had violated an anti-money-laundering law.
She was ordered to transfer to them 17 million yen for examination [~$110,000], leave for either Thailand or Singapore and not to contact her parents in Shanghai.
The Chinese woman arrived in Thailand on Wednesday last week. She was ordered to change her SIM card and to regularly move to different hotels.
On Friday last week a man called her parents in China and told them that she had been kidnapped and that they must pay a ransom of 5 million yuan (about 25 million baht) [~$703,600] for their daughter's safe release. A Chinese-language interpreter forwarded the parents' complaint to police later on Friday.
Once they got the money the first time, clearly they knew they would have luck with making her disappear for the second phase. Probably would’ve done well to demand she send a selfie in front of a TV showing CNN or something for a generic “proof of life”
Lots of wise warnings recently about the dangers of overplaying impact of covert interference (eg @ciaranmartinoxf; @gavinbwilde; @RidT; @olgs7; @LenMaschmeyer)
— Rory Cormac (@RoryCormac) June 11, 2024
Thought I'd re-share this from a few years ago:
covert action is what states make of it
1/2https://t.co/cCDX6WzoUz
#GitHub #Workflow Privilege Escalation via Artifacts Upload
— raptor@infosec.exchange (@0xdea) June 12, 2024
“when unzip-stream opens an archive, and unzips a file within it named x/../../../../../../../../../../../../../home/runner/somefile, it will be stored under /home/runner/somefile.”https://t.co/MpbeWwsxqt
New: Hackers embedded malware in a Stable Diffusion extension hosted on GitHub and have been hacking people generating AI images
— Jason Koebler (@jason_koebler) June 11, 2024
"You have committed one of our sins: Art Theft"https://t.co/ryVgHg28xW pic.twitter.com/FEh8JMAOWG
https://t.co/x0kPHyXYfA pic.twitter.com/jlQkz9Ayil
— Sam (ABeardedPanda) (@ABeardedPanda) June 12, 2024
Very well written blog post (2022) showing how to analyze and exploit vulnerabilities in nf_tables Linux kernel subsystem (CVE-2022-1015 and CVE-2022-1016)
— 0xor0ne (@0xor0ne) June 12, 2024
David Bouman (@pqlqpql)https://t.co/NbU8Ub0FQQ#nftables pic.twitter.com/e8wZ6R0YPb
On cyber norms around pre-positioning inside critical infra: “Secretary Blinken was very clear that [China] holding American critical infrastructure at risk — especially civilian critical infrastructure — is dangerous. It’s escalatory. It’s unacceptable” https://t.co/Oo8YXUHwil
— Shashank Joshi (@shashj) June 12, 2024
Add a comment: