PowerShell Potluck - September 2024
Welcome back to another PowerShell Potluck, and you didn't have to bring a thing, other than a little curiosity and a willingness to try new things. Here's a round-up of PowerShell buffet items I found interesting this month.
PowerShell World
There is a lot of activity in the PowerShell community in Europe. And in many cases you don't even have to leave your desk to participate. There is a new umbrella organization called PowerShell World on Meetup.com that is "dedicated to bringing together professionals with a passion for PowerShell, DSC, Configuration Management, DevOps, Infrastructure as Code, Continuous Delivery, on-prem and Cloud Infrastructure." If this sounds like you, I encourage you to join the group. The big upcoming event is the PSConfEU MiniCon on October 15, 2024. This is a free virtual event, although you still need to register.
PwshSpectreConsole
Here is a very interesting project that came across my social media feeds. The PwshSpectreConsole module has a new release. I was not familiar with this module. It is a PowerShell wrapper for the [Spectre.Console library]https://spectreconsole.net/) which allows you to do some very cool colorful and graphical things in a console.
If you want a taste, install the module on PowerShell 7 and run Start-SpectreDemo.
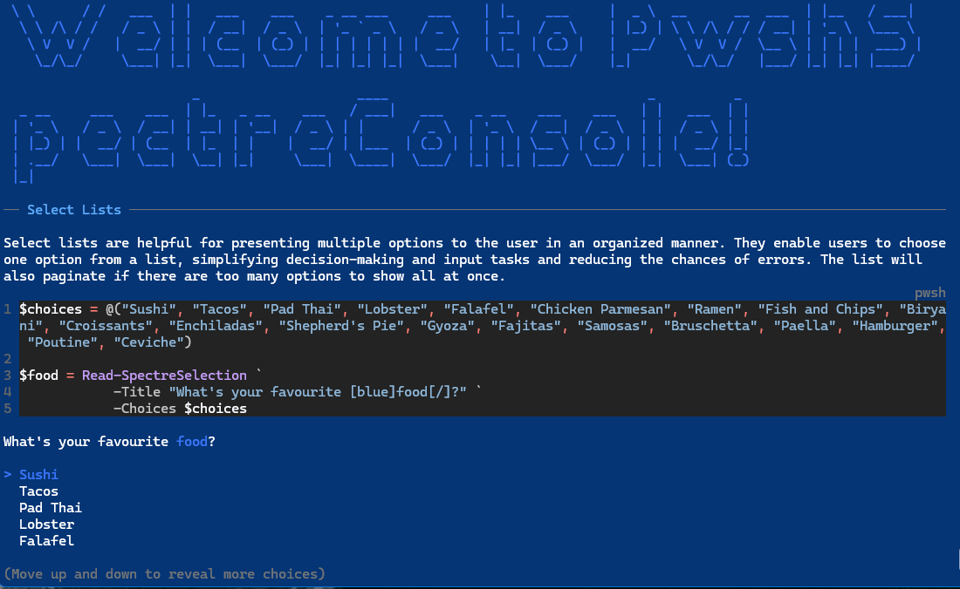
This will give you a taste of what you can do. Full documentation can be found at https://pwshspectreconsole.com/
I'm hoping to explore this module this fall and see what I can come up with. Don't be surprised if there is future content on this.
Map WSL drive
Here's a little trick I learned this month which might be useful if you use the Windows Subsystem for Linux (WSL). You can map a drive letter to your WSL installation. For example, I have Ubuntu installed so I can test cross-platform code. You should be able to use New-PSDrive to map a file system drive.
New-PSDrive U filesystem \\wsl$\Ubuntu
If the WSL host is not running, this will start it. Now I can navigate the Ubuntu file system using the U: drive.
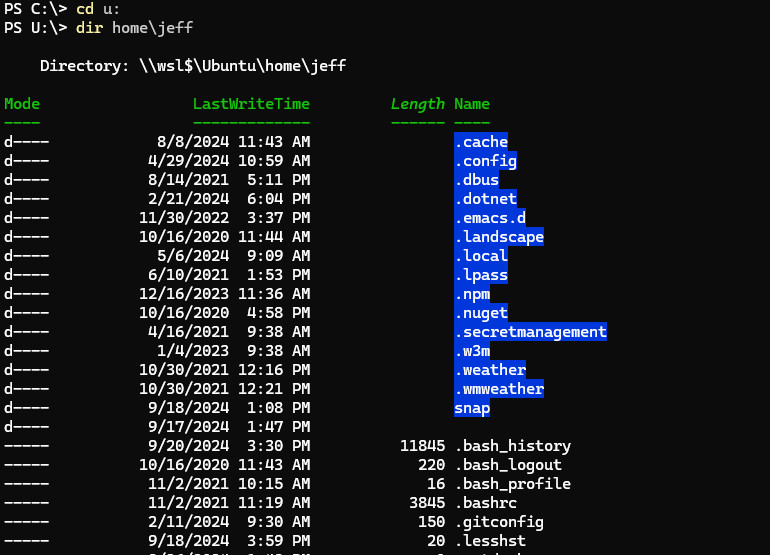
This makes it very convenient to move files between my Windows and Linux environments.
Windows Terminal Updates
I also read about recent updates to Windows Terminal on 4SysOps.com You are using Windows Terminal, right? The latest releases include some intriguing features.
ScratchPad
You can now open a scratchpad in Windows Terminal. This is a floating window that you can use to jot down notes or run commands. You'll need to manually edit your settings file. I added:
{
"command":
{
"action": "splitPane",
"type": "scratchpad"
},
"keys": "ctrl+alt+o",
"name": "Open split scratchpad"
},
In Windows Terminal, I can press Ctrl+Alt+O to open a scratchpad in a split pane.
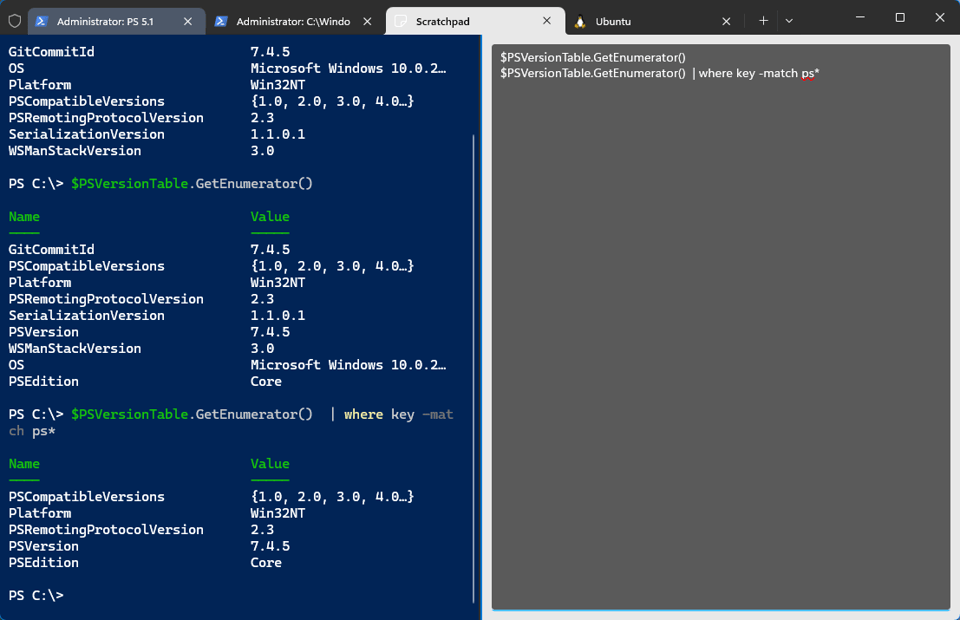
To close the scratch pad, select it and press "Ctrl+Shift+W". I also added a setting to run a scratchpad as a separate tab.
{
"command": {
"action": "newTab",
"type": "scratchpad"
},
"keys": "ctrl+alt+;",
"name": "Open scratchpad tab"
},
This gives me a place to jot notes and temporarily hold data while I work.
Snippets
Another cool feature, which I have used in the past, but perhaps is a bit more refined now is the use of code snippets. The idea is that you might have a string of text you want to insert at a prompt. For example, I often will open a Windows Terminal session with a remote connection to a VM that is running an older operating system and I need to adjust my TLS settings. I don't want to have to type "[Net.ServicePointManager]::SecurityProtocol = [Net.SecurityProtocolType]::Tls12" so I created a snippet. Again, you need to edit your Windows Terminal JSON file and add a command under Actions.
{
"command": {
"action": "sendInput",
"input": "[Net.ServicePointManager]::SecurityProtocol = [Net.SecurityProtocolType]::Tls12"
},
"keys": "ctrl+t",
"name": "Set TLS2"
},
In any Windows Terminal session, I can press Ctrl+T and the string will be sent to the prompt. This is a great idea for any command you run often, especially one that is tedious to type.
Show Your Key Bindings
You can always find your action by opening the command palette, but I'm a big fan of key bindings. Where it gets tricky is determining what key bindings might already be in use. And you also have to take PSReadLine into account. Fortunately, this is easy to discover.
Get-PSReadLineKeyHandler | Sort Key | Select-Object Key,Function,Description
Windows Terminal key bindings are stored in the settings file. Here is some code you can use to see what you have defined.
$json = "$env:LOCALAPPDATA\Packages\Microsoft.WindowsTerminal_8wekyb3d8bbwe\LocalState\settings.json"
$settings = Get-Content $json | ConvertFrom-Json
$r = $settings.Actions | Select-Object @{Name="Name";Expression = {$_.name }},
@{Name="Action";Expression={$_.command.Action }},
@{Name="Key";Expression={$_.keys }},
@{Name="Type";Expression={$_.command.Type }},
@{Name="Profile";Expression={$_.command.profile }},
@{Name="Input";Expression={$_.command.Input }}
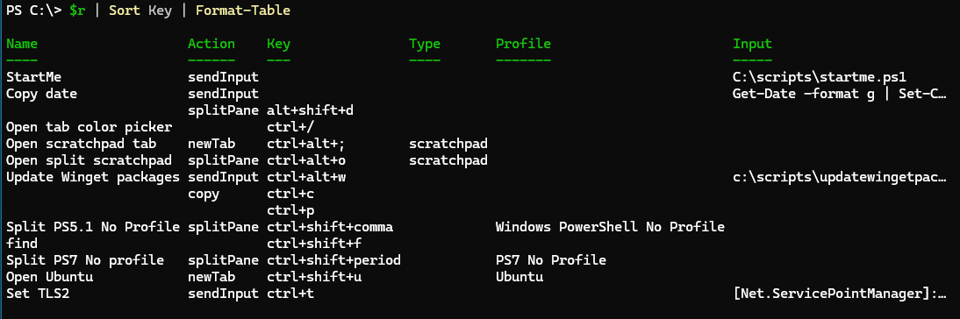
This is also a nice way to see your custom actions. Unfortunately, I haven't found a convenient way to list Windows Terminal default key bindings.
You can find official documentation on custom actions at https://learn.microsoft.com/en-us/windows/terminal/customize-settings/actions.
Scripting Homework
I'm going to wrap-up this month with a little scripting challenge. Think of it as homework. The best way to learn something is to do it. This is something you can accomplish in a PowerShell script file, although if you want to incorporate some PowerShell functions, go right ahead. The end result should meet the following requirements:
Create a key under HKCU: called
PSProfile.Under this key, create a key for each of the four PowerShell profile scripts, e.g.
AllUsersAllHosts.Under each key, add values for the file path, the file size, the last modified date, and an MD5 file hash of the profile script.
Store the file size as a
QWord.You will need to account for profiles that may not exist.
If your profile is using a symbolic link, you may need to resolve the link to get the actual file path and size.
For extra credit bragging rights, store the profile script contents as a binary value in the registry and write a function to or script to view the binary key value.
I'll share my solutions next month. Good luck and have fun with it.
If you are a free subscriber, I hope you’ll consider upgrading to a premium subscription which will give you full access to all content including the archive.
Add a comment: