April 15, 2025
April 15, 2025
"Stuxnet still flunks the test of cyberwar, as I argued in 2013: It was not a disruptive incident, technology did not cause offense to dominate, the attacker was not a weak asymmetric actor; and deterrence shaped the attacker’s decisions." https://www.tandfonline.com/doi/full/10.1080/01402390.2025.2481447?src=exp-la#d1e1997
— Shashank Joshi (@shashj.bsky.social) 2025-04-14T12:39:04.990Z
The EU is rather slow on the uptake. 12 years ago: "According to SPIEGEL information, the US placed bugs in the EU representation in Washington and infiltrated its computer network. Cyber attacks were also perpetrated against Brussels in New York and Washington." https://www.spiegel.de/international/europe/nsa-spied-on-european-union-offices-a-908590.html [contains quote post or other embedded content]
— Shashank Joshi (@shashj.bsky.social) 2025-04-14T12:23:46.081Z
"A little over five years ago, EU security experts noticed several telephone calls that were apparently targeting the remote maintenance system in the Justus Lipsius Building, where the EU Council of Ministers and the European Council are located." https://www.spiegel.de/international/europe/nsa-spied-on-european-union-offices-a-908590.html
— Shashank Joshi (@shashj.bsky.social) 2025-04-14T12:24:52.176Z
On the importance of cultural "mimicry" to the work of illegals and non-official cover intelligence officers. https://www.tandfonline.com/doi/full/10.1080/02684527.2025.2485806?needAccess=true#d1e529
— Shashank Joshi (@shashj.bsky.social) 2025-04-14T10:42:53.779Z
misleading, naive; apples and oranges; different user bases => different design choices and trade-offs; 'security audits' matter much less than years of community reviews; PR... https://t.co/56UwWQD13Q
— JP Aumasson (@veorq) April 15, 2025
https://t.co/9bXLziS6NH pic.twitter.com/Oj3Bst7m82
— JP Aumasson (@veorq) April 15, 2025
"After the daring Iraq ride, the CIA worked with Polish spies globally, especially because Poles held a rare advantage of communist-era intelligence networks located in countries like North Korea, Cuba, Nigeria, Iran, and Angola and [Palestine]." https://t.co/lKrZdCO4cW
— Shashank Joshi (@shashj) April 15, 2025
Before the Internet, this was our online distribution center (Software Creations BBS located in Boston), which cost us $20k a month to run! This was managed by my good friend back then, Dan Linton, in his basement. pic.twitter.com/uqWtAZU2zn
— Scott Miller - Apogee/3D Realms Founder ☢️ (@ScottApogee) April 14, 2025
HyperDbg v0.13.1 has been released. 💫
— HyperDbg (@HyperDbg) April 13, 2025
This version includes improved mitigations against anti-hypervisor techniques used to detect nested virtualization environments, along with various bug fixes.
Check it out:https://t.co/3rsIefo0qv
Blackpill
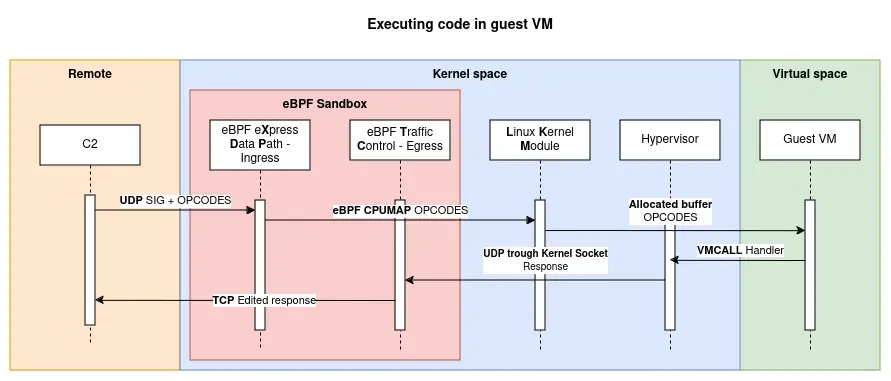
blackpill: A stealthy Linux rootkit made in Rust
blackpill is a Linux kernel rootkit in Rust using a custom made type-2 hypervisor, eBPF XDP and TC programs
GitHub - DualHorizon/blackpill: A Linux kernel rootkit in Rust using a custom made type-2 hypervisor, eBPF XDP and TC programs
A Linux kernel rootkit in Rust using a custom made type-2 hypervisor, eBPF XDP and TC programs - DualHorizon/blackpill
Slides of my talk at #Zer0Con2025!
— Alexander Popov (@a13xp0p0v) April 14, 2025
⚡️ Kernel-Hack-Drill: Environment For Developing Linux Kernel Exploits ⚡️
I presented the kernel-hack-drill open-source project and showed how it helped me to exploit CVE-2024-50264 in the Linux kernel.
Enjoy!https://t.co/84DqT4rdvm pic.twitter.com/2RVSRxFlvD
Slides of my talk at #Zer0Con2025!
— Alexander Popov (@a13xp0p0v) April 14, 2025
⚡️ Kernel-Hack-Drill: Environment For Developing Linux Kernel Exploits ⚡️
I presented the kernel-hack-drill open-source project and showed how it helped me to exploit CVE-2024-50264 in the Linux kernel.
Enjoy!https://t.co/84DqT4rdvm pic.twitter.com/2RVSRxFlvD
Start the conversation: