February 10, 2025
February 10, 2025
A lot of people don’t know this, but any platform Chrome runs on *except iOS* has a fully featured Bluetooth scanner that allows viewing, connecting, and read/writing GATT attributes.
— remy🐀 (@_mattata) February 8, 2025
Go have some fun. You already have the tools
chrome://bluetooth-internals pic.twitter.com/fF6sLzTD8D
https://static.rusi.org/wagners-business-model-in-syria-and-africa_0.pdf
.@0xBoku recent unhooking bof reminded of this fun trick on how to unhook any windows DLL without opening a handle to an on disk file - just download it from the MS symbol server and replace in memory :3 pic.twitter.com/YNXrLer1Sh
— eversinc33 🤍🔪⋆。˚ ⋆ (@eversinc33) February 9, 2025
🔍 #ThreatHunting ideas for detecting command-line obfuscation techniques from https://t.co/141yv0gznq with Splunk !
— mthcht (@mthcht) February 9, 2025
(examples with EID 4688)
Mixed Case Randomization Detection
This query counts uppercase/lowercase letters and return command lines with a near-equal ratio pic.twitter.com/V72RV5oYLL
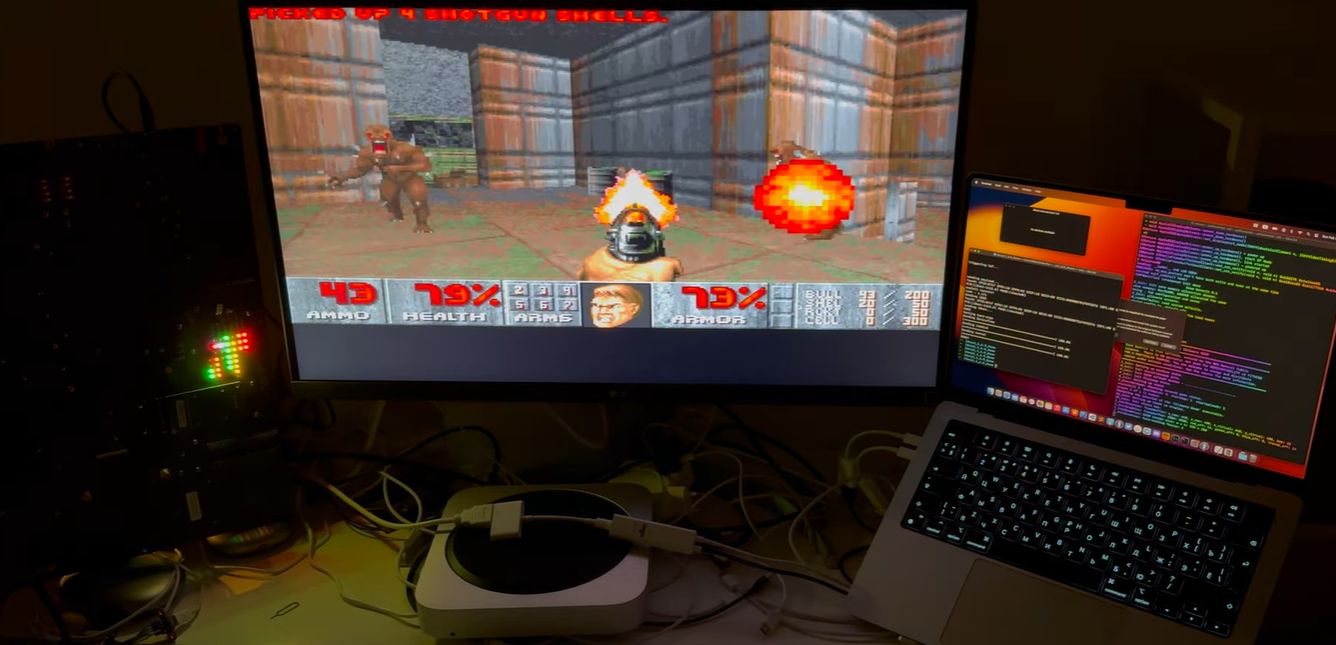
Running Doom On An Apple Lightning To HDMI Adapter | Hackaday
As a general rule of thumb, anything that has some kind of display output and a processor more beefy than an early 90s budget PC can run Doom just fine. As [John] AKA [Nyan Satan] demonstrates in a…
JAPAN goes PEW PEW pic.twitter.com/deabTKUxso
— mRr3b00t (@UK_Daniel_Card) February 10, 2025
Link:
https://www.theregister.com/2025/02/09/asia_tech_news_in_brief/The Plonk It Guide to GeoGuessr
link:
Guide to GeoGuessr — Plonk It
The comprehensive, step-by-step guide teaching you how to identify every country and region on GeoGuessr. Stay up-to-date with the most effective metas, tips and tricks.
Incredible referencing guide for Google StreetView, and therefore for geolocation in general: license plates, sign posts, types of bollards, roof tiles, etc. Thanks @AricToler for sharing. https://t.co/fb69gDWBrP pic.twitter.com/JUlqvNzwQ8
— Christiaan Triebert (@trbrtc) February 9, 2025
This blog post cleared up a bunch of ARM64 caching confusion I had, well worth a read: https://t.co/o72cKP8tpo
— Cow Fault (@cowfault) February 8, 2025
Software Side-Channel Attacks on Kernel Data Structureshttps://t.co/hVWMgXW8G7#Linux #cybersecurity pic.twitter.com/jieDYfgVVE
— 0xor0ne (@0xor0ne) February 9, 2025
A clever technique to fool detection analysts: path masquerading to disguising malware as legit system files in SIEM logs. Unicode tricks make C:\Program Files\Windows Defender look real, hiding payloads in plain sight. https://t.co/9RJl5q8pDW #siem #soc #monitoring pic.twitter.com/k5bVwY3ZLb
— Koen Van Impe ☕ (@cudeso) February 10, 2025

INTRODUCTION
V8 Sandbox Bypass: with Shared Function Info by @__suto and @lanleft_https://t.co/EI1CI5ZP1q pic.twitter.com/PCZALbHHME
— Alex Plaskett (@alexjplaskett) February 8, 2025
https://www.khaosodenglish.com/news/2025/02/10/thai-swiss-us-operation-nets-hackers-behind-1000-cyber-attacks/The group deployed Phobos ransomware against 17 Swiss companies between April 30, 2023, and October 26, 2024. Their operation involved unauthorized access to victims’ networks, data theft, and encryption of files. The hackers demanded cryptocurrency payments for decryption keys and threatened to publish stolen data if ransoms weren’t paid. They also used cryptocurrency mixing services to obscure transaction trails.
After ~300,000 messages and an estimated ~3,700 collective hours, someone broke through all 8 levels.
— Jan Leike (@janleike) February 9, 2025
However, a universal jailbreak has yet to be found... https://t.co/xpj2hfGC6W
Add a comment: