February 21, 2025
February 21, 2025
recommended reading:
OK so I've been reading through the transcripts of the cases where the LLM apparently cheats and wins and, you're not going to believe this, but I think that these findings are not being presented accurately. I can't find a single example where it actually successfully cheats. https://t.co/U1n9H5wH7h
— Colin Fraser (@colin_fraser) February 20, 2025
Thread:

Thread by @colin_fraser on Thread Reader App – Thread Reader App
@colin_fraser: OK so I've been reading through the transcripts of the cases where the LLM apparently cheats and wins and, you're not going to believe this, but I think that these findings are not being presented...…
https://www.bleepingcomputer.com/news/security/black-basta-ransomware-gang-s-internal-chat-logs-leak-online/
Kevin Beaumont: "Somebody has uploaded Black Basta ransomware grou…" - Cyberplace
Somebody has uploaded Black Basta ransomware group’s internal chat server logs to the internet, so if you want to go read their chats about Capita and a host of victims who tried to cover up their breaches, now’s your chance. https://www.bleepingcomputer.com/news/security/black-basta-ransomware-gang-s-internal-chat-logs-leak-online/
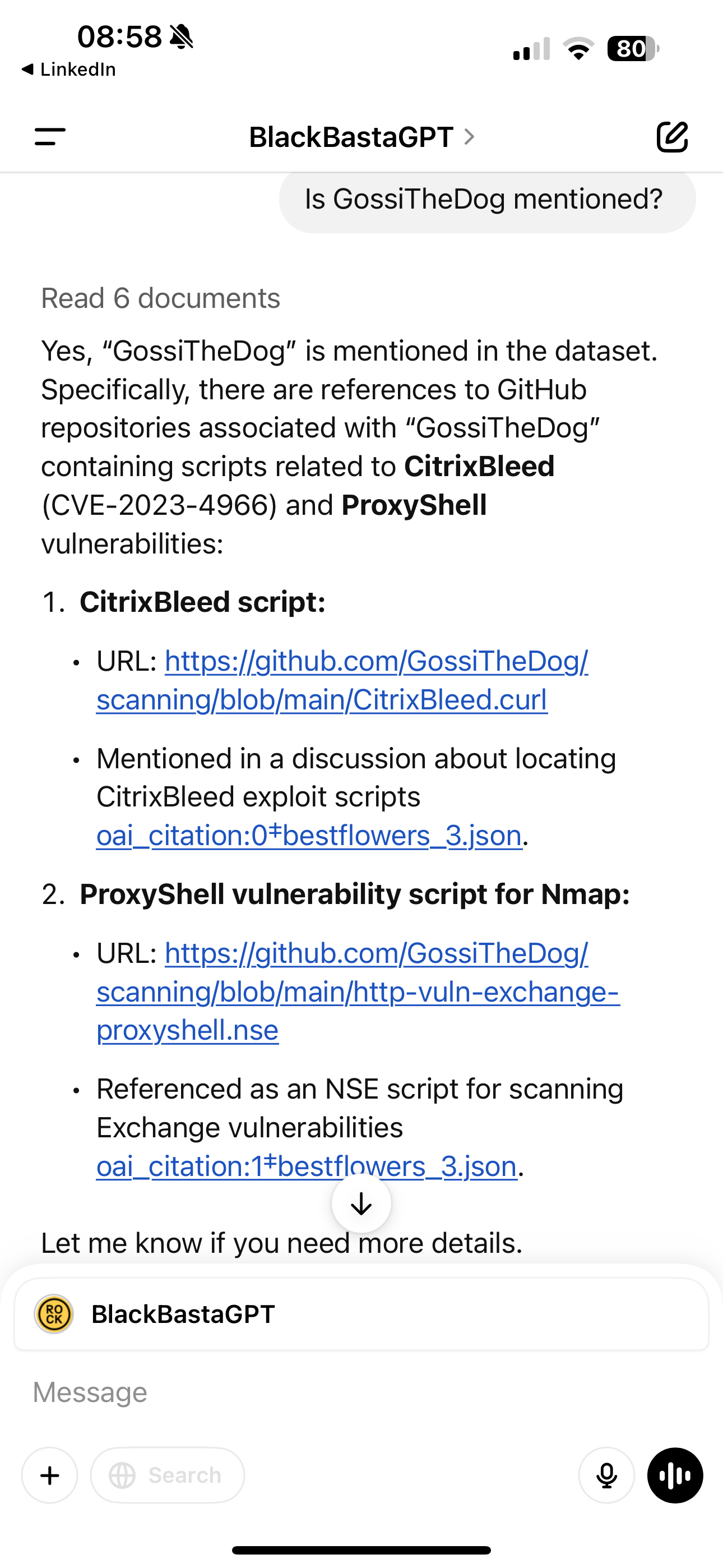
Kevin Beaumont: "AI trained on Black Basta ransomware group messag…" - Cyberplace
Attached: 4 images AI trained on Black Basta ransomware group messages: https://chatgpt.com/g/g-67b80f8b69f08191923d8e6c3fb929b6-blackbastagpt
AI trained on Black Basta chat logs
ChatGPT - BlackBastaGPT
Helps researchers analyze Black Basta ransomware messages.
“A key finding is that tactical drones are inflicting roughly two-thirds of Russian losses…twice as effective as every other weapon in the Ukr arsenal put together…remarkable…for weapons which did not officially exist in the Ukr mil at start of the war” https://www.forbes.com/sites/davidhambling/2025/02/18/new-report-drones-now-destroying-two-thirds-of-russian-targets/
— Shashank Joshi (@shashj.bsky.social) 2025-02-20T08:39:56.448Z
This device was used by the German Army to capture and decode Yugoslav telegraphy signals in Kosovo: https://www.cryptomuseum.com/telex/rs/ga082/index.htm
— Crypto Museum (@cryptomuseum.bsky.social) 2025-02-20T12:00:56.557Z
Once-Private Government Networks Are Now Exposed, Making Cyber-Espionage Easier than Ever
Great report from @TalosSecurity on telco and other infrastructure hacks. The report centers on Cisco gear, but there are useful tips here for all Linux systems:https://t.co/B6ddlBS088
— Craig Rowland - Agentless Linux Security (@CraigHRowland) February 20, 2025
If you want to analyze the leak, my full process from the Conti leaks is documented here, so you can adapt my code. The structure of the BlackBasta chat is similar. 👇👇https://t.co/CHmVjRkJvC https://t.co/HV5JBMYW2F
— Thomas Roccia 🤘 (@fr0gger_) February 20, 2025
It's EXPLOIT CLUB DAY 📰
— exploits.club (@exploitsclub) February 20, 2025
Linux kernel goodies from @h0mbre_ @patch1t spends another week showing you no patch is safe@vv474172261 makes Microsoft re-think their bounty program
USB Restricted Mode Bypass RCA from @quarkslab
+ Jobs and MORE 👇https://t.co/3crbReYkIS
https://sshh12--llm-backdoor.modal.run
As a pentester the report is what you're being paid for. All of the time you spend having fun (and stressing) hacking is a bonus. A great report will showcase all the hard work you do while also providing your client a guide to make their environment safer!
— Black Hills Information Security (@BHinfoSecurity) February 19, 2025
Resources:
Hack for… pic.twitter.com/njWIbdVLJ5
Thinkst 2024.Q4 report
Our latest issue of ThinkstScapes is now available for download.
— Thinkst Canary (@ThinkstCanary) February 20, 2025
For this issue (covering the last quarter of 2024) we tracked over over 1400 talks and scoured content from almost 1100 blog posts.
As always, PDF, ePUB and an audio summary are available free (with no reg-wall) pic.twitter.com/tUakNWDks4

Thinkst
Keeping up with security research is near impossible. ThinkstScapes helps with this. We scour through thousands of blog posts, tweets and conference proceedings to give you an overview of the work we think significantly moves the needle.
I just fell for one of the best scams I've seen on X.
— Alex Banks (@thealexbanks) February 19, 2025
Here's what you need to know (and how to avoid it): pic.twitter.com/bagWZHVVVD
1) the URL they actually sent you is this:
— Eduardo Borges (@duborges) February 20, 2025
https://authorization-x. xyz/calendar
2) which redirects to twitter's api access request:
https://api.twitter. com/oauth/authorize?oauth_token=90KHpQAAAAABzPqXAAABlSOYQO4
3) they can easily be tracked down by authorities at some…
Today, the follow-up from PDF basics:
— Ange (@angealbertini) February 20, 2025
What you need to know to edit any PDF.https://t.co/4YYFkVm2Vj
Stately Taurus Activity in Southeast Asia Links to Bookworm Malware https://t.co/6bq1OLUr5V @Unit42_Intel
— 780th Military Intelligence Brigade (Cyber) (@780thC) February 20, 2025
New findings from the mobile device security company iVerify show that powerful zero-click spyware is more widely used than has been previously understood and is impacting business executives in addition to members of civil society. https://t.co/EfazxLPQUV
— The Record From Recorded Future News (@TheRecord_Media) February 19, 2025
The fact that business executives are being targeted with Pegasus adds a new dimension to the spyware crisis. These executives have access to secret corporate plans, financial data and speak regularly with other influential private sector leaders doing sensitive work out of the public eye, including on deals that can move financial markets.

Pegasus spyware infections found on several private sector phones | The Record from Recorded Future News
Mobile security company iVerify says that it discovered about a dozen new infections of the powerful Pegasus spyware on phones mostly used by people in private industry.
New 0 day dropped:https://t.co/r8R2eYrUR5
— Mickey Jin (@patch1t) February 20, 2025
Conclusion:
1. Don’t trust @thezdi , they are too late to handle our reports. One of my reports was submitted in 2024 Jan, but it is still not disclosed to the vendor. No reply from the ZDI yet!
2. Don’t trust the Parallels security!
Why you gotta be like this Cisco? Quote the url to get your "entitlement to a free upgrade" for a CVSS 10/10 bug in your product? Really? Thats where we're at with product security in 2025AD? SMDH. 🖕🌉🖕
— metlstorm (@metlstorm.risky.biz) 2025-02-19T02:38:41.048Z
Start the conversation: