April 22, 2022
Some good news on software supply chain security.


A reasonable debate to be had on the topic.




It turns out the Air Force can develop a new UAV in weeks when they need to.


Research on how people actually interact with YouTube suggests that there isn’t a “rabbit hole” and… idk. I’m not convinced. Just, anecdotally, it is obvious that people do rabbit hole. They start on something and it gets reinforced and they dive in. So, maybe it isn’t the YT algorithm with “play next”… but there’s definitely some behaviour pattern that exists. It would be good to have an understanding of that.
The research isn’t perfect, and has some issues according to disinformation researcher I respect.


And there is some data which suggests it is wrong in cases. Jury is still out, and whenever there’s a finding which seems really counter to evidence/experience it’s good to be a bit sceptical about the claims.


I love the aesthetics of propaganda posters.
Weird news in the cybers. A crypto startup in Kyiv has built a multi platform LOIC clone, allowing swarms of ppl to collaboratively DDoS targets (presumably in Russia.)
If they really wanted to help out they would get Putin into NFTs, or convince him that he can solve his Army corruption problem with blockchain.

Inside the Ukrainian Crypto Startup Waging Cyberwar on Russia
Hacken helps crypto businesses with cybersecurity. Now, with the war at home, it’s also leading a guerilla offensive against the Russian internet.
Phones are bad for privacy. Part some-huge-number in a series.
Anomaly Six Demo’d Surveillance Powers by Spying on CIA
Anomaly Six claims to monitor the movements of billions of phones around the world and unmask spies with the press of a button.
Analysis of an exploit used in a recent crypto heist. The vulnerable contract had a sort of… time of check time of use bug, plus… some other stuff…
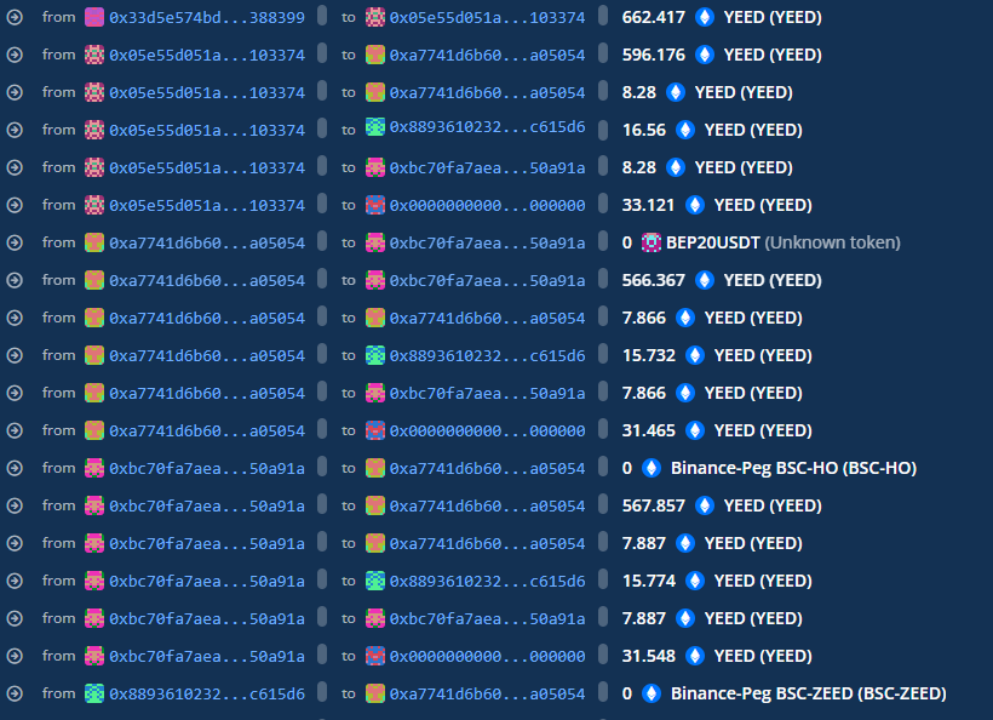
Beosin’s Analysis of the ZEED Exploit : The hacker has self-destructed the contract before transferring funds out | by Beosin | Medium
On April 21th, 2022, according to Beosin EagleEye, ZEED’s contract on BNB Chain was exploited for about $100M. Beosin security team…
Offensive con talks are trickling out.
Channel available here:
https://www.youtube.com/channel/UCMNvAtT4ak2azKNk6UlB1QQ
Lapsus$ stole T-Mobile source code. I guess they can compile and release their own telco now??
Leaked Chats Show LAPSUS$ Stole T-Mobile Source Code – Krebs on Security
https://krebsonsecurity.com/2022/04/leaked-chats-show-lapsus-stole-t-mobile-source-code/



Add a comment: