Refuge's Tech Safety Newsletter May 2025
17th of May is World Telecommunication & Information Society Day
Each year, World Telecommunication and
Information Society Day celebrates the power of
connection. It commemorates the founding of the
International Telecommunication Union in 1865, a
moment that transformed human communication.
From the sending of the first telegraphs to the development of 5G, telecommunications have bridged the distances between us and created a more connected world. However, for some individuals, the same technologies that are meant to empower can create hostile environments that feel overwhelming and complicated.
Communication technology has evolved rapidly, starting with the telegraph in 1844 and the telephone in 1876. By 1901, wireless radio messages crossed the Atlantic, and in 1973, the first mobile phone call was made. The 1990s and 2000s brought the internet, SMS, and mobile phones, transforming how we connect. In the 2010s, smartphones and social media took over, raising new risks. Now in the 2020s, 5G, AI, smart devices and the Internet of Things have pushed connectivity further, along with the risks that come with them.
Telecommunications extend far beyond just cables,
towers, and data plans; they are embedded in our daily lives. For survivors of domestic abuse, a mobile phone or access to the internet can mean the difference between isolation and access, and between threat and safety. A phone can serve as a lifeline, providing access to helplines, refuge, emergency services, or even just a trusted friend. However, in the hands of an abuser, the same mobile phone can become a weapon.
Impact on Survivors
Survivors often report being tracked through their mobile phones, fearing the presence of stalkerware, and difficulties with terminating fraudulent or coerced phone contracts taken out in their name. Many also face ongoing harassment through calls and text messages, all while navigating customer service systems that leave them feeling trapped and without the necessary support. This is not uncommon, and is a growing form of technology-facilitated abuse which requires urgent action from the industry.
Telecom providers have the tools, reach, and influence to drive real change. Survivors require not just better technology, but also safer systems.
Here's how telecom companies can lead the way:
Make telecoms a priority bill: This is vital to ensure that survivors are not disconnected which often results in survivors being unable to engage with support services leaving them isolated and at risk of further abuse.
Safe exits, no penalties: Allow survivors to separate accounts and transfer numbers without jeopardising their safety or financial stability.
Survivor-centred support: Provide discreet and secure processes for account recovery and privacy control.
Trained staff: Educate frontline workers to recognise red flags and respond with empathy.
Privacy-first design: Simplify the process for disabling location sharing, hiding call logs, and controlling access.
Partnership with lived experience: Collaborate with survivors and domestic violence organisations to co-create safety policies.

Connection without safety is not true progress. Survivors deserve both.
Refuge is a frontline charity supporting survivors of domestic abuse, with specialised knowledge in technology-facilitated and economic abuse. Our team offers training for telecoms providers looking to understand how their systems impact survivors, and we can help you prioritise survivor safety every step of the way. If you are ready to contribute to a safer, more informed future, we would love to hear from you.
World Password Day
Getting back to basics with our cyber hygiene
World Password Day falls on the first Thursday in May each year, making it the 1st of May 2025. This is a great opportunity to prompt the importance of using strong and secure passwords and practising good cyber hygiene to keep your accounts safe. Gone are the days of it being safe to use a DOB, pet name or well-known number patterns, these are nowhere near enough to protect you from the intelligence of attacks out there.
You might ask, so, how do I make a strong password to prevent unauthorised access to my accounts?
It is important to use a different password for each account, reusing them is dangerous as data leaks could lead to more confidential accounts being accessed.
Avoid creating variations of the same password, if one is leaked it would be fairly simple to guess variations of this to access other accounts.
Avoid using personal information for a password, so anything other people might know about you, remember those quizzes on social media? As harmless as they may be, it is encouraging people to share personal information online that could lead to password clues.
Use passphrases rather than single passwords, and avoid phrases that can be easily guessed, so you could select three random words: EG: PurpleMacaroniRose.
Passwords need to be long, most tech sites advise using a minimum of 12 but aim for 16-18 characters.
When creating passwords use a combination of numbers, symbols, caps and lower case and avoid switching letters with numbers and symbols that look similar (like a with @) because hackers know this trick. So for our example earlier, you could edit our three words PurpleMacaroniRose to 30Purple*10Macaroni&1Rose!
Now you have that strong password, remember this needs to be a new and different password for every single account.
But how do we remember them?
Avoid writing them down, if someone finds your password book, they have access to all. Consider using a password manager, they can create complex passwords for you and will store your passwords in an encrypted vault. Phones will often come with these built like Apple's keychain. It is important that the account is secure for the password manager to prevent someone from accessing the vault and all of your passwords.
You can also take steps to see if any of your accounts associated with your email have been compromised by using www.haveibeenpwned.com. If you do find information has been breached, make sure you change the password for that account and that you are not using that password anywhere else.
And finally, when reviewing our passwords it’s a good job to take some additional steps to practice good cyber hygiene so, what do we need to be doing?
Use multi-factor authentication where possible
Ensure your operating systems are up to date
Regularly reviewing privacy and security settings on our accounts
Delete apps and accounts you no longer use
Be aware of phishing attacks – phone calls, emails and text messages
Wipe old devices completely before selling them on
Use an antivirus on your devices
Ensure your home Wi-Fi is secure
The Refuge Technology Facilitated Abuse Team can offer support to survivors experiencing concerns around their technology. Support can be found by calling the National Domestic Abuse Helpline on 0808 2000 247 from a safe and secure device where possible, or by visiting our Tech Safety Website www.refugetechsafety.org
Password Generation Game
World Password Day is a great reminder for all of us—young and old—to review how we protect our digital lives. As adults, we have a key role in helping children understand the importance of password strength and cyber hygiene in a way that’s engaging, age-appropriate, and confidence-building.
Whether they’re logging into school platforms, games, or social media (with age-appropriate guidance), children are building their digital footprint early. Weak or reused passwords can put their accounts and their information at risk.
It’s never too early to introduce password safety in a fun, simple, and empowering way.
For World Password Day, try our password generator game below to encourage children and young people to review and strengthen their passwords.
Please Note: for each category you can change out the words and symbols to make this personal for child/young person for better engaged learning and understanding.
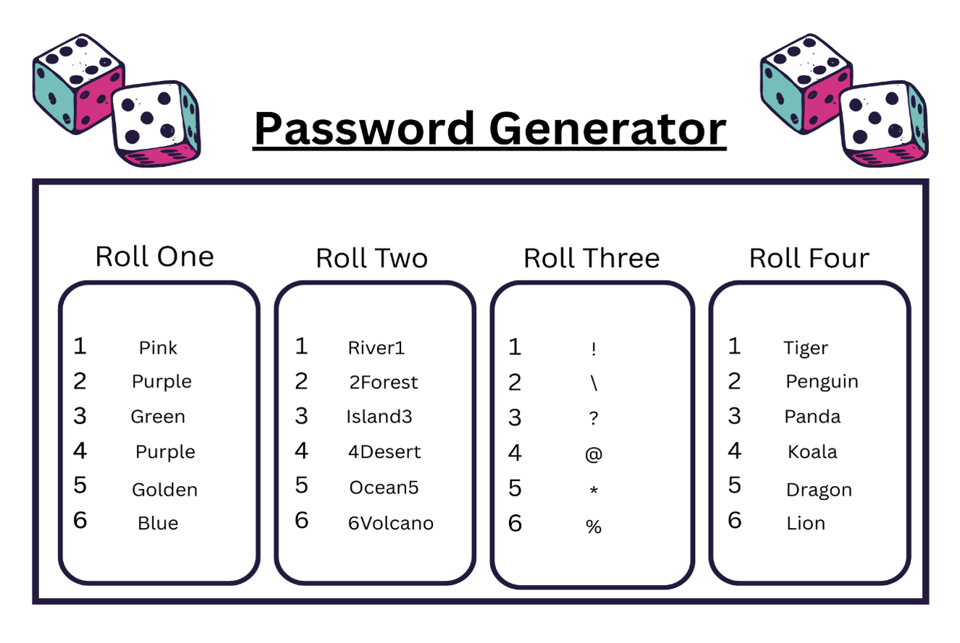
What you need:
1 Dice
How to play:
Roll the dice for each category and the number that is shown on your dice will help develop your new strong password.
Example-
Roll One- 6- Blue
Roll Two- 2 – 2Forest
Roll Three- 1- !
Roll Four-4- Koala
Altogether that makes- Blue2Forest!Koala