Cybersecurity Newsletter June 10th 2024
Cybersecurity Newsletter June 10th 2024
In this week’s news: Snowflake security issues are snowballing, Heinekin, NYTimes, and Christies were breached, the Microsoft Recall fiasco, a new PHP exploit, a CSS GitHub exploit, Azure firewall bypasses, and London Hospitals were attacked.
Snowflake’s security problems following a recent spate of customer data thefts are, for want of a better word, snowballing. After Ticketmaster was the first company to link its recent data breach to the cloud data company Snowflake, loan comparison site LendingTree has now confirmed its QuoteWizard subsidiary had data stolen from Snowflake:
https://techcrunch.com/2024/06/07/snowflake-ticketmaster-lendingtree-customer-data-breach/
CSS Injection on GitHub Profiles: From Unicode Exploits to New Bypass Techniques:
https://stevemats.medium.com/css-injection-on-github-profiles-from-unicode-exploits-to-new-bypass-techniques-f73f343f05d8
Threat actors have claimed responsibility for a data breach involving Heineken employees. The news broke through a post on the social media platform tweeted by the account DarkWebInformer:
https://gbhackers.com/threat-actors-claiming-breach/
An ex-employee has alleged that Amazon breached UK sanctions by providing Moscow with its facial recognition technology after Russia’s full-scale invasion of Ukraine.:
https://www.ft.com/content/f28377a1-432b-4f29-8544-e5ec7ac1cab9
Two weeks ahead of Recall’s launch on new Copilot+ PCs on June 18, security researchers have demonstrated how preview versions of the tool store the screenshots in an unencrypted database. The researchers say the data could quickly be hoovered up by an attacker. And now, in a warning about how Recall could be abused by criminal hackers, Alex Hagenah, a cybersecurity strategist and ethical hacker, has released a demo tool that can automatically extract and display everything Recall records on a laptop:
https://www.wired.com/story/total-recall-windows-recall-ai/
The tool is called TotalRecall:
https://github.com/xaitax/TotalRecall
Microsoft rolls back ‘dumbest cybersecurity move in a decade’:
https://cyberscoop.com/microsoft-rolls-back-dumbest-cybersecurity-move-in-a-decade/
Tenable Research discovered a vulnerability in Azure (customer action required). The vulnerability allows a malicious attacker to bypass firewall rules based on Azure Service Tags by forging requests from trusted services. A threat actor could exploit Service Tags that have been allowed through a user's firewall if there are no additional validation controls:
https://www.tenable.com/security/research/tra-2024-19
Cox Communications has fixed an authorisation bypass vulnerability that enabled remote attackers to abuse exposed backend APIs to reset millions of Cox-supplied modems' settings and steal customers' sensitive personal information:
https://www.bleepingcomputer.com/news/security/cox-fixed-an-api-auth-bypass-exposing-millions-of-modems-to-attacks/
Hacktivists are conducting DDoS attacks on European political parties that represent and promote strategies opposing their interests, according to a report by Cloudflare:
https://www.bleepingcomputer.com/news/security/ddos-attacks-target-eu-political-parties-as-elections-begin/
A threat actor known as “8220 Gang” is seen exploiting two vulnerabilities in the Oracle WebLogic server: CVE-2017-3506, which allows remote OS command execution, and CVE-2023-21839 is an insecure deserialisation vulnerability. CISA recently added the Oracle WebLogic flaw tracked as CVE-2017-3506 to its known exploited vulnerabilities catalogue on 3 June 2023:
https://fortiguard.fortinet.com/threat-signal-report/5466
London Hospitals Face Major Disruptions After Cyberattack A system used by several major London hospitals was targeted in a ransomware cyberattack, forcing the cancellation of services and the diversion of patients:
https://www.nytimes.com/2024/06/05/world/europe/london-hospitals-cyberattack.html
Microsoft has announced the gradual phasing out of all versions of NTLM (NT LAN Manager). This decision is part of Microsoft’s ongoing efforts to harden Windows against various security threats and vulnerabilities:
https://cybersecuritynews.com/microsoft-to-disable-ntlm/
Canadian Cyber Centre warns of PRC cyber operations targeting multiple sectors, issues proactive security measures:
https://industrialcyber.co/critical-infrastructure/canadian-cyber-centre-warns-of-prc-cyber-operations-targeting-multiple-sectors-issues-proactive-security-measures/
A critical zero-day vulnerability, CVE-2024-24919, has been discovered in Check Point Security Gateways, enabling the IPSec VPN or Mobile Access blades. This vulnerability is actively exploited in the wild, posing a significant threat to organisations worldwide:
https://cybersecuritynews.com/vulnerable-to-0-day-attacks/
North Korean Kimsuky APT has been actively exploiting Facebook and MS Console for targeted attacks. Facebook and MS Console are often targeted by hackers, as they contain a lot of personal and sensitive data that can be used for identity theft, phishing, and other harmful activities:
https://cybersecuritynews.com/kimsuky-apt-facebook-ms-console/
Microsoft Azure SQL Managed Instance Documentation SAS Token Incorrect Permission Assignment Authentication Bypass Vulnerability:
https://www.zerodayinitiative.com/advisories/ZDI-24-581/
Internal source code and data belonging to The New York Times was leaked on the 4chan message board after being stolen from the company's GitHub repositories in January 2024, The Times confirmed to BleepingComputer. As first seen by VX-Underground, the internal data was leaked on Thursday by an anonymous user who posted a torrent to a 273GB archive containing the stolen data:
https://www.bleepingcomputer.com/news/security/new-york-times-source-code-stolen-using-exposed-github-token/
CVE-2024-4577 - Yet Another PHP RCE: Make PHP-CGI Argument Injection:
https://blog.orange.tw/2024/06/cve-2024-4577-yet-another-php-rce.html

Critical RCE Vulnerability (CVE-2024-4577) in PHP on Windows: Patch Now Available - SOCRadar® Cyber Intelligence Inc.
A remote code execution (RCE) vulnerability in PHP has been discovered by DEVCORE during their continuous offensive research. Due to the widespread use of PHP
GitHub - xcanwin/CVE-2024-4577-PHP-RCE: 全球首款利用PHP默认环境的CVE-2024-4577 PHP-CGI RCE 漏洞 EXP,共享原创EXP,支持SSRF,支持绕过WAF。The world's first CVE-2024-4577 PHP-CGI RCE exploit utilizing the default PHP environment. Sharing original exploit, supports SSRF, supports WAF bypass.
全球首款利用PHP默认环境的CVE-2024-4577 PHP-CGI RCE 漏洞 EXP,共享原创EXP,支持SSRF,支持绕过WAF。The world's first CVE-2024-4577 PHP-CGI RCE exploit utilizing the default PHP environment. Sharing original exploit, suppor...
Universal local privilege escalation Proof-of-Concept exploit for CVE-2024-1086, working on most Linux kernels between v5.14 and v6.6, including Debian, Ubuntu, and KernelCTF. The success rate is 99.4% in KernelCTF images:
https://github.com/Notselwyn/CVE-2024-1086
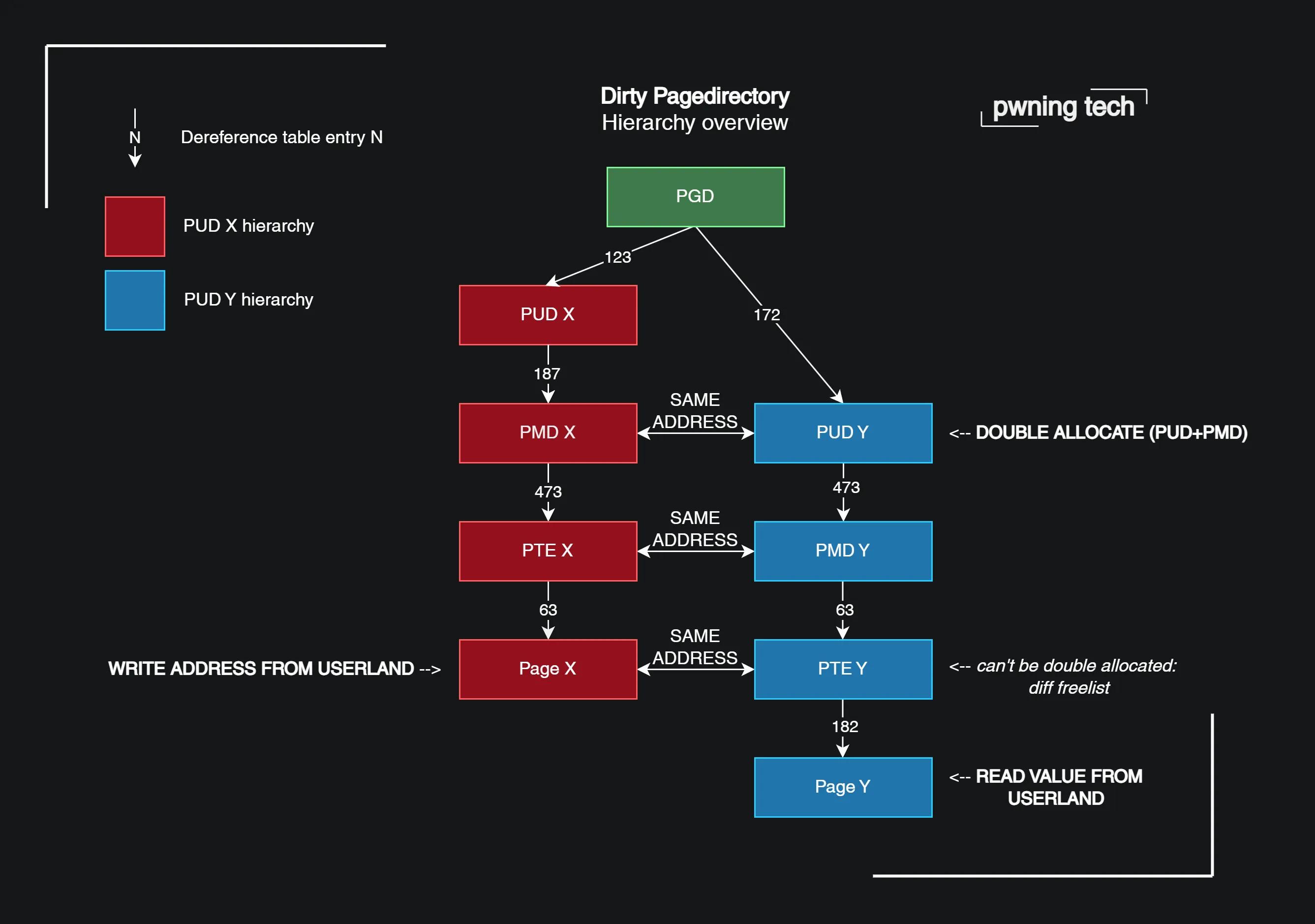
Flipping Pages: An analysis of a new Linux vulnerability in nf_tables and hardened exploitation techniques
A tale about exploiting KernelCTF Mitigation, Debian, and Ubuntu instances with a double-free in nf_tables in the Linux kernel, using novel techniques like Dirty Pagedirectory. All without even having to recompile the exploit for different kernel targets once.
Exploiting XXE Vulnerabilities on Microsoft SharePoint Server and Cloud via Confused URL Parsing:
https://github.com/W01fh4cker/CVE-2024-30043-XXE
After Snowflake, Hugging Face reports a security breach. Hugging Face has advised its community members to refresh access tokens or switch to safer ones to protect against the attack:
https://www.csoonline.com/article/2137564/after-snowflake-hugging-face-reports-security-breach.html
Organisations in the manufacturing, construction, and education sectors across South Korea have been targeted by North Korean state-sponsored advanced persistent threat operation and Lazarus Group sub-cluster Andariel, also known as Silent Chollima, Nickel Hyatt, and Onyx Sleet, in attacks spreading the novel Dora RAT malware with reverse shell and file upload and download support:
https://www.scmagazine.com/brief/intrusions-with-novel-dora-rat-backdoor-deployed-by-andariel
IcedID Brings ScreenConnect and CSharp Streamer to ALPHV Ransomware Deployment:
https://thedfirreport.com/2024/06/10/icedid-brings-screenconnect-and-csharp-streamer-to-alphv-ransomware-deployment/
A financially motivated hacker claims to have stolen over 34 gigabytes of data belonging to Singapore-based Telecom company Absolute Telecom PTE Ltd:
https://www.govinfosecurity.com/hackers-claim-they-breached-telecom-firm-in-singapore-a-25461
Russian state-backed threat operation APT28 deployed attacks with the Headlace information-stealing malware and credential-harvesting sites — also known as Fancy Bear, Sednit, BlueDelta, Sofacy Group, STRONTIUM, and Pawn Storm — against European networks as part of multi-stage espionage campaign between April and December:
https://www.scmagazine.com/brief/europe-subjected-to-multi-phase-apt28-cyberespionage-attacks
On 20 March 2024, Progress disclosed three vulnerabilities in the Progress Telerik Reporting and Progress Telerik Report Server (CVE-2024-1800, CVE-2024-1801 and CVE-2024-1856). Another vulnerability (CVE-2024-4358) was disclosed later on 31 May 2024, which also affects the Progress Telerik Report Server:
https://cert.be/en/advisory/warning-critical-and-high-vulnerabilities-progress-telerik-can-be-exploited-execute-code
A group of Israeli researchers explored the security of the Visual Studio Code marketplace and managed to "infect" over 100 organisations by trojanizing a copy of the famous 'Dracula Official theme to include risky code. Further research into the VSCode Marketplace found thousands of extensions with millions of installs:
https://www.bleepingcomputer.com/news/security/malicious-visual-studio-code-extensions-with-millions-of-installs-discovered/
Telegram Combolists and 361M Email Addresses: It contains 1.7k files with 2B lines and 361M unique email addresses, of which 151M had never been seen before. Alongside those addresses were passwords and, in many cases, the website the data pertains to:
https://www.troyhunt.com/telegram-combolists-and-361m-email-addresses/
Researchers observed a new Linux variant of the TargetCompany ransomware family that targets VMware ESXi environments using a custom shell script to deliver and execute payloads:
https://www.bleepingcomputer.com/news/security/linux-version-of-targetcompany-ransomware-focuses-on-vmware-esxi/
GoldPickaxe iOS Malware Harvests Facial Recognition Data & Bank Accounts:
https://gbhackers.com/goldpickaxe-ios-malware/
Cisco has disclosed a significant security vulnerability in its Webex Meetings platform that allowed unauthorised access to meeting information and metadata:
https://cybersecuritynews.com/cisco-webex-meetings-vulnerability/
Since March 2024, the BI.ZONE Threat Intelligence team has been tracking the cluster of activity dubbed Sapphire Werewolf. The threat actor targets Russia’s industries: education, manufacturing, IT, defence, and aerospace engineering. Over 300 attacks were carried out using Amethyst, an offshoot of the popular open-source SapphireStealer:
https://www.infostealers.com/article/sapphire-werewolf-polishes-amethyst-stealer-to-attack-over-300-companies/
Christie's starts notifying clients of RansomHub data breach:
https://www.bleepingcomputer.com/news/security/christies-starts-notifying-clients-of-ransomhub-data-breach/
Pandabuy was extorted twice by the same threat actor:
https://securityaffairs.com/164263/cyber-crime/pandabuy-extorted-again.html
A new vulnerability has been found in the EmailGPT service, a Google Chrome extension and API service that utilises OpenAI’s GPT models to assist users in writing emails within Gmail:
https://www.infosecurity-magazine.com/news/emailgpt-exposed-prompt-injection/
CodeVeil: A Python-powered obfuscation tool transcending PowerShell to cloak scripts in mystery. Elevate security testing with advanced evasion techniques for diverse languages:
https://github.com/trojansteve/CodeVeil