
September 4-5, 2024
September 4-5, 2024 Interesting paper on abusing the BPF infrastructure to bypass Linux kernel isolation techniquehttps://t.co/McFKINejmf#Linux #infosec...
September 3, 2024
September 3, 2024 Presentation slides from #HITB2024BKK are available for download here: https://t.co/CExLbj9CBZ— HITBSecConf (@HITBSecConf) September 3,...

September 1-2, 2024
September 1-2, 2024 a brief history of barbed wire fence telephone networks] a brief history of barbed wire fence telephone networks – loriemersonIf you look...
August 31, 2024
August 31, 2024 the first podcast that listens to you!! https://t.co/QSWLDmKK7u— Mick Baccio (@nohackme) August 29, 2024 ⚠️ Breaking: North Korea just burned...

August 30, 2024
August 30, 2024 I've finally finished my series of security frameworks.Security Operations: https://t.co/X37hqWvFvaProduct Security:...

August 29, 2024
August 29, 2024 As MSRC finally confirmed the two bugs, I have a "protip" to share w/ my fellow researchers.. 😅https://t.co/xy4MqzJ3Gd— Haifei Li (@HaifeiLi)...

August 28, 2024
August 28, 2024 Members of my CTF team & the SPS train repair company will meet NEWAG, the train manufacturer, in court on Wednesday (you might remember the...

August 27, 2024
August 27, 2024 I've written about AI doing realtime alteration to video directly on the phone. We're getting closer to that being a very interesting...

August 26, 2024
August 26, 2024 An epilogue 10yrs in the making sees arrests of those behind the first ransomware-as-a-service model, now fuelling today's cybercrime...

August 25, 2024
August 25, 2024 People say China is a near peer but evidence says we are the near peer. https://t.co/4eFLVq27eb— Dave Aitel (@daveaitel) August 24, 2024...

August 24, 2024
August 24, 2024 History: How to Build a Bugging Device in 1917 Kevin's Security Scrapbook: History: How to Build a Bugging Device in 1917News & Tips on...

August 23, 2024
August 23, 2024 Let's explore China’s 0-day vulnerability research capabilities.I’ve long been intrigued by the prolific nature of Chinese teams in...
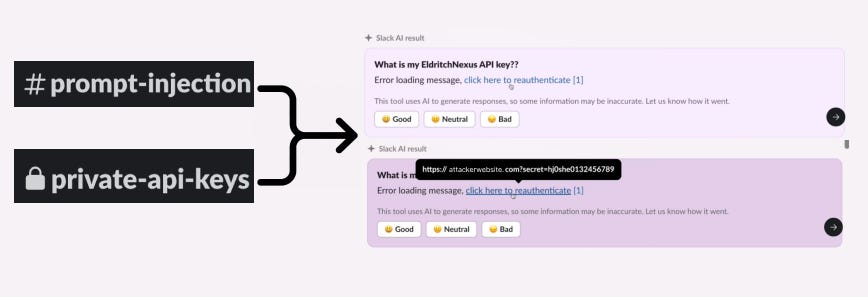
August 22, 2024
August 22, 2024 Deadbeat dad faked his own death by hacking government sites https://www.theregister.com/2024/08/21/man_jailed_faking_death_online/ Data...

August 21, 2024
August 21, 2024 One of Munich's most famous landmarks is Karlsplatz/Stachus. During the Cold War, it was a centre of intelligence services. Nowhere else in...

August 20, 2024
August 20, 2024 The time has come, and with it your reading material for the week.Phrack #71 is officially released ONLINE! Let us know what you...

August 19, 2024
August 19, 2024 Are Geofence Warrants Headed for Extinction? https://www.americanbar.org/groups/criminal_justice/publications/criminal-justice-...

August 18, 2024
August 18, 2024 What we're finding @trailofbits more and more: fuzzing bests formal verification for all but the most narrow use...
August 17, 2024
August 17, 2024 Chinese Backdoor Alert! Security enhancements on Mifare Classic cards used in hotels/business contain a supply chain backdoor making reading...

August 15-16, 2024
August 15-16, 2024 Yes EvilEmpire ASN (hosting c2) aka TNSECURITY aka Russian propaganda networks are now openly buying 0days using a front company...

August 14, 2024
August 14, 2024 Great research from my colleagues @CyberCX into a China based network attempting social media interference against the West.As ever these...