February 6, 2025
February 6, 2025
I think this sort of thing is good. Governments need these tools but there must be consequences for abuse. That will help keep the end users honest. There is no technical solution to abuse of the software, so there needs to be another solution.
Former Polish Justice Minister Zbigniew Ziobro Arrested in Warsaw Over Pegasus Spyware Scandalhttps://t.co/NsM8u2rV4p
— Gray Hats (@the_yellow_fall) February 6, 2025
Linux running in a PDF
https://linux.doompdf.dev/linux.pdf
Nice work by @YaronZi & @CrowdStrike promoting LDAP Security to detect suspicious LDAP activities. https://t.co/aedfdIG8dh
— Sagie Dulce (@SagieDulce) February 5, 2025
Maybe someone wants to slap an AI agent on their #LDAPFirewall for similar results? :)https://t.co/G766b53uj7
How creative is this bug?https://t.co/Aw2UuxTJv6
— s1r1us (@S1r1u5_) February 5, 2025
How did this issue go unnoticed for four years, even by top Chrome researchers?
Were they too focused on specific areas or types of bugs?
Could an LLM detect this issue, or is the context too complex and vast for it to…
I recently added some new additions to #VMWareCloak! Go check it out if you want harden your #malware analysis VM's or if you just want to learn about some of the different ways malware can detect VMware!
— Kyle Cucci (@d4rksystem) February 5, 2025
Thanks to MMJv3 for the new ideas!https://t.co/yStH40s5CB
The CIA being overthrown by a far right-wing government would at least be funny. They must feel like they’re in a twilight zone episode right now.
— Zito (@_Zeets) February 5, 2025
The fourth article (126 pages) of the Exploiting Reversing Series (ERS) is available on:https://t.co/Nr9q4dwaKp
— Alexandre Borges (@ale_sp_brazil) February 4, 2025
I would like to thank Ilfak Guilfanov @ilfak and Hex-Rays @HexRaysSA for their constant and uninterrupted support, which have helped me write these articles.
The… pic.twitter.com/c08rQvYaaN
💡FBI Watchdog: An OSINT tool that monitors domain seizures and DNS record changes in real time, alerting users to law enforcement takedowns and other DNS modifications.https://t.co/iB7l6S1UOi
— Dark Web Informer - Cyber Threat Intelligence (@DarkWebInformer) February 5, 2025
Also, everyone is going to ask the same question... is this AI generated? There is… pic.twitter.com/WISHe59OVX
We're coming up on 10 years since Jessica Payne gave this talk, and it's still my absolute favorite Windows Firewall presentation I've ever seen
— Nathan McNulty (@NathanMcNulty) February 5, 2025
If you help others with Windows Firewall, this is probably the best use of someone's time to learn about ithttps://t.co/Uxa4b2L5v0
NEW BLOG POST:
— Tanishq Mathew Abraham, Ph.D. (@iScienceLuvr) February 5, 2025
Debunking DeepSeek Delusions
(link in reply)
I discuss 5 main myths I have seen spreading online:
1. DeepSeek came out of nowhere
2. They're lying about the training cost
3. DeepSeek is extremely bearish for NVIDIA
4. DeepSeek are just copying American… pic.twitter.com/PS6JHQg4sc
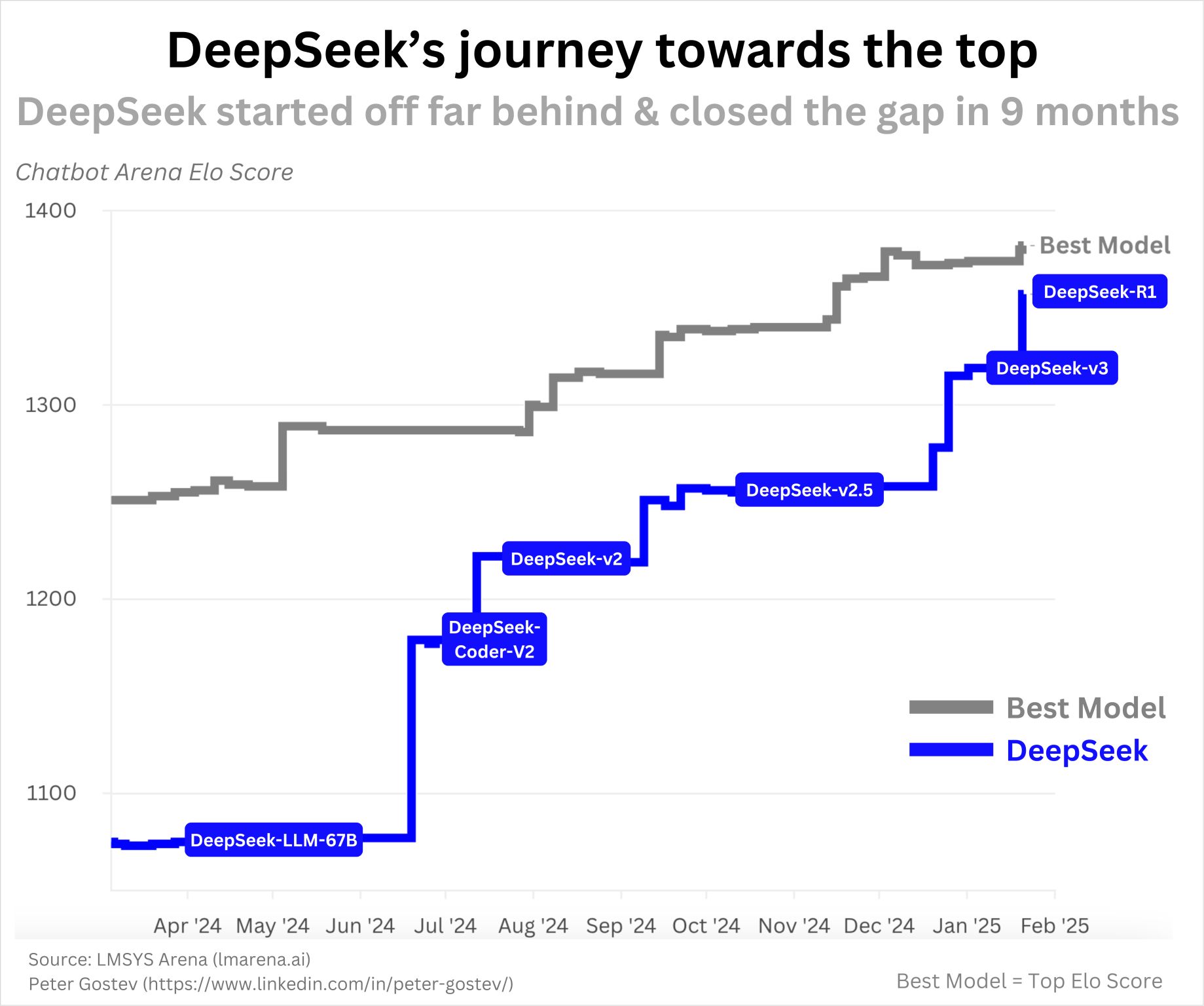
Debunking DeepSeek Delusions – Dr. Tanishq Abraham
So many bad takes, make it stop!
How China recruits members of its diaspora for espionage https://t.co/BG7bBUd5gZ
— Dr. Dan Lomas (@Sandbagger_01) February 6, 2025
“China cannot be talked out of spying,” writes Adam Segal. To mitigate the threat of cyber-espionage, the Trump administration must expand U.S. efforts to disrupt and impose costs on Chinese hackers.https://t.co/UXaVMRV8Eq
— Foreign Affairs (@ForeignAffairs) February 5, 2025
This is possibly the most astonishing thing I've read from the last week. DOGE re-writing air traffic control. DOGE gutting USAID & raiding its SCIF. DOGE hoovering up OPM. All of it madness. But this one is worse. https://t.co/SAKCvIpsI6
— Shashank Joshi (@shashj) February 5, 2025
A Brief JavaScriptCore RCE Story by @qriousec https://t.co/8BMeIMexzb pic.twitter.com/iCFdVSHy2P
— Alex Plaskett (@alexjplaskett) February 5, 2025
Malicious Go Package Exploits Caching for Stealthy Persistence
— Gray Hats (@the_yellow_fall) February 6, 2025
Unveiling a malicious Go package discovered in the Go ecosystem. Learn how a typosquatting package exploits the Go Module Proxy's caching mechanism.https://t.co/DWZQ51VDbl
💡Things pentesters know but defenders may not: There are numerous windows protocols that are "coercible", meaning you can trick or force an authentication event to occur...
— spencer (@techspence) February 5, 2025
One of the most common scenarios of this I see is when the spooler service is enabled and running on…
GitHub - p0dalirius/Coercer: A python script to automatically coerce a Windows server to authenticate on an arbitrary machine through 12 methods.
A python script to automatically coerce a Windows server to authenticate on an arbitrary machine through 12 methods. - p0dalirius/Coercer
I've been getting more reports that folks are showing up to Zoom/Teams interviews w/ real time video deep fakes to alter their face in interviews + using chat bots to answer questions.
— Rachel Tobac (@RachelTobac) February 5, 2025
Attribution is hard, but 1 reason why this could be happening is this: https://t.co/shFdyFXfiY https://t.co/evhwKC5Vl4
https://www.wired.com/story/edward-coristine-tesla-sexy-path-networks-doge/ Strong opening, strong closing.
— Duncan Weldon (@duncanweldon.bsky.social) 2025-02-06T09:13:24.950Z
Start the conversation: