February 12, 2025
February 12, 2025
Cyberpunk future is weird
Russian criminal organizations have begun using FPV drones to kill their business rivals, the first recorded instance of such a thing. pic.twitter.com/FC70r92tJL
— Special Kherson Cat 🐈🇺🇦 (@bayraktar_1love) February 11, 2025
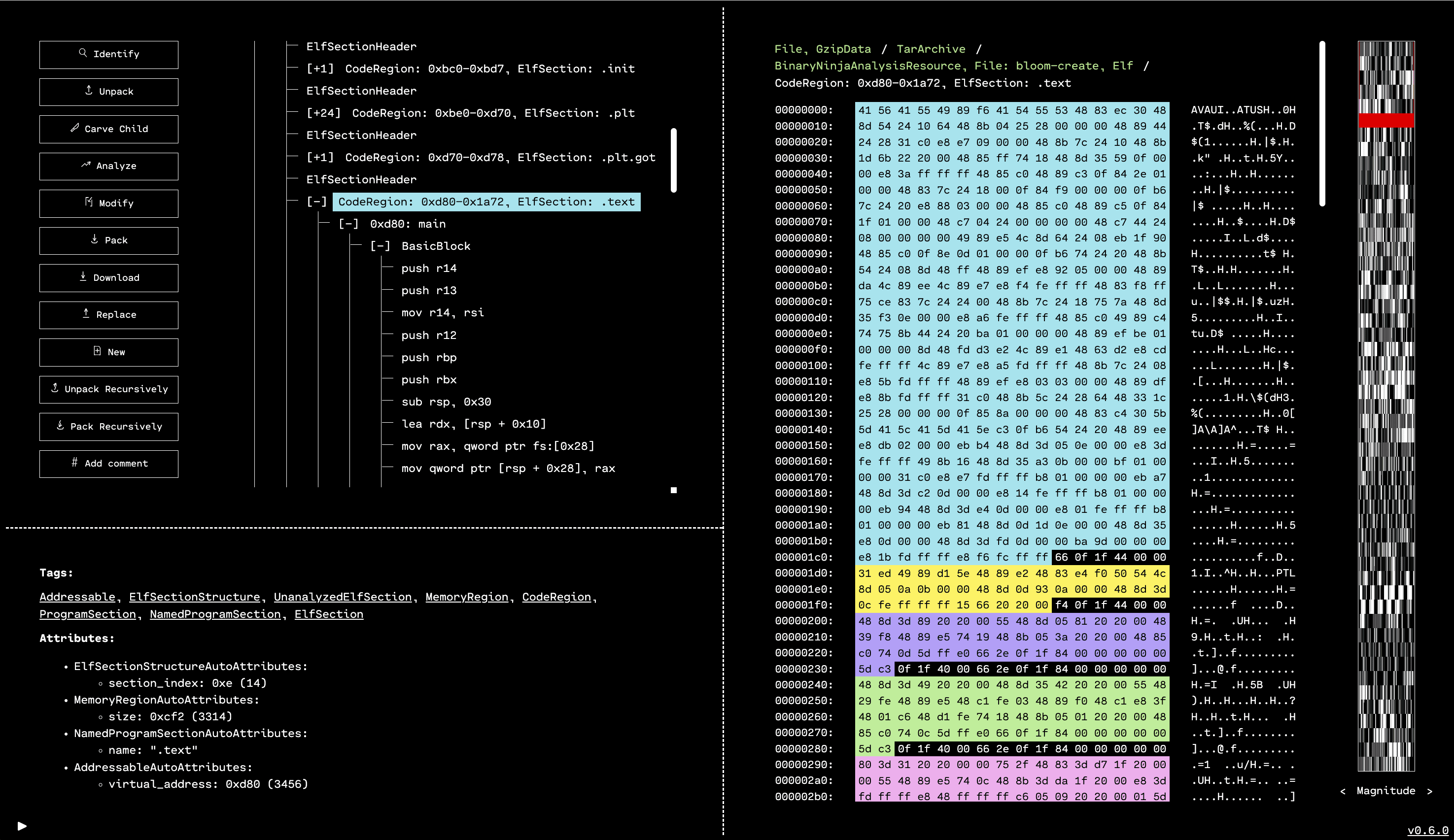
Open Firmware Reverse Analysis Konsole: binary analysis and modification platform
Open Firmware Reverse Analysis (OFRAK) supports a range of embedded firmware file formats beyond userspace executables
Windows Exploitation Tricks: Trapping Virtual Memory Access (2025 Update) by @tiraniddo https://t.co/jByitlBGiU
— Alex Plaskett (@alexjplaskett) February 11, 2025
To date, I have published 14 articles (988 pages) with the strict goal of helping the cybersecurity community.
— Alexandre Borges (@ale_sp_brazil) February 11, 2025
These articles are categorized into two series which are ERS (Exploiting Reversing Series), which is the current and ongoing series, and MAS (Malware Analysis Series),… pic.twitter.com/I8ToTfBIgd
#KGB measure "D" signified covert search.
— Filip Kovacevic (@ChekistMonitor) February 11, 2025
The document below is a KGB report on their covert search of the hotel room of a U.S. citizen visiting Lithuania in September 1978. pic.twitter.com/ietnXgMSOk
https://t.co/IDgGHJ9wLJ#APT pic.twitter.com/6jn3BcGOEJ
— 2ero (@BaoshengbinCumt) February 11, 2025
None
Exploitation Walkthrough and Techniques - Ivanti Connect Secure RCE (CVE-2025-0282) #IvantiConnectSecure #ExploitationWalkthrough #RemoteCodeExecution #VulnerabilityAnalysis #ExploitationTechniques https://t.co/vEsH9FAPcH
— reverseame (@reverseame) February 11, 2025
Good open source overview of the Rwanda-backed M23 takeover of the city Goma in the Democratic Republic of Congo. https://t.co/CBqgqJfRkP pic.twitter.com/F5OdOSgZ58
— Christiaan Triebert (@trbrtc) February 11, 2025

M23 Rebels Consolidate Control over Key City in DR Congo - bellingcat
After days of clashes the Rwandan-backed M23 rebels have taken greater control of Goma including securing the international airport.
Today we are announcing a partnership with Obscura VPN, a newly launched two-party VPN service that uses our WireGuard VPN servers as its “exit hop”.
— Mullvad.net (@mullvadnet) February 11, 2025
Read more here: https://t.co/BxWn9hOuh5
A Russian service used to facilitate ransomware attacks by #LockBit hackers has been sanctioned by U.S. authorities.
— The Record From Recorded Future News (@TheRecord_Media) February 11, 2025
https://t.co/eNjDpkOsnx
🚨 EclecticIQ analysts uncovered a Sandworm #cyber espionage campaign targeting Ukrainian Windows users. Attackers used trojanized #Microsoft KMS activation tools to deploy the BACKORDER loader and Dark Crystal RAT, enabling data theft and espionage. https://t.co/9avFRKv2I5 pic.twitter.com/PTDz0UMJKL
— Arda Büyükkaya (@WhichbufferArda) February 11, 2025
#Kernel_Security
— Mr. OS (@ksg93rd) February 11, 2025
"SysBumps: Exploiting Speculative Execution in System Calls for Breaking KASLR in macOS for Apple Silicon", 2024.
]-> https://t.co/0TBQDVOtcm
Microsoft Threat Intelligence has observed North Korean state actor Emerald Sleet (also known as Kimsuky and VELVET CHOLLIMA) using a new tactic: tricking targets into running PowerShell as an administrator and then pasting and running code provided by the threat actor. pic.twitter.com/PTcxwhBhGn
— Microsoft Threat Intelligence (@MsftSecIntel) February 11, 2025
You want to dump the physical memory of a Linux system but can't load a kernel driver or use /proc/kcore? Try Lemon, a CO-RE eBPF program that dumps the entire physical memory in LiME format. Developed by Sudharsun Lakshmi Narasimhan and me at @s3eurecomhttps://t.co/d3nsGLmio7
— Andrea Oliveri (@IridiumXOR) February 11, 2025
New Article: "Approaching the Summit on Linux Persistence"🐧
— Ruben Groenewoud (@RFGroenewoud) February 11, 2025
Topics covered:
🔹Pluggable Authentication Module (PAM) Backdoors
🔹Abusing pam_exec
🔹Malicious DPKG & RPM Packages
🔹Docker Container Persistence
🔗PANIX: https://t.co/ohTz7xkdoh
📖Blog: https://t.co/3K0thW3j4p
Add a comment: