Refuge's Tech Safety Newsletter March 2024
New laws on intimate image abuse
From 31st January 2024, the Online Safety Act made the sharing of AI-generated intimate images without consent illegal. Recent reports of sexually explicit ‘deepfake’ images of Taylor Swift circulating in the news have highlighted the reality that women and children are disproportionally targeted by generative AI.
The Act also brought in further changes around sharing and threatening to share intimate images without consent. Sharing intimate images of someone without their consent and with intent to cause distress has been illegal since 2015 and since 2021 it has also been illegal to threaten to share such images thanks to Refuge’s Naked Threat campaign. As a result of sustained campaigning by Refuge and our allies, the new Online Safety Act reforms wider intimate image abuse law:
• It is illegal to share an intimate image without consent. This means it will no longer be necessary to prove the perpetrator’s motivation to cause harm to prosecute. Perpetrators could go to prison for up to 6 months if found guilty, or 2 years if it is proven the perpetrator also intended to cause distress, alarm or humiliation, or shared the image to obtain sexual gratification.
• Survivors of intimate image abuse will be granted automatic lifelong anonymity and automatic eligibility for special measures during the trial i.e. giving evidence via video.
• Sending unsolicited sexual images, also known as ‘cyberflashing’, has been criminalised. However, this offence depends on proof of the perpetrator’s intent to cause harm or gain sexual gratification, which can be difficult to prove.
How to Support Employees Who are Experiencing Technology-Facilitated Abuse
• 1 in 4 women in England and Wales experience domestic abuse at some point in their lives
• Abuse and harassment on social media is one of the most frequently reported issues to Refuge’s tech team
• Of the women and their children Refuge supported in 2020-21, 59% experienced abuse involving technology
• The number of survivors our specialist team supported rose by 258% between 2018 and 2022
• “Even when he’s not physically with me it feels like there’s always the chance he could have gotten into an online space to watch me.”
• “You start to think, ‘Am I the crazy one?’ because it doesn’t feel like anyone takes this kind of abuse seriously.”
• “When you can’t trust tech, you feel isolated in this world..”
• “My ex-husband would control all finances. He used it as a power he had over me to control where I went and with who. It was his way of keeping me at home.”
In the past year, more than two million survivors have reported experiencing domestic abuse, with a significant proportion also enduring technology-facilitated abuse. Given its prevalence, it is highly probable that someone within your workplace or professional circles has been impacted by this increasingly common form of abuse.
Handling disclosures of abuse, particularly those involving technology, requires sensitivity and understanding. When a survivor feels pressured to leave right away, this may cause them to withdraw, and can potentially even worsen the situation. Instead, it is important to provide them with the appropriate support, whilst also acknowledging that leaving an abusive situation requires time and courage.
Technology-facilitated abuse encompasses a broad spectrum of harmful behaviours that leverage modern technology to inflict harm. Abusers often perpetrate multiple forms of abuse, including physical, sexual, psychological, or economic abuse, utilising technology as a means to do this (you can read more about economic abuse here). This could involve anything from hacking into a survivor's phone, engaging in cyberstalking, or using social media platforms, home security systems, or other technological means to exert control over or harm survivors and their children.
It is also important to remember that technology is everywhere. We wear it in our ears, in our pockets, and round our wrists. Most adults always have at least one digital device within reach at all times, therefore perpetrators are able to resort to technology to harass survivors while they are at work. They might bombard them with texts, calls, or emails. They may tamper with their devices by installing stalkerware. They might threaten to distribute intimate images or personal information to their employer, interfering with their ability to work. Even if a survivor is in full-time work, they might still be struggling financially, as they may have been pressured to reduce their working hours, or have the survivor’s income paid directly into their account (you can learn more about how Refuge, in partnership with Payplan, support clients with financial difficulties in our Spotify podcast). In some instances, survivors are even pressured into quitting their job completely. This can make a survivor’s world feel very small, and can have a profound impact on their day to day life.
On the other hand, whilst in an abusive relationship, many survivors find the workplace to be a sanctuary away from abuse. At work, they can physically distance themselves from their abuser, gaining a sense of independence and quite often, normalcy. Supportive colleagues and managers can play a crucial role in this, providing a safe environment where survivors may feel comfortable disclosing their abuse and reaching out for help.
If you work with women, it's inevitable that you will encounter individuals who are or know someone who is experiencing or has experienced domestic abuse. Certain professionals have specific responsibilities in providing support and safeguarding women and children who are at risk. It is essential to familiarise yourself with these obligations, as well as your organisation's policies and procedures for identifying abuse and how to respond to disclosures. You might find our tips on how to speak to survivors and information for professionals useful.
Keep in mind that you might be the first person a woman confides in about her abuse, and it’s important not to miss a crucial opportunity for her to access support. It is paramount to listen to her, believe her, do not judge her, and respond appropriately and safely.
Some things you can do after someone discloses that they are experiencing domestic abuse:
• Listen - Validate her experience, believe her, and reassure her that she is not alone. Disclosing domestic abuse for the first time can be daunting but is a crucial initial step towards seeking help.
• Refrain from pressuring the survivor to leave immediately, recognising that it may not be safe, especially if her devices and accounts are not secure.
• Offer the use of a company phone or your own phone to contact Refuge's 24-hour National Domestic Abuse Helpline at 0808 2000 247. Offer her a safe space to make this call.
• If she works from home, agree on a code word so she can signal when she is in danger and needs you to get help – make it clear what code words mean, for example one could mean ‘call me’, whereas another could mean ‘call the police’.
• Be flexible with working arrangements and allow her to work from the office more often.
• Provide her with a safe device to use so she can safely make calls to services such as domestic abuse support, the police, solicitors, and social services.
• Direct her to Refuge's Tech Safety Guides, Digital Breakup Tool and Home Tech Tool for additional support and resources.
• Encourage her to preserve evidence of the abuse before taking any actions such as deleting messages or posts, restricting the abuser's access to her phone or accounts, or reporting abusive content to tech companies.
• Encourage her to document as much of the abuse as possible, as this could serve as evidence should it ever be reported to the police.
• If you see or hear an assault, or you are worried your friend might be in an emergency situation, call the police immediately on 999.
• Stay updated around trends in technology by reaching out to us and exploring training options tailored to your organisation's needs. Contact us at techabuse@refuge.org.uk to start the conversation.
Tech Abuse Team: Emerging Trends
In recent years, the misuse of technology in the perpetration of domestic abuse has become commonplace – with 84% of survivors experiencing at least one form of technology-facilitated abuse. Perpetrators are finding new and increasingly efficient ways to exert power and control over survivors using technology, leading to a marked need for support services around this issue. Established in 2017, the Technology-Facilitated Abuse and Economic Empowerment team began working directly with survivors of domestic abuse in 2018, with the aim of addressing a critical safety need for survivors working with domestic abuse services.
In the first year following the development of our service, 168 survivors were offered support with issues related to technology-facilitated abuse. The developments in the world of technology combined with the effects of the COVID pandemic accelerated the demand for the team’s services and by 2023, that number had skyrocketed, with 514 survivors needing support from the Tech Abuse team to secure their tech and address concerns around tech abuse. The number of referrals the team receives has not yet come down and many of the survivors the team works with are needing support with increasingly complex forms of technology-facilitated abuse.
To understand the needs of survivors being supported by the Tech Abuse team and the common issues they are facing, our team collects what we call ‘emerging trends’. These trends outline what we are seeing on the front line of domestic abuse and the issues that survivors need the most support with. Using the data the team has collected over 2023, let’s explore the highest key emerging trends we are seeing:
Emerging Trends
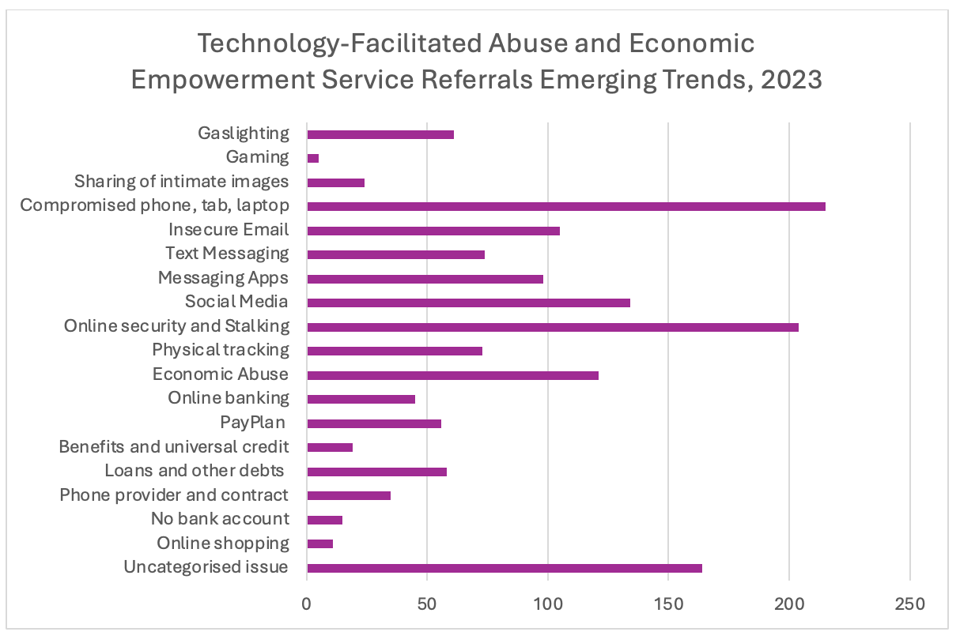
Compromised Devices
Phones, laptops and tablets are key pieces of technology that we all use in daily life. They are also the technology we regularly see being misused by perpetrators to facilitate domestic abuse. These devices hold huge amounts of sensitive information and are often linked to ‘cloud accounts’ that can be easily compromised – giving perpetrators access to information including emails, message logs and log-in details for a host of apps and platforms we commonly use.
The overarching concerns with compromised devices is that often survivors are using these key pieces of technology to seek support, including using them to contact support services or mapping a route to flee. Depending on how that technology has been compromised, a perpetrator can access critical information that can seriously escalate a risk of further harm and abuse.
Online Security and Stalking
Vulnerable online security and stalking are the second most common issue we see when working with survivors experiencing tech abuse. Concerns around shared cloud accounts, linked devices and compromised security settings often mean that a survivor’s online security is vulnerable, and allows that technology to be misused by perpetrators to stalk, monitor and control. Perpetrators may also exploit the survivor’s compromised online security to revoke access to accounts or find information that could either put the survivor at increased risk or violate the survivor’s right to privacy.
This form of abuse is where we commonly see coercive and controlling tactics being used by perpetrators, with perpetrators often gaining access to these accounts by disempowering survivors from understanding security settings and how to keep themselves safe online. We often see perpetrators making survivors believe they do not have the ability to set up their own accounts as they are not ‘tech savvy’ and then using this as a gateway to have complete access and control of that survivor’s accounts, directly leading to perpetrator’s using these accounts to stalk and monitor survivors.
‘Unclassified Issues’
This category of the emerging trends we are seeing is also the most applicable to the fast-changing nature of tech and technology-facilitated abuse. The developments in technology have meant that in the last year, the team are regularly seeing increasingly complex and new forms of technology-facilitated abuse that have not yet been built into our record management and data collection systems.
In this category, some of the most common issues involved Wi-Fi hacks, the misuse of smart home technology (IoT devices) and threats to share intimate images. Perpetrators are increasingly using unique tactics to continue abusing survivors, with technology like smart home tech being incredibly effective in the gaslighting and controlling of survivors. The number of ‘unclassified issues’ coming into the team has highlighted a need to expand our recording management system to cover the ways technology is rapidly changing and becoming increasingly misused.
Looking to the Future: 2024
The emerging trends the team are seeing are consistent with the nature of Refuge’s services and the dynamics of domestic abuse we see daily. Perpetrators are misusing technology to monitor, stalk and harass survivors and the common issues we see, like vulnerable online security and stalking, reflect this. In 2024, the team are expecting to see more complex cases of tech abuse that might involve new methods like AI generated imagery technology being used to manufacture non-consensual intimate images or stalkerware becoming more technologically advanced and readily accessible. The team are regularly updating record management systems and hope to expand them, so that we can have a full picture of what survivors are experiencing. If you are supporting survivors experiencing tech abuse, be sure to keep up to date with the team’s emerging trends so that you can best support!