August 23, 2022
Seems like .mudge has gone whistleblower on Twitter. Part of the Twitter defense seems to be trying to imply that mudge is incompetent.
Kevin Beaumont has a good thread on the whole thing.
-


-
Entrust, a security company, was extorted by LockBit, a ransomware group. In retaliation a DDoS against LockBit’s site caused down time. The DDoS was done with http requests containing the string “delete entrust motherfuckers”

Background:


-


-
The NY fire department guide to forcible entry.
https://ia800207.us.archive.org/15/items/FDNYforcibleEntryReferenceGuide/FDNY_Forcible_entry_reference_guide.pdf-
Reporting a vuln to CrowdStrike did not go smoothly. The amusing tale
https://www.modzero.com/modlog/archives/2022/08/22/ridiculous_vulnerability_disclosure_process_with_crowdstrike_falcon_sensor/index.html-
The most amusing part of Google’s response to this is how they say they don’t look at photos unless the user takes affirmative action. That action? Adding a photo to their photo album (while cloud syncing is enabled.)


-
github.com/0vercl0k/parac…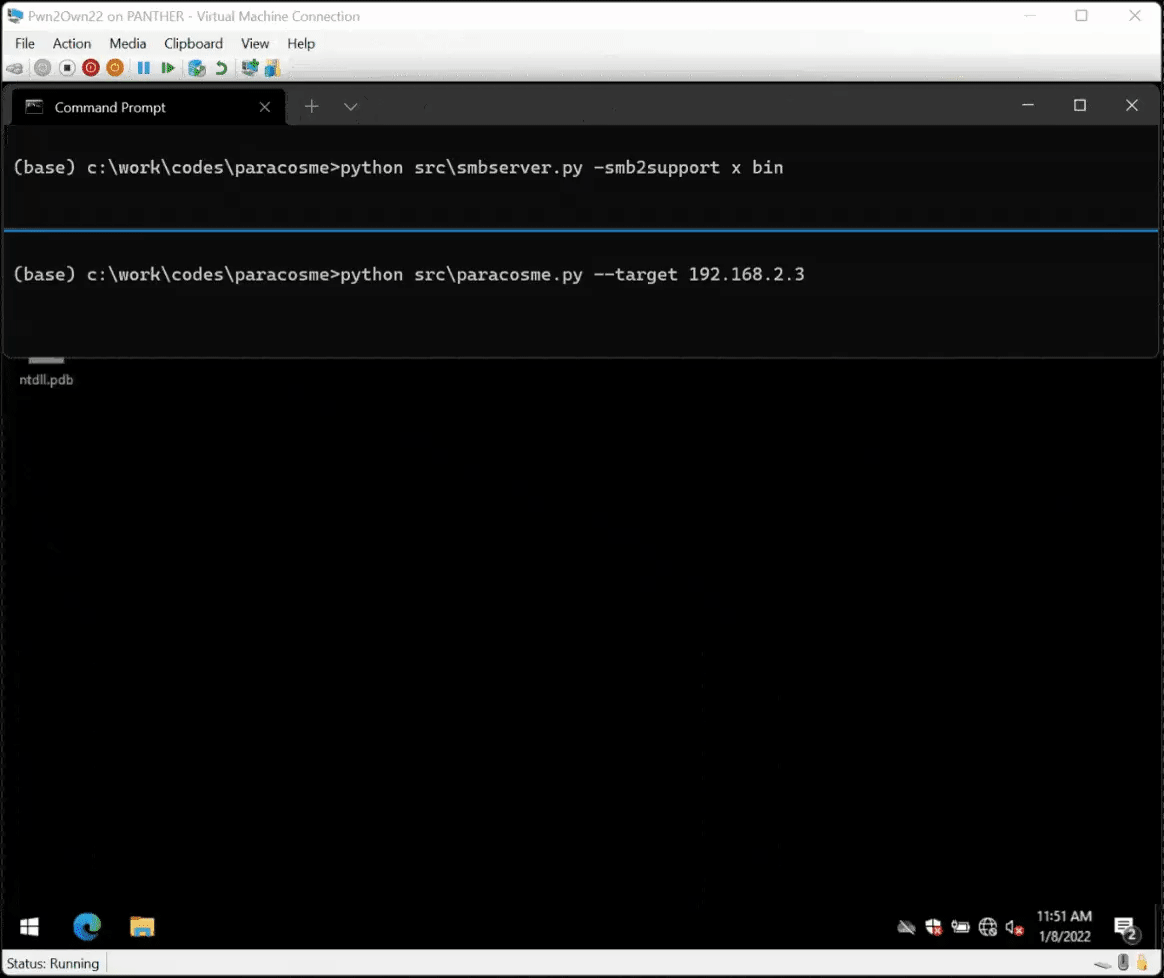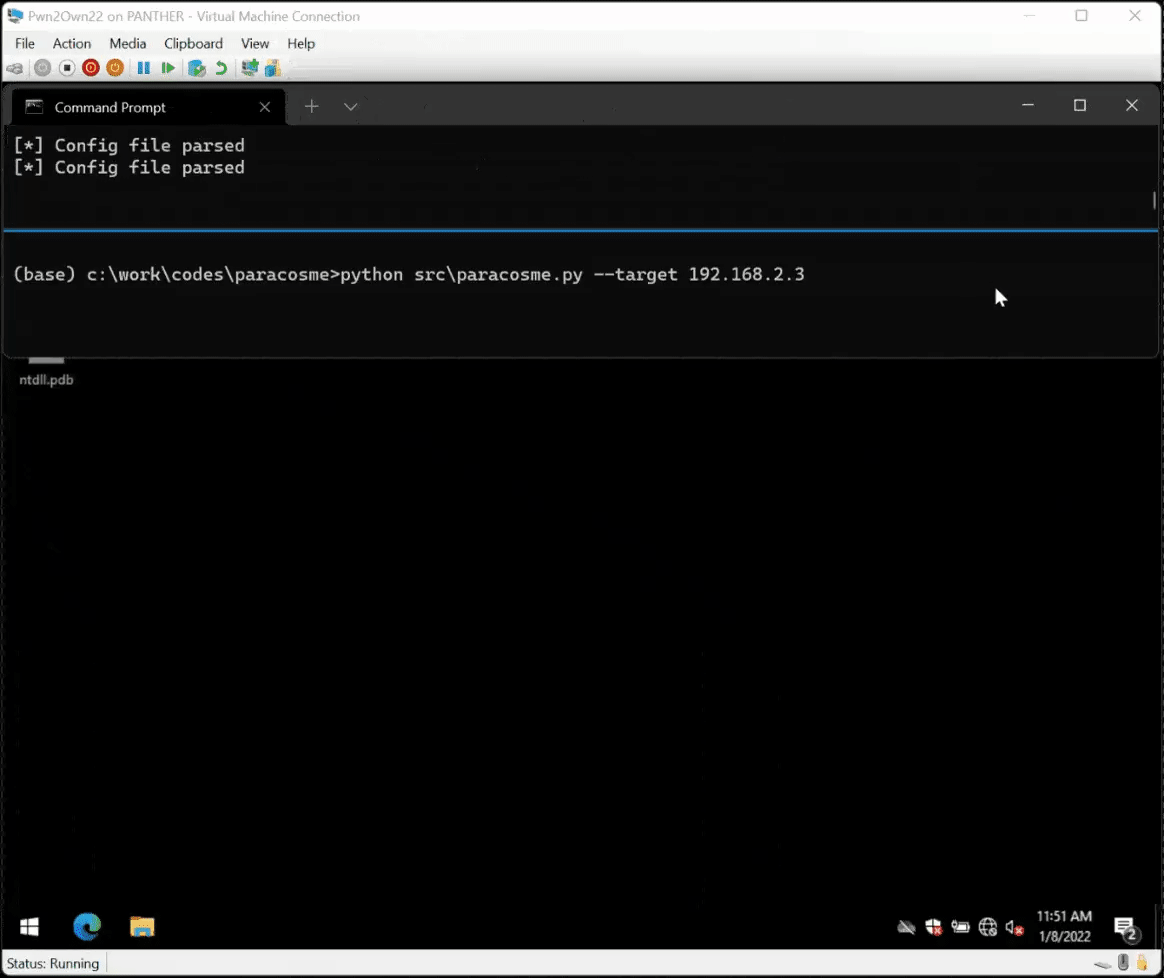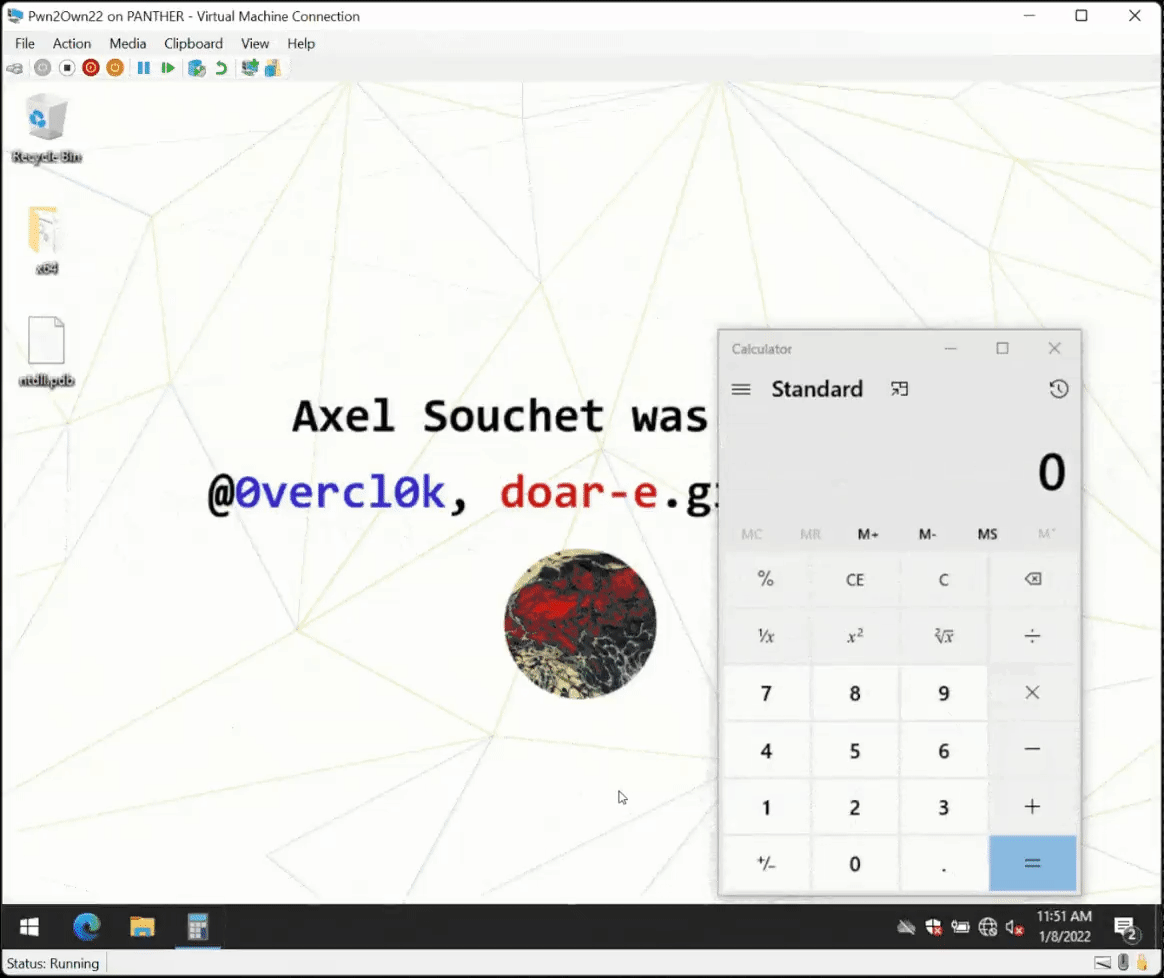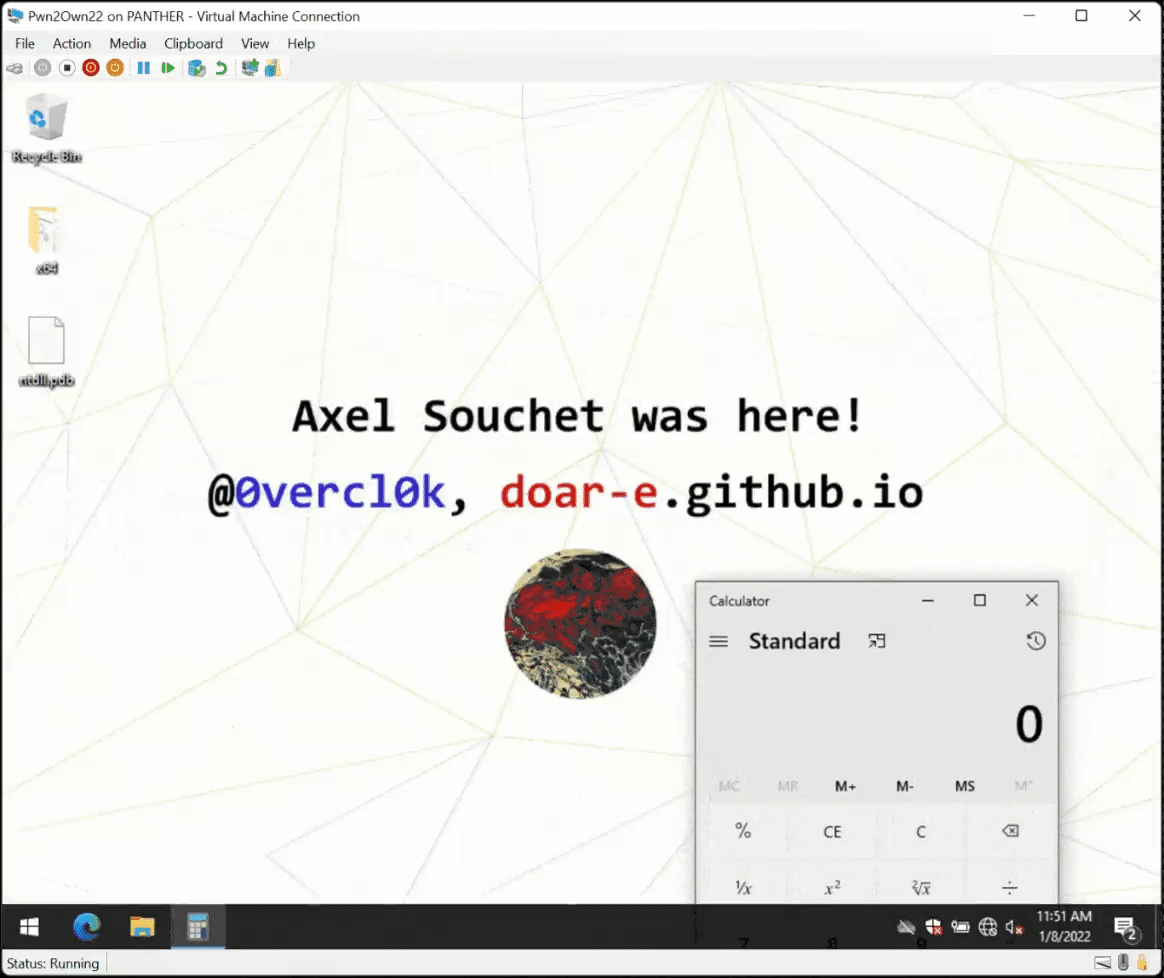
-


-
Best source of up to date daily Ukraine war maps.
https://deepstatemap.live/en-


-


-


-
viralpostgenerator.com

-


-


-

-
-






Add a comment: