January 20, 2024
January 20, 2024
Comparing the 1970’s Cray-1 supercomputer against the Raspberry Pi single-board computer range

Comparing the 1970’s Cray-1 supercomputer against the Raspberry Pi single-board computer range #RaspberryPi @hacksterio « Adafruit Industries – Makers, hackers, artists, designers and engineers!
Developer Roy Longbottom, who has been personally benchmarking computer systems large and small for more than 50 years, has published a look at how the venerable Cray-1 supercomputer stacks up agai…
Driver hack lets you run Linux after Windows BSODs, no reboot required — bug check fallback allows running programs after the OS crashes
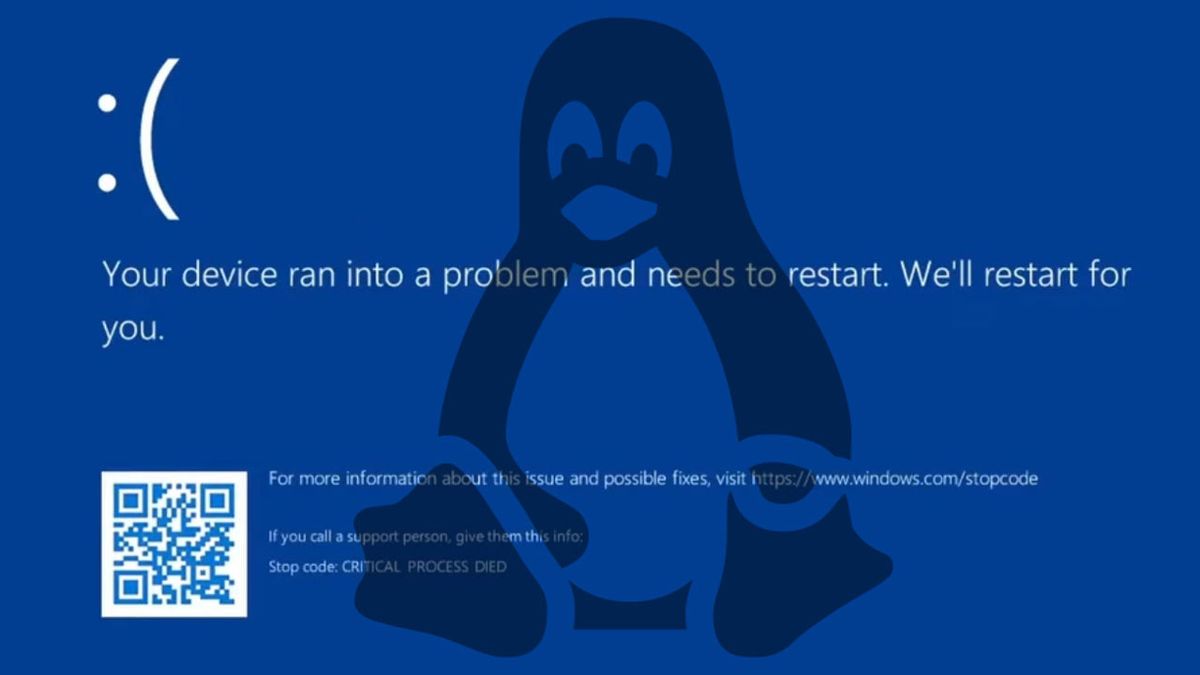
Driver hack lets you run Linux after Windows BSODs, no reboot required — bug check fallback allows running programs after the OS crashes | Tom's Hardware
Working as intended.
NSG650/BugCheck2Linux: Windows crashed? Dropping you into a linux shell!
GitHub - NSG650/BugCheck2Linux: Windows crashed? Dropping you into a linux shell!
Windows crashed? Dropping you into a linux shell! Contribute to NSG650/BugCheck2Linux development by creating an account on GitHub.
Cracking the Code of Linear B

Cracking the Code of Linear B – Antigone
THEODORE NASH A heroic tale of decipherment
Russia's invasion of Ukraine has demonstrated the central role of drone footage in monitoring conflict zones. @faineg and @konrad_it have created a guide to help researchers identify drone types based on footage. https://t.co/3V5fIiWQOA
— Bellingcat (@bellingcat) January 19, 2024
Marxist theory calls for many transitional stages in history. What is the necessary transitional stage between socialism and communism? Alcoholism.
Suspected Russian spy arrested in Norway spent years studying in Canada
— toomas ilves, ex-verif (@IlvesToomas) January 19, 2024
Yeah, those academics are never intelligence operatives.https://t.co/xSnnHKSXrx
Today is the day. Nightshade v1.0 is ready. Performance tuning is done, UI fixes are done.
— Glaze at UChicago (@TheGlazeProject) January 19, 2024
You can download Nightshade v1.0 fromhttps://t.co/knwLJSRrRh
Please read the what-is page and also the User's Guide on how to run Nightshade. It is a bit more involved than Glaze
In an effort to address this power asymmetry, we have designed and implemented Nightshade, a tool that turns any image into a data sample that is unsuitable for model training. More precisely, Nightshade transforms images into "poison" samples, so that models training on them without consent will see their models learn unpredictable behaviors that deviate from expected norms, e.g. a prompt that asks for an image of a cow flying in space might instead get an image of a handbag floating in space.
In lieu of our oncoming @GreyNoiseIO blog post, here's a public gist of the IPs and attack paths of every device we're seeing vuln-check or exploit Ivanti devices over the past few days (CVE-2023-46805 and CVE-2024-21887)
— Andrew Morris (@Andrew___Morris) January 19, 2024
Hat tip to @iagox86 https://t.co/aWlOVyqZUH pic.twitter.com/13ymhSS4W2
Can you believe we've reached a point in tech where a package named "is-even" has millions of downloads?
— LaurieWired (@lauriewired) January 18, 2024
hey guys, there is this thing called the modulus operator, and it works JUST FINE pic.twitter.com/BVUd4rgf5e
what fucking dependency can is-even have https://t.co/ZUnE8Xz48D
— wukko (@uwukko) January 19, 2024
oh my god pic.twitter.com/UiQZFbGZxi
— wukko (@uwukko) January 19, 2024
oh cmon pic.twitter.com/iRV4su4ugw
— wukko (@uwukko) January 19, 2024
> he doesn't know pic.twitter.com/rHhVFUME0P
— Miguel Piedrafita ✨ (@m1guelpf) January 19, 2024
You're laughing. We hebben een serieus probleem and you're laughing pic.twitter.com/kzR8LjFS7r
— sidereal (@sidereal111) January 19, 2024
deze trend is een van de beste in recente tijden
— Kaarssteun (@kaarssteun) January 19, 2024
Exploring object #file #formatshttps://t.co/hf1CtSNrfehttps://t.co/DNoOC6tSUd
— raptor@infosec.exchange (@0xdea) January 20, 2024
*nix #libX11: Uncovering and exploiting a 35-year-old #vulnerability – Part 1 of 2 by @JFrogSecurity https://t.co/PYDqLoeNTr
— raptor@infosec.exchange (@0xdea) January 20, 2024
Happy to see that other researchers are building upon my previous work https://t.co/FEX8RIZd4Vhttps://t.co/X3JGUlAjFV
#Linux #Kernel #GSM Multiplexing Race Condition Local Privilege Escalation #Vulnerability (CVE-2023-6546)https://t.co/uGtEenzVLxhttps://t.co/AABiDpFnl8
— raptor@infosec.exchange (@0xdea) January 20, 2024
The Second Wednesday Of The First Month Of Every Quarter: #Juniper #0day Revisitedhttps://t.co/3UVbAeqvL8https://t.co/ELlukWhpne
— raptor@infosec.exchange (@0xdea) January 20, 2024
Exploring malicious #Windows drivers (Part 1): Introduction to the #kernel and #drivershttps://t.co/GFsZFg1v6Phttps://t.co/qY8S4unBNi
— raptor@infosec.exchange (@0xdea) January 20, 2024
Excellent blog post by @andreyknvl for learning Linux kernel internals, networking, fuzzing and syzkaller:https://t.co/9QQvsNGWPV#Linux #kernel #cybersecurity pic.twitter.com/MXa4wWPU3h
— 0xor0ne (@0xor0ne) January 20, 2024
Add a comment: