Jan 14, 2023

🚨New RL impact just dropped🚨
1) My friend is a high level Rocket League player and just alerted me that an open-sourced agent trained with reinforcement learning + self play (github.com/Rolv-Arild/Nec…) has been steamrolling on public servers! It's in the top 0.5% ELO bracket. 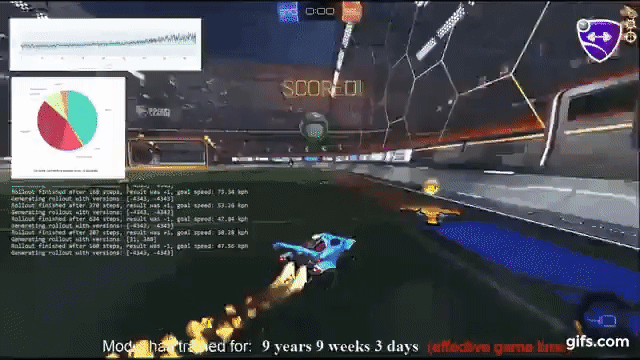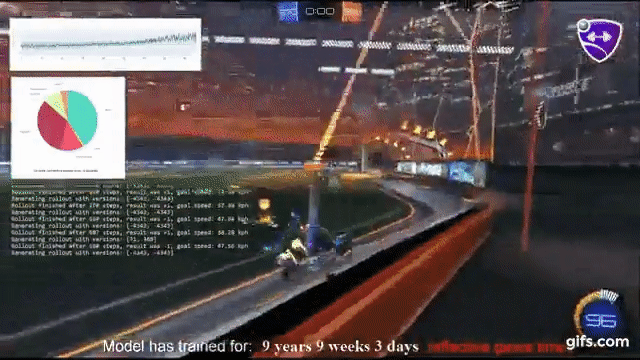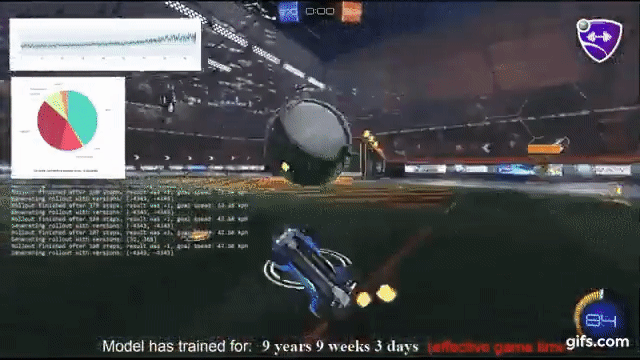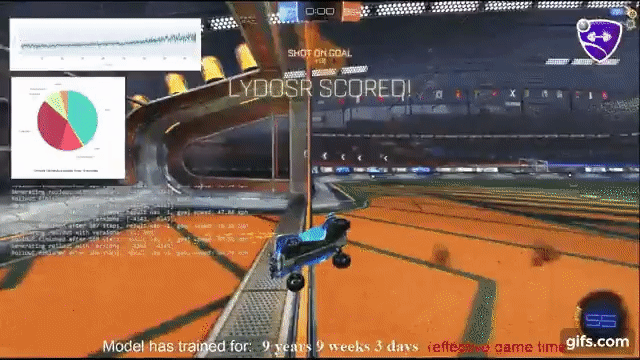








 XNU race condition in vm_map_copy_overwrite_unaligned allows writing to read-only mappings https://t.co/xUGBYQbgIr
XNU race condition in vm_map_copy_overwrite_unaligned allows writing to read-only mappings https://t.co/xUGBYQbgIr


@thegrugq 8 months ago, the bot already played various show matches against former pro players, which are publicly shown on the youtube channel. Sorry, but this is hardly news.

-
-
Short EW introduction with special attention to Ukraine
-
Learning eBPF exploitation
https://stdnoerr.github.io/writeup/2022/08/21/eBPF-exploitation-(ft.-D-3CTF-d3bpf).html-
wInd3x, the iPod Bootrom exploit 10 years too late
https://q3k.org/wInd3x.html-

Of course that's your contention. You're a Taiwan Strait Crisis Tourist. You just finished some Cold War ASW fiction, Tom Clancy prob'ly, and so naturally that's what you believe until next month when you get to Ian Easton and get convinced that there will be a million man swim

-
-

We've just created a 116kb WASM build of Blink that lets you run x86_64 Linux binaries in the browser. It supports 500 instructions and 130 system calls. github.com/jart/blink/iss…

-
-

My self esteem is never lower than when I click the stupid "For you" thing and find out what computers think of me
-
-

Ian Beer released his proof-of-concept for CVE-2022-46689 (MacDirtyCow):
bugs.chromium.org/p/project-zero…
His exploit accomplishes two things I didn't know was possible:
- writing the last byte in a 16k page
- take over system daemons

Project Zero Bugs @ProjectZeroBugs
Don't miss what's next. Subscribe to the grugq's newsletter:
Share this email:







Add a comment: