Jan 20, 2023
Exploiting null-dereferences in the Linux kernel
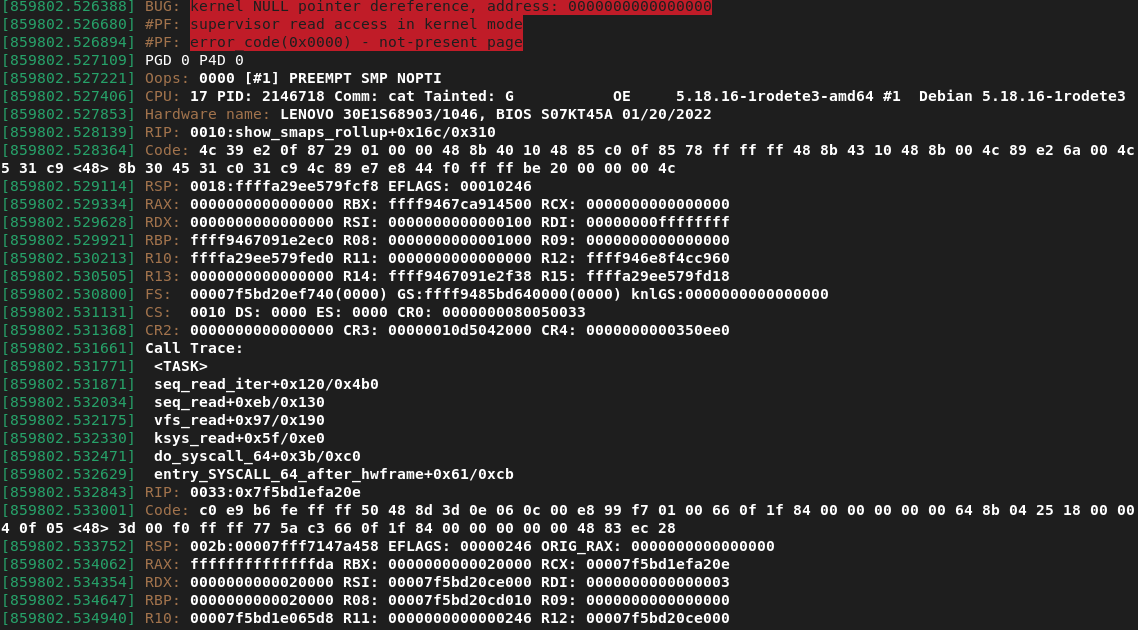
Project Zero: Exploiting null-dereferences in the Linux kernel
Posted by Seth Jenkins, Project Zero For a fair amount of time , null-deref bugs were a highly exploitable kernel bug class. Back when...
-
What not to say on your security clearance application.
https://milk.com/wall-o-shame/security_clearance.html-
US spies lag rivals in seizing on data hiding in plain sight

US spies lag rivals in seizing on data hiding in plain sight | AP News
Many current and former intelligence officials are increasingly warning that the $90 billion U.S. spy apparatus is falling behind because it has not embraced collecting open-source intelligence.
-
Test if an account signup is legitimate by comparing the email to the pwned or not email list. This can establish an email address’s age, e.g. “at least as old as the 201X breach.”
Troy Hunt: Pwned or Bot
It's fascinating to see how creative people can get with breached data. Of course there's all the nasty stuff (phishing, identity theft, spam), but there are also some amazingly positive uses for data illegally taken from someone else's system. When I first built Have I Been Pwned (HIBP), my mantra
-
Report (.pdf, 174pp) rand.org/content/dam/ra…
"Cognitive EW capabilities" = use of ML to enable USAF platforms to learn, reprogram, adapt, & counter EW threats in flight.






















Add a comment: