De-influencing Security for our wellbeing
The last week has brought more bad news and horror to the world.Many people we work with or know will have friends or family affected, or will be just incredibly sad about yet more human suffering. I mention this not because I have answers,or because I think my opinions will help. But because I think a lot about how we as security practitioners can sensitively navigate our professional spaces. Do we give people space to deal with the constant awfulness that the last few years have brought? If someone is overwhelmed by the news and comes in to a phishing sim, or a lecture about mandatory training or not doing xyz, or sees yet another post about someone’s “success”,how do they feel? How are we caring for each other and the ones we work with? So this week,I want to talk about making things better for each other.
De- Influencing Security
Fun non-scientific fact: I find 8/10 straight couples who post date night and other loved up social posts are mostly miserable together.Believe that or not, we have a society of influencers, marketing and filters. By design, so that we feel less than, buy more and want to follow trends. In fact, social media has made us so unused to seeing unfiltered pictures, that children have deteriorating mental health and self worth, and we are often shocked how people look in real life.
Now what has this got to do with security? Let me explain:I feel we are,especially with security education,chasing an unrealistic “influencer” dream. We should de-influence security, remove the instagram effect of projecting the perfect.We can and should focus on quiet work, done well, and work that has outcomes. Your work can be as amazingly effective and worthwhile just working with 4 people,as it is 4000 people. You don’t need to have fancy dashboards and big events to be doing important work.
The shiny event or project someone boasts of in an blog, post or talk is often all output. It is why people like Anna Delvey, SBF or Elizabeth Holmes can be so successful for a time. The illusion isn’t questioned.

I would love to see more honesty about the challenges and real projects that we do. Even if you are in some huge global organisation,some of your most impactful work will be with small groups of people. Of course, we should celebrate really big projects too. But the real work, the work we all do and are proud of every day?- that matters too.
I once got a group of 20 people to use a password manager and I was so proud of the work I did to get their trust and engagement. You might have convinced one person to adopt a change, or one team in one region might be working in a new way because of you. That is amazing work, not just because it has impact, but because of the relationships that you develop from it.
Above all, I would like us to talk more about how we make people feel, which is so much more important than some metric or cool photo on LinkedIn. In 50-100 years, you will be forgotten, all of us will. Even if we win big awards or are in politics or other powerful roles. So while you are remembered, let’s make it for being helpful, thoughtful and good.
Accepting the limitations that we work with
I think we also need more honesty around what workplaces expect and how much we can realistically accomplish. To expand on this point, I recommend you read this newsletter by Sara Wachter-Boetcher. Sara focusses on UX,not security, but her points will likely resonate with you:
that we need to focus on knowing our worth,not arguing to prove our value. Building connections works better than being adversarial and can bring change over time.
We can just do the work and be loud about it. If you know something will work, or want to run a pilot, go ahead.
Sometimes the goals of the business will run against your goals. Just focus on what you CAN change and do.
Security education/risk/culture can be a role where you are terrified of not doing enough. Of not proving your value. There will always be someone demanding that you make a training on a new criminal scam, or put out comms about something else that is a business or consumer concern, put posters up(pls no) or send ten thousand emails (even more no). Then people are obsessed with how to measure their work. It is a challenge, but find your sponsors and do the work that you know needs to be done. Forget the fancy vanity metrics. If you know that something needs to be done, go ahead and do that. This is where sponsors for your work, and great relationships prove their worth. Your connections, supporters and cheerleaders will speak to your impact and value more than any dashboard ever will.
And support the ones who are doing that quiet, slow less fancy work.We are making a problem for ourselves if we don’t celebrate quietly effective work.If you want cheerleaders, put that energy out there for others too.
Building trust
I have written about the new NIST Human Centred Cybersecurity Program, but it is worth mentioning again in this context. The program focusses on usability, collaboration and accessibility of cybersecurity information. It is putting the people we work with first, before targets and metrics and “how it has always been done’.
I think we often prescribe, lecture and mandate. I don’t think we actively listen enough.We don’t seek to understand the humans we deal with. When you work with young people, psychologists advise us to be more of a partner than a lecturer. Some of the advice is resumed in this infographic I made for a course:
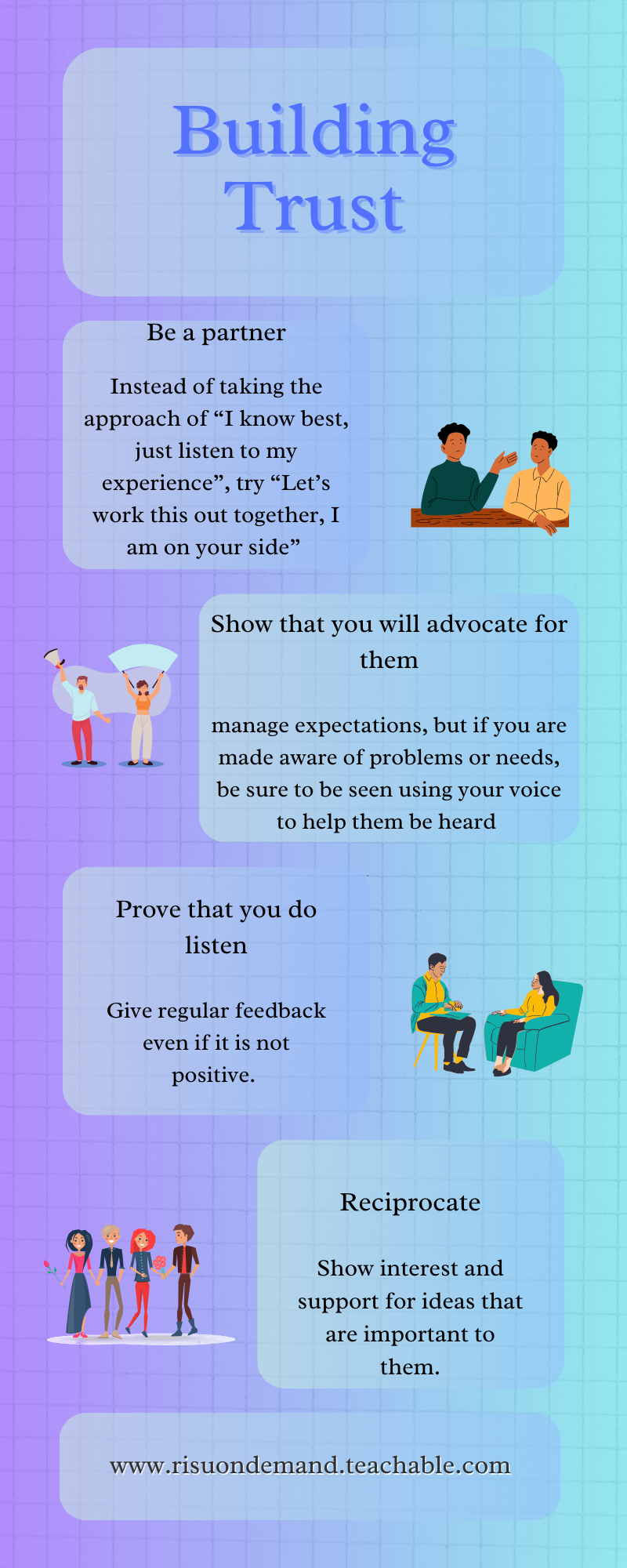
It is one thing to say that humans need frameworks to protect them, like yellow lines to nudge them to safety, or systems that won’t work if you are driving, or auto pilot to fly a plane.
But we need to go further. We need to acknowledge this very uncertain world. Then we need to make sure that we are a solution not a problem.
How can we do this? I won’t pretend that I think it is easy. Many companies want to focus on protecting their assets first, more than helping employees to feel included, safe and even interested in security education. For example, LinkedIn spam, especially containing malware is now in the news.But for years it has been hard to get some leaders to endorse social media security education, unless it related to work use.
Add to this the fact that security education can only be as good as the ones doing it. And we need to be in balanced rooms, aware of how people are using the internet.If your security team don’t use WhatsApp or Snap, and have no idea about parental controls or the latest ways people are using tech.. they can’t make appropriate content for those people.I say this thinking of my own practice, where I have no idea how Snapchat works and even less desire to do so! BUT I do collaborate with those that do understand it.
My golden rule is that you should try to focus on only having 3 steps for any process you want to explain, and that it should take no longer than 5 minutes.

The point of saying all of this is to help us remember that amid all this human risk and other talk, the humans matter.We shouldn’t be adding stress to their days. We can’t expect people to listen when we just mandate training or lecture. And we must treat people with compassion and respect. We have to be active partners who listen and sit alongside people. Because the world is a lot right now.
Just and Blame Culture
Steven Shorrock is an expert in Human Factors,and this newsletter on just and blame culture is an interesting read.When we think about building trust, and how we communicate, we need to think about the various cultures that may exist in the teams or communities we work with. One organisation might have many cultures. I am glad to see more cybersecurity professionals working with human factors experts, as it can only improve our work.
October is Domestic Violence Awareness Month
A great idea for your October cyber month shenanigans would be to focus on raising awareness of tech abuse in intimate partner abuse. As a survivor of domestic abuse, this is a topic close to my heart.I have spoken at a number of conferences over the years about recognising abuse and how to help people. I still don’t feel that we as security practitioners do enough to help.
Tech abuse is increasingly common and is often done via child “safety” apps or family sharing apps. For example, tracking location and setting limits on what might be on a device. This is why I am always cautious about family “safety” apps.I consider them mostly legalised stalking apps. I make sure to highlight the importance of consent and opting out. My children for example, are aware that I can track their location via Apple’s Find My function. They are all old enough to be able to turn this option off.But the important thing is that they are aware. I also do not use this to scare or control them.
Perhaps the most troubling aspect of doing work in recognising tech abuse is how normalised harm is, even in tech circles. I am often told in sessions that people actively look through a partner’s device, control heat and light and think it is funny to scare people via cameras and speakers.There is a lot of work that we can do in security education to help people to understand consent and that just because you can, does not mean that you should.
A good baseline of advice to help people avoid tech abuse is:
Set up new smart devices such as lights, locks or heating with shared controls. Avoid just one person having overall control.
If someone in your life is limiting your access to light, heat or basic human needs, you can seek help from many places at work/in stores, healthcare settings or transport hubs.( Make sure that your audience is aware of where they can get help in their region.)
Cars now come with apps that can track location,tyre pressure and even remote start and stop the vehicle. Be aware of this as there is currently no way to remove this from the car.
Domestic abuse support groups can help you to get a spare device and set it up, if you don’t have the support to do that.
Our phones are now very private extensions of ourselves, with banking, travel and healthcare information on them. It is completely normal and right to keep your device locked and private.
It can be useful to set up “after death” plans- where you give someone permissions to access your devices or password manager if something should happen to you. Doing this can avoid you having to give someone your PIN or passwords “just in case”.
Podcasts
Hidden brain this week is about How to spot a scam
Discarded discusses misinformation
IRL by Mozilla has a series on AI that is worth your time
Risky Biz talks to the head of Yubico about the MGM hack
Speaking of Psychology is about celebrity crushes and parasocial relationships- interesting when we think about how we interact online,who we trust etc.
I wish you all a good week ahead,when no emails find you. I don’t think things are going to miraculously get better in the world. But I do think that if we all try to think about what other people might be experiencing, we can make a difference we might not realise.